How could the FBI recover BTC from Colonial’s ransomware payment?
Naked Security
JUNE 9, 2021
But Bitcoins are anonymous! However could they get refunded? Cryptocurrency Cryptography Law & order bitcoin BTC Colonial Darkside FBI
Naked Security
JUNE 9, 2021
But Bitcoins are anonymous! However could they get refunded? Cryptocurrency Cryptography Law & order bitcoin BTC Colonial Darkside FBI
InfoWorld on Security
JUNE 11, 2021
In the latest Agents of Transformation report, Agents of Transformation 2021: The Rise of Full-Stack Observability , 77% of global technicians report experiencing a higher level of complexity as a result of accelerated cloud computing initiatives during the pandemic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
We Live Security
JUNE 30, 2021
Are you on Facebook? So are scammers. Here are some of the most common con jobs on Facebook you should watch out for and how you can tell if you’re being scammed. The post Common Facebook scams and how to avoid them appeared first on WeLiveSecurity. Scams
DoublePulsar
JUNE 8, 2021
I’ve talked about ransomware and extortion attacks on organizations for about a decade. I recently spent a year at Microsoft in Threat… Continue reading on DoublePulsar ». ransomware

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance
SecureList
JUNE 23, 2021
Introduction. Nowadays, cybersecurity companies implement a variety of methods to discover new, previously unknown malware files. Machine learning (ML) is a powerful and widely used approach for this task.
Troy Hunt
JUNE 9, 2021
I've had a couple of cases to date where email addresses compromised by malware then discovered in the course of investigations have been provided to Have I Been Pwned (HIBP).
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Schneier on Security
JUNE 8, 2021
“If you think any of these systems are going to work as expected in wartime, you’re fooling yourself.” ” That was Bruce’s response at a conference hosted by U.S.

Adam Levin
JUNE 4, 2021
You would think that ExaGrid, a backup appliance and anti-ransomware service might know how to avoid ransomware, but it was hit. .
Lohrman on Security
JUNE 13, 2021
After the recent ransomware attacks against Colonial Pipeline, JBS and others, there are new calls for the U.S. to hack back against cybercrimminals and hold nation-states responsible. So what now?

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
Troy Hunt
JUNE 14, 2021
Today I'm very happy to welcome the Finnish government to Have I Been Pwned by granting their National Cyber Security Centre full and free access to query their government domains.

Joseph Steinberg
JUNE 7, 2021
Every so often, I encounter an unusual technology device that so well solves a problem that I have encountered many times that I cannot imagine not adding the product to my arsenal of tools, even if it is not something that I would necessarily use every day. The Hushme is one such offering.

Schneier on Security
JUNE 14, 2021
This is probably worth paying attention to: A change to TikTok’s U.S. privacy policy on Wednesday introduced a new section that says the social video app “may collect biometric identifiers and biometric information” from its users’ content.
Adam Shostack
JUNE 1, 2021
People sometimes ask me about my recording setup, and I wanted to share some thoughts about recording good learning content. The most important thing I’ve learned is the importance of conceptualizing what you want it to look like.
Krebs on Security
JUNE 16, 2021
Authorities in Ukraine this week charged six people alleged to be part of the CLOP ransomware group , a cybercriminal gang said to have extorted more than half a billion dollars from victims.
Lohrman on Security
JUNE 20, 2021
The North Atlantic Treaty Organization (NATO) opened the door for cyber attacks to trigger “Article 5” actions. This is a big deal — here’s why
Troy Hunt
JUNE 5, 2021
This week has been absolutely dominated by code contributions to Pwned Passwords. This is such an awesome, humbling experience that so many people have wanted to contribute their time to something that makes online life better for all of us.
Joseph Steinberg
JUNE 3, 2021
Joseph Steinberg recently discussed with Fox Business Network host and commentator, Kennedy, why hackers are targeting meat companies, pipelines, and other important elements of the US economy’s supply chain… and, what can Americans do to stop such attacks.
Schneier on Security
JUNE 17, 2021
General Packet Radio Service (GPRS) is a mobile data standard that was widely used in the early 2000s. The first encryption algorithm for that standard was GEA-1, a stream cipher built on three linear-feedback shift registers and a non-linear combining function.

