How to easily encrypt/decrypt a file in Linux with gpg
Tech Republic Security
MAY 4, 2016
Stop your search for an easy way to encrypt and decrypt files in Linux -- the built-in gpg tool will do the trick.

Tech Republic Security
MAY 4, 2016
Stop your search for an easy way to encrypt and decrypt files in Linux -- the built-in gpg tool will do the trick.

ForAllSecure
MAY 24, 2016
Aside from our cool research , ForAllSecure also works on creating fun and engaging games to promote computer security. Just about every employee in our company has been involved in Capture the Flag exercises for the past several years, and we have been hosting these online events for our customers for about 3 years now. One of our big dreams is to see these types of contests gain in popularity, similar to how e-sports grew.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
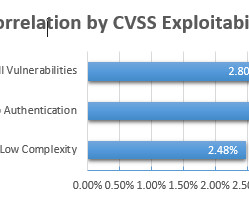
NopSec
MAY 17, 2016
Note: This article was updated in June 2022. Here at NopSec, we are all about risk — our number one goal as a company to help organizations evaluate and reduce their risk. However, the term “risk” can be highly subjective, making it difficult for organizations to determine the riskiest vulnerabilities. One quantitative measure NopSec employs to help an organization evaluate the risk of a vulnerability is through malware correlation.

Privacy and Cybersecurity Law
MAY 27, 2016
Today, the Office of the Privacy Commissioner (OPC) announced its report of findings against Compu-Finder, a Quebec-based company that offers […].

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Tech Republic Security
MAY 16, 2016
Armies around the world are gearing up for cyberwarfare: here's what it is and what you need to know.

Tech Republic Security
MAY 31, 2016
Microsoft is partnering with ConsenSys and Blockstack Labs to build an open source, blockchain-based identity system to help provide legal identification for people around the world.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
MAY 11, 2016
Eight universities have begun a year-long initiative to train IBM Watson for work in cybersecurity. Will the Jeopardy champ soon police the internet?

Tech Republic Security
MAY 6, 2016
The Computer Science Teachers Association (CTSA) is working on a cybersecurity certification program for computer science educators, so they can better teach students about computer security.

Tech Republic Security
MAY 24, 2016
A recent security report from CompTIA found that while threats are growing stronger, many enterprises still aren't ready to face them.

Tech Republic Security
MAY 5, 2016
The LAPD recently hacked into an iPhone 5s involved in a very public murder trial. This news could prove a potential roadblock for backdoor legislation.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
MAY 10, 2016
Think your Amazon Echo or Samsung Smart TV are IoT security threats? Businesses using the 'industrial internet of things' are even bigger targets for cyberattacks.

Tech Republic Security
MAY 31, 2016
NTechLab's facial recognition app uses AI to identify a face among billions of photos in less than a second, and is one of the best in the world, but the Russian startup draws concerns from academics.

Tech Republic Security
MAY 26, 2016
IT risk assessments are crucial to minimize the fallout from cyberattacks. Experts explain why and suggest what questions to consider to assess your company's risk.

Tech Republic Security
MAY 26, 2016
Apple devices aren't impervious to threats against your data. Here are 5 more methods for keeping your information safe.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
MAY 17, 2016
Experts offer five scenarios they suspect will wreak havoc on cybersecurity by 2020.

Tech Republic Security
MAY 24, 2016
Researchers look at what it means when cyberweapons have the same status as traditional weapons of war.

Tech Republic Security
MAY 16, 2016
HPE's new Business of Hacking report takes a look at the underground world of criminal hackers and what steps businesses can take to stay secure.

Tech Republic Security
MAY 11, 2016
By definition, marketing is all about getting people to do something. Make sure the "doing something" is your decision and not the marketers'.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Tech Republic Security
MAY 19, 2016
Read about the potential devastating effects of business ID theft, and what steps experts are taking to address this issue.

Tech Republic Security
MAY 31, 2016
Israeli researchers recently found a slew of security flaws in the Samsung Knox security system commonly used in Android phones.

Tech Republic Security
MAY 9, 2016
Lack of existing case law may fuel legal battles in which companies in the IoT market will have the most to lose.

Tech Republic Security
MAY 5, 2016
Developers would often rather write apps than secure them, but public cloud providers can help them do both.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
MAY 16, 2016
If you're serious about security on your Linux machines, you might want to clear the bash history. Learn how to do this more effectively than with just a single command.

Tech Republic Security
MAY 10, 2016
The Android Security Update for May 2016 includes a number of critical issues. Jack Wallen has the highlights, and shows how to find out if your device is up to date.

Tech Republic Security
MAY 3, 2016
The popular image processing library ImageMagick has a number of critical vulnerabilities currently being used in the wild, allowing attackers to gain control of servers.

Tech Republic Security
MAY 12, 2016
For an easy-to-use password manager for the Ubuntu Touch platform, Jack Wallen recommends the no-frills app password-shroud.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

NopSec
MAY 9, 2016
Compliance isn’t enough for healthcare organizations. For years, we have equated compliance with effective vulnerability risk management. This is simply not the case. Recent highly publicized data breaches in major hospitals show that minimum compliance is not effective when protecting your data. In fact, it’s not just major healthcare organizations that get attacked, but virtually all hospitals have been victims of a cyber attack (commonly ransomware) at some point in varying degrees.

NopSec
MAY 2, 2016
Most small and medium business owners believe that cyber criminals only target large businesses and corporations. They couldn’t be more wrong. In 2015, 62% of all data breaches were against SMBs according to IBM and the Ponemon Institute. Considering that a majority of business entities in the United States are small and medium businesses, and most of them do not have robust information security programs in place, there is definitely an incentive in targeting SMBs instead.

ForAllSecure
MAY 24, 2016
Aside from our cool research , ForAllSecure also works on creating fun and engaging games to promote computer security. Just about every employee in our company has been involved in Capture the Flag exercises for the past several years, and we have been hosting these online events for our customers for about 3 years now. One of our big dreams is to see these types of contests gain in popularity, similar to how e-sports grew.

ForAllSecure
MAY 24, 2016
Aside from our cool research , ForAllSecure also works on creating fun and engaging games to promote computer security. Just about every employee in our company has been involved in Capture the Flag exercises for the past several years, and we have been hosting these online events for our customers for about 3 years now. One of our big dreams is to see these types of contests gain in popularity, similar to how e-sports grew.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
Let's personalize your content