New Privacy Features in iOS 14
Schneier on Security
OCTOBER 7, 2020
A good rundown.

Krebs on Security
OCTOBER 1, 2020
Companies victimized by ransomware and firms that facilitate negotiations with ransomware extortionists could face steep fines from the U.S. federal government if the crooks who profit from the attack are already under economic sanctions, the Treasury Department warned today. Image: Shutterstock. In its advisory (PDF), the Treasury’s Office of Foreign Assets Control (OFAC) said “companies that facilitate ransomware payments to cyber actors on behalf of victims, including financial in
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Troy Hunt
OCTOBER 2, 2020
Sexuality, relationships and online dating are all rather personal things. They're aspects of our lives that many people choose to keep private or at the very least, share only with people of our choosing. Grindr is "The World's Largest Social Networking App for Gay, Bi, Trans, and Queer People" which for many people, makes it particularly sensitive.

Adam Levin
OCTOBER 16, 2020
Barnes & Noble has confirmed a data breach following a cyberattack that took many of their services offline. . The bookseller sent an email to customers notifying them that their personal information had been exposed, but that their financial information had not been compromised. . “While we do not know if any personal information was exposed as a result of the attack, we do retain in the impacted systems your billing and shipping addresses, your email address and your telephone number if yo

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Adam Shostack
OCTOBER 31, 2020
With three days to the US election, the outrage machines are running on all cylinders. It’ll be easier to stay happy if you remember to notice them. To be clear, I’m not using a metaphor. Websites from news to social media use data to drive stories. Twitter’s top tweets, Facebook’s timeline, your local newspaper, but also Linkedin, Medium, Buzzfeed, – all are focused on keeping you on their site as long as possible to show you as many ads as possible.
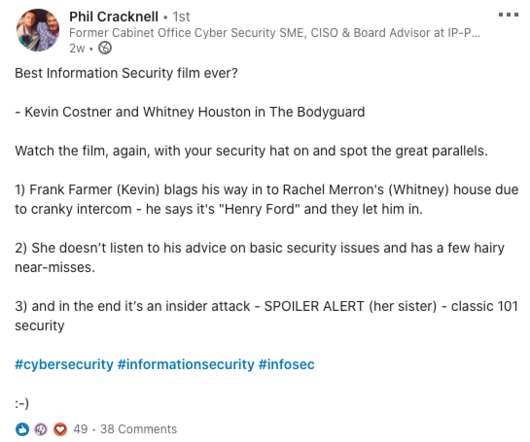
Javvad Malik
OCTOBER 29, 2020
There’s often a lot of debate as to what the best security or hacking movie is. Many people talk about Hackers, or Sneakers, or try and slip Mr Robot into the mix. But they are all way way waaaaay off the mark. I was reminded of this by Phil Cracknell who posted on linkedin that in his opinion the Kevin Costner, Whitney Houston classic, Bodyguard was the best infosec movie.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
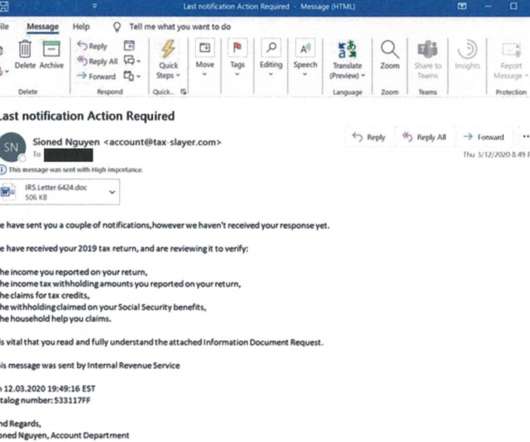
Krebs on Security
OCTOBER 12, 2020
Microsoft Corp. has executed a coordinated legal sneak attack in a bid to disrupt the malware-as-a-service botnet Trickbot , a global menace that has infected millions of computers and is used to spread ransomware. A court in Virginia granted Microsoft control over many Internet servers Trickbot uses to plunder infected systems, based on novel claims that the crime machine abused the software giant’s trademarks.
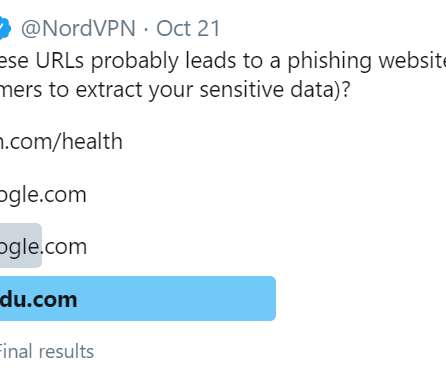
Troy Hunt
OCTOBER 28, 2020
Been a lot of "victim blaming" going on these last few days. The victim, through no fault of their own, has been the target of numerous angry tweets designed to ridicule their role in internet security and suggest they are incapable of performing their duty. Here's where it all started: This is a great example of how bad people are at reading and understanding even the domain part of the URL then making decisions based on that which affect their security and privacy (see the answer under the pol