The Last Watchdog
JUNE 1, 2021
Cybercriminals use various techniques for conducting cyberattacks. One such popular way to infiltrate a system is Pharming. It is an online scam attack quite similar to Phishing. Related: Credential stuffing explained. The term Pharming is a combination of two words Phishing and Farming. It is a type of social engineering cyberattack in which the website’s traffic is manipulated to steal confidential credentials from the users.
Krebs on Security
JUNE 15, 2021
The U.S. Department of Justice (DOJ) last week announced the arrest of a 55-year-old Latvian woman who’s alleged to have worked as a programmer for Trickbot , a malware-as-a-service platform responsible for infecting millions of computers and seeding many of those systems with ransomware.
Doctor Chaos
JUNE 15, 2021
Unaddressed cybersecurity threats can cause lost profits, regulatory fines and missed opportunities. Plus, as company leaders scramble to recover from attacks, making progress often takes weeks or months, severely disrupting business operations.
Troy Hunt
JUNE 8, 2021
Ever notice how there was a massive gap of almost 9 months between announcing the intention to start open sourcing Have I Been Pwned (HIBP) in August last year and then finally a couple of weeks ago, actually taking the first step with Pwned Passwords ?
Joseph Steinberg
JUNE 1, 2021
Cybercriminals Are Impersonating Meal-Kit Services In Order To Steal Money And Personal Information.
Schneier on Security
JUNE 24, 2021
The Norwegian Consumer Council just published a fantastic new report: “ Time to Ban Surveillance-Based Advertising.

The Last Watchdog
JUNE 28, 2021
Microsoft has blunted the ongoing activities of the Nobelium hacking collective, giving us yet another glimpse of the unceasing barrage of hack attempts business networks must withstand on a daily basis. Related: Reaction to Biden ‘s cybersecurity executive order. Nobelium is the Russian hacking collective best known for pulling off the milestone SolarWinds supply chain hack last December.
Krebs on Security
JUNE 25, 2021
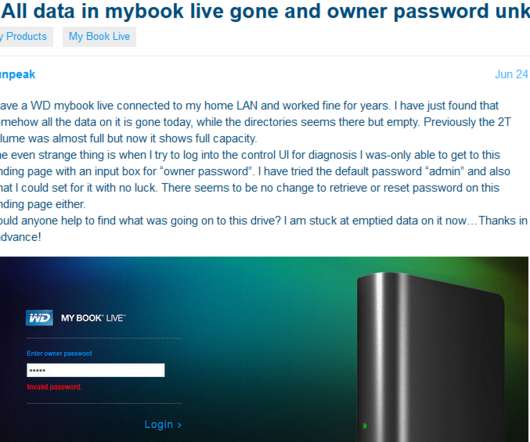
Hard drive giant Western Digital is urging users of its MyBook Live brand of network storage drives to disconnect them from the Internet, warning that malicious hackers are remotely wiping the drives using a critical flaw that can be triggered by anyone who knows the Internet address of an affected device.
Lohrman on Security
JUNE 6, 2021
Maria Thompson’s last day as North Carolina’s chief risk officer was June 4, 2021. In this interview, she shares her team’s cyber journey, along with helpful insights for others to benefit from.
Troy Hunt
JUNE 28, 2021
Today I'm very happy to welcome the 23rd national government to Have I Been Pwned, the Slovak Republic. As of now, CSIRT.sk has full and free access to query all their government domains via an API that returns all their email addresses impacted by each data breach in HIBP.
Joseph Steinberg
JUNE 23, 2021
Cyber Security Expert, Joseph Steinberg, has joined Newsweek’s Expert Forum, the premier news outlet’s invitation-only community of pioneering thinkers and industry leaders.
Schneier on Security
JUNE 16, 2021
TorrentFreak surveyed nineteen VPN providers, asking them questions about their privacy practices: what data they keep, how they respond to court order, what country they