5 Ways to Fight School Ransomware Attacks
Dark Reading
MARCH 16, 2023
The challenges are steep, but school districts can fight back with planning.

Dark Reading
MARCH 16, 2023
The challenges are steep, but school districts can fight back with planning.

Schneier on Security
MARCH 14, 2023
By Nathan E. Sanders & Bruce Schneier Nearly 90% of the multibillion-dollar federal lobbying apparatus in the United States serves corporate interests. In some cases, the objective of that money is obvious. Google pours millions into lobbying on bills related to antitrust regulation. Big energy companies expect action whenever there is a move to end drilling leases for federal lands, in exchange for the tens of millions they contribute to congressional reelection campaigns.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
MARCH 17, 2023
The U.S. Federal Bureau of Investigation (FBI) this week arrested a New York man on suspicion of running BreachForums , a popular English-language cybercrime forum where some of the world biggest hacked databases routinely show up for sale. The forum’s administrator “ Pompompurin ” has been a thorn in the side of the FBI for years, and BreachForums is widely considered a reincarnation of RaidForums , a remarkably similar crime forum that the FBI infiltrated and dismantled in 20

Tech Republic Security
MARCH 15, 2023
AI-generated phishing emails, including ones created by ChatGPT, present a potential new threat for security professionals, says Hoxhunt. The post Humans are still better at creating phishing emails than AI — for now appeared first on TechRepublic.

Speaker: William Hord, Senior VP of Risk & Professional Services
Enterprise Risk Management (ERM) is critical for industry growth in today’s fast-paced and ever-changing risk landscape. When building your ERM program foundation, you need to answer questions like: Do we have robust board and management support? Do we understand and articulate our bank’s risk appetite and how that impacts our business units? How are we measuring and rating our risk impact, likelihood, and controls to mitigate our risk?

Security Boulevard
MARCH 13, 2023
Be careful what you wish for: Biden wants new regulations for cloud providers—but we’re not sure it’ll help. The post White House to Regulate Cloud Security: Good Luck With That appeared first on Security Boulevard.

Schneier on Security
MARCH 14, 2023
From Brian Krebs : A Croatian national has been arrested for allegedly operating NetWire, a Remote Access Trojan (RAT) marketed on cybercrime forums since 2012 as a stealthy way to spy on infected systems and siphon passwords. The arrest coincided with a seizure of the NetWire sales website by the U.S. Federal Bureau of Investigation (FBI). While the defendant in this case hasn’t yet been named publicly, the NetWire website has been leaking information about the likely true identity and lo
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
MARCH 17, 2023
Some 12% of employees take customer details, health records, sales contracts and other confidential data when leaving a company, according to DTEX. The post How to prevent data theft by existing and departing employees appeared first on TechRepublic.

CSO Magazine
MARCH 13, 2023
Phishing attempts are typically like fishing in a barrel — given enough time, a bad actor is 100% likely to reel in a victim. Once they recognize organizations as habitually vulnerable, they will continue to target them and the barrel-fishing cycle goes on and on. “Bad actors are highly motivated and funded with the sole attempt to be successful at attracting only one victim,” says Johanna Baum, CEO and founder of Strategic Security Solutions Consulting.

Schneier on Security
MARCH 14, 2023
This is a current list of where and when I am scheduled to speak: I’m speaking on “ How to Reclaim Power in the Digital World ” at EPFL in Lausanne, Switzerland, on Thursday, March 16, 2023, at 5:30 PM CET. I’ll be discussing my new book A Hacker’s Mind: How the Powerful Bend Society’s Rules at Harvard Science Center in Cambridge, Massachusetts, USA, on Friday, March 31, 2023 at 6:00 PM EDT.

Krebs on Security
MARCH 15, 2023
Microsoft on Tuesday released updates to quash at least 74 security bugs in its Windows operating systems and software. Two of those flaws are already being actively attacked, including an especially severe weakness in Microsoft Outlook that can be exploited without any user interaction. The Outlook vulnerability ( CVE-2023-23397 ) affects all versions of Microsoft Outlook from 2013 to the newest.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.