The Last Watchdog
OCTOBER 19, 2020
There is no shortage of innovative cybersecurity tools and services that can help companies do a much better job of defending their networks. Related: Welcome to the CyberXchange Marketplace In the U.S. alone, in fact, there are more than 5,000 cybersecurity vendors. For organizations looking to improve their security posture, this is causing confusion and vendor fatigue, especially for companies that don’t have a full time Chief Information Security Officer.
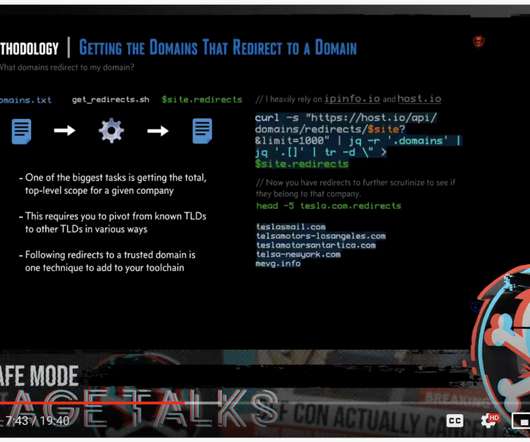
Daniel Miessler
OCTOBER 28, 2020
I have an unpopular opinion about the security conference scene. Basically, it’s the opposite of what John Strand said here: Can we all agree that pre-recorded Conference talks are horrible? I mean… Why? — strandjs (@strandjs) October 28, 2020. I see this sentiment a lot from a lot of people in infosec, and I think I’ve figured it out.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
OCTOBER 29, 2020
One policy expert says cybersecurity measures should be an expected item that comes with every purchase, like the safety measures in your car.
Schneier on Security
OCTOBER 13, 2020
One of the things we learned from the Snowden documents is that the NSA conducts “about” searches. That is, searches based on activities and not identifiers. A normal search would be on a name, or IP address, or phone number. An about search would something like “show me anyone that has used this particular name in a communications,” or “show me anyone who was at this particular location within this time frame.” These searches are legal when conducted for the

Krebs on Security
OCTOBER 15, 2020
One of the digital underground’s most popular stores for peddling stolen credit card information began selling a batch of more than three million new card records this week. KrebsOnSecurity has learned the data was stolen in a lengthy data breach at more than 100 Dickey’s Barbeque Restaurant locations around the country. An ad on the popular carding site Joker’s Stash for “BlazingSun,” which fraud experts have traced back to a card breach at Dickey’s BBQ.

Troy Hunt
OCTOBER 15, 2020
You know how some people are what you'd call "house proud" in that they like everything very neat and organised? You walk in there and everything is in its place, nice and clean without clutter. I'm what you'd call "network proud" and the same principle applies to how I manage my IP things: That's just a slice of my Ubiquiti network map which presently has 91 IP addresses on it between clients and network devices.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Adam Levin
OCTOBER 13, 2020
Microsoft has stepped up its efforts to disrupt the Trickbot malware botnet after receiving permission to take on its network infrastructure. Citing concerns of potential activity to disrupt the upcoming elections, Microsoft was granted approval from the U.S. District Court for the Eastern District of Virginia to disable online servers connected to the botnet. .

Security Affairs
OCTOBER 30, 2020
Google researchers disclosed today a zero-day vulnerability in the Windows operating system that is currently under active exploitation. Security researchers from Google have disclosed a zero-day vulnerability in the Windows operating system, tracked as CVE-2020-17087, that is currently under active exploitation. Ben Hawkes, team lead for Google Project Zero team, revealed on Twitter that the vulnerability was chained with another Chrome zero-day flaw, tracked as CVE-2020-15999 , that Google re

Tech Republic Security
OCTOBER 28, 2020
Wandera finds malicious network traffic and configuration vulnerabilities on mobile devices as popular entry points for cybercriminals.

Schneier on Security
OCTOBER 27, 2020
Slate magazine was able to cleverly read the Ghislaine Maxwell deposition and reverse-engineer many of the redacted names. We’ve long known that redacting is hard in the modern age, but most of the failures to date have been a result of not realizing that covering digital text with a black bar doesn’t always remove the text from the underlying digital file.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Krebs on Security
OCTOBER 9, 2020
A week ago, KrebsOnSecurity broke the news that someone was attempting to disrupt the Trickbot botnet , a malware crime machine that has infected millions of computers and is often used to spread ransomware. A new report Friday says the coordinated attack was part of an operation carried out by the U.S. military’s Cyber Command. Image: Shuttstock.

Troy Hunt
OCTOBER 29, 2020
Almost a decade ago now, I wrote what would become one of my most career-defining blog posts: The Only Secure Password is the One You Can't Remember. I had come to the realisation that I simply had too many accounts across too many systems to ever have any chance of creating decent unique passwords I could remember. So, I set out to find a password manager and 10 Christmas holidays ago now, I spent the best 50 bucks ever: I choose 1Password way back then and without a shadow of a doubt, it has b

Adam Levin
OCTOBER 2, 2020
Facebook has announced that it will place greater restrictions on advertisements for social and political issues ahead of the upcoming U.S. presidential election. The company announced the new restrictions on its corporate blog earlier this week, which prohibit the following content: Ads discouraging participation in the voting process. Ads seeking to delegitimize lawful voting practices as fraudulent, illegal, or corrupt.

Security Affairs
OCTOBER 29, 2020
FBI and the DHS’s CISA agencies published a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia. The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) has issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
OCTOBER 19, 2020
Ransomware has evolved into a significant threat for all types of organizations. How and why is it such a pervasive issue, and how can organizations better defend themselves against it?

Schneier on Security
OCTOBER 6, 2020
Previously I have written about the Swedish-owned Swiss-based cryptographic hardware company: Crypto AG. It was a CIA-owned Cold War operation for decades. Today it is called Crypto International , still based in Switzerland but owned by a Swedish company. It’s back in the news : Late last week, Swedish Foreign Minister Ann Linde said she had canceled a meeting with her Swiss counterpart Ignazio Cassis slated for this month after Switzerland placed an export ban on Crypto International , a

Krebs on Security
OCTOBER 28, 2020
In March 2020, KrebsOnSecurity alerted Swedish security giant Gunnebo Group that hackers had broken into its network and sold the access to a criminal group which specializes in deploying ransomware. In August, Gunnebo said it had successfully thwarted a ransomware attack, but this week it emerged that the intruders stole and published online tens of thousands of sensitive documents — including schematics of client bank vaults and surveillance systems.

Troy Hunt
OCTOBER 2, 2020
This week there's a lot of connected things: connected shoes, connected garage camera and connected GoPro. And then there's Scott's Grindr account. Awkward. Actually, since recording this weekly update the details of the issue have now been released so I'll talk about that in more detail next week. This week there's all the above and, on a more personal note, my relationship with Charlotte.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
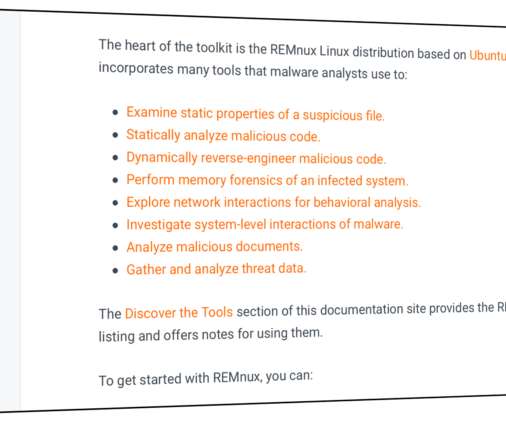
Lenny Zeltser
OCTOBER 13, 2020
REMnux ® offers a curated collection of free tools for reverse-engineering or otherwise analyzing malicious software. How to find the right tool for the job, given how many useful utilities come as part of the distro? To guide you through the process of examining malware, REMnux documentation lists the installed tools by category. Each grouping, which you’ll find in the Discover the Tools section of the documentation site, represents the type of actions the analysts might need to take: Exa
Security Affairs
OCTOBER 31, 2020
The REvil ransomware operators made the headlines again, this time the gang claims to have hacked the Gaming Partners International (GPI). Gaming Partners International (GPI) is a full-service supplier of gaming furniture and equipment for casinos worldwide. The REvil ransomware gang (aka Sodinokibi) claims to have stolen info from the systems at the company before encrypting them.

Tech Republic Security
OCTOBER 8, 2020
The goal is to not only secure your remote devices and endpoints but to make that security part of your overall strategy, says NordVPN Teams.
Schneier on Security
OCTOBER 19, 2020
Researchers are tricking autopilots by inserting split-second images into roadside billboards. Researchers at Israel’s Ben Gurion University of the Negev … previously revealed that they could use split-second light projections on roads to successfully trick Tesla’s driver-assistance systems into automatically stopping without warning when its camera sees spoofed images of road signs or pedestrians.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
Let's personalize your content