Tech Republic Security
MARCH 13, 2023
A new malware dubbed HiatusRAT infects routers to spy on its targets, mostly in Europe and in the U.S. Learn which router models are primarily targeted and how to protect from this security threat. The post New Hiatus malware campaign targets routers appeared first on TechRepublic.

Security Boulevard
MARCH 16, 2023
Ben is disappointed: FBI reports huge rise in cryptocurrency investment scams. Why am I not surprised? The post Scams Lost US $10 BILLION in 2022 — Crypto Fraud Grows Fast appeared first on Security Boulevard.

Dark Reading
MARCH 15, 2023
Over the weekend, cybercriminals laid the groundwork for Silicon Valley Bank-related fraud attacks that they're now starting to cash in on. Businesses are the targets and, sometimes, the enablers.

CyberSecurity Insiders
MARCH 17, 2023
After Rubrik, Hitachi Energy issued a public statement that some of its customer accounts might have been compromised, after a ransomware attack took place on a third-party software called Fortra GoAnywhere MFT. Clop ransomware gang is the company that managed to infiltrate the servers and siphon data and a portion of employee data might have been compromised.

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
So, you’ve accomplished an organization-wide SaaS adoption. It started slow, and now just a few team members might be responsible for running Salesforce, Slack, and a few others applications that boost productivity, but it’s all finished. Or is it? Through all the benefits offered by SaaS applications, it’s still a necessity to onboard providers as quickly as possible.

Tech Republic Security
MARCH 13, 2023
By exploiting webcams and other IoT devices, hackers can spy on private and professional conversations, potentially giving them access to sensitive information, says BitSight. The post How internet-facing webcams could put your organization at risk appeared first on TechRepublic.

CSO Magazine
MARCH 14, 2023
During every quarter last year, between 10% and 16% of organizations had DNS traffic originating on their networks towards command-and-control (C2) servers associated with known botnets and various other malware threats, according to a report from cloud and content delivery network provider Akamai. More than a quarter of that traffic went to servers belonging to initial access brokers, attackers who sell access into corporate networks to other cybercriminals, the report stated.

Dark Reading
MARCH 14, 2023
One researcher thinks trust is broken in AD. Microsoft disagrees that there's a security vulnerability. But enterprise IT environments should be aware of an authentication gap either way.

Graham Cluley
MARCH 17, 2023
Well, this isn’t good. Google has issued a warning that some Android phones can be hacked remotely, without the intended victim having to click on anything.

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Did you know that 2021 was a record-breaking year for ransomware? The days of a “once in a while” attack against businesses and organizations are over. Cyberthreats have become a serious issue. With 495.1 million attacks, the threat marked a 148% increase compared to 2020 and was the most expensive year on record! As a result, data protection needs to be a concern for most banks, businesses, and information technology specialists.

Tech Republic Security
MARCH 14, 2023
A possible Chinese attack campaign on compromised unpatched SonicWall SMA edge devices stayed undetected since 2021 and could persist even through firmware updates. The post Attack campaign on edge appliance: undetected since 2021 and resists firmware update appeared first on TechRepublic.

The Hacker News
MARCH 17, 2023
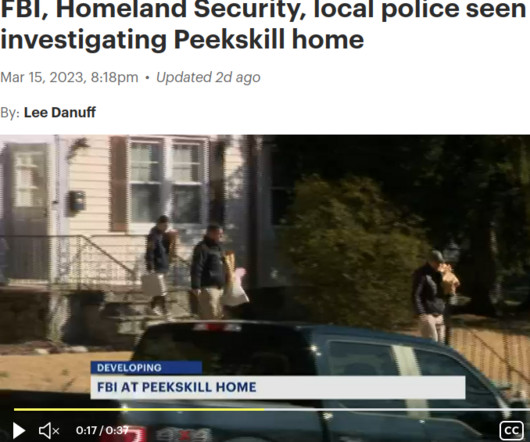
U.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums hacking forum under the online alias "Pompompurin." The development, first reported by Bloomberg Law, comes after News 12 Westchester, earlier this week, said that federal investigators "spent hours inside and outside of a home in Peekskill.

We Live Security
MARCH 14, 2023
ESET Research uncovered a campaign by APT group Tick against a data-loss prevention company in East Asia and found a previously unreported tool used by the group The post The slow Tick‑ing time bomb: Tick APT group compromise of a DLP software developer in East Asia appeared first on WeLiveSecurity

Security Boulevard
MARCH 14, 2023
Growing interconnectedness makes it harder to detect ransomware before it causes harm. Whether data is processed locally or in the cloud, the risk of a breach is the same. But edge computing also makes it easier for hackers to break in because sensitive data is stored and processed on a wider range of systems. As. The post Using AI Cybersecurity Solutions to Stop Ransomware appeared first on Security Boulevard.

Speaker: Dr. Karen Hardy, CEO and Chief Risk Officer of Strategic Leadership Advisors LLC
Communication is a core component of a resilient organization's risk management framework. However, risk communication involves more than just reporting information and populating dashboards, and we may be limiting our skillset. Storytelling is the ability to express ideas and convey messages to others, including stakeholders. When done effectively, it can help interpret complex risk environments for leaders and inform their decision-making.

Tech Republic Security
MARCH 15, 2023
With backing from major firms, credential security company Beyond Identity has launched the Zero Trust Authentication initiative for organizations to hack-proof user credentials. The post For credentials, these are the new Seven Commandments for zero trust appeared first on TechRepublic.

CSO Magazine
MARCH 16, 2023
Single Sign-On (SSO) providers like Okta protect businesses by combining all company-approved sites and services in a single dashboard. Employees can then use a single, strongly vetted identity to log in to those sites and services using a single set of credentials. It's better for security, and easier for employees. Now, 1Password Business customers can access 1Password with their Okta credentials, too.

Dark Reading
MARCH 16, 2023
The ransomware group has already claimed 116 victim organizations so far on its site, and it continues to mature as a thriving cybercriminal business, researchers said.

Bleeping Computer
MARCH 17, 2023
The NBA (National Basketball Association) is notifying fans of a data breach after some of their personal information, "held" by a third-party newsletter service, was stolen. [.

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
PCI compliance can feel challenging and sometimes the result feels like you are optimizing more for security and compliance than you are for business outcomes. The key is to take the right strategy to PCI compliance that gets you both. In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization.

Tech Republic Security
MARCH 14, 2023
The Premium Ethical Hacking Certification Bundle features eight courses that introduce students to the fundamentals and prepare them to earn important credentials from CompTIA. The post Learn the basics of cybersecurity with this $60 web-based training package appeared first on TechRepublic.
Security Boulevard
MARCH 17, 2023
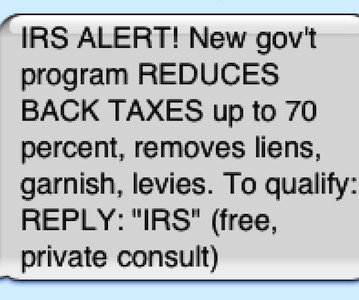
Federal Communications Commission rules to block illegal text messages. What took you so long? The post FINALLY! FCC Acts on SMS Scam-Spam — But Will It Work? appeared first on Security Boulevard.

CSO Magazine
MARCH 17, 2023
Microsoft released its monthly security bulletin this week, covering patches for over 80 vulnerabilities across its products. However, two of them had already been used by attackers before patches were released. One vulnerability affects all supported versions of Outlook for Windows and allows attackers to steal Net-NTLMv2 hashes and then use them in NTLM (New Technology LAN Manager) relay attacks against other systems.

Thales Cloud Protection & Licensing
MARCH 13, 2023
Key Points from the US National Cybersecurity Strategy 2023 divya Mon, 03/13/2023 - 15:39 On March 2, the Biden administration released its 2023 National Cybersecurity Strategy, an attempt “ to secure the full benefits of a safe and secure digital ecosystem for all Americans.” The Strategy recognizes that the US government must use all tools of national power in a coordinated manner to protect national security, public safety, and economic prosperity.

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
The COVID-19 pandemic forced many people into working remotely, opening the floodgates for a host of digital compliance issues. Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. This is especially vital if your workers were (and still are!) using company equipment from home, or are still working remotely.

Let's personalize your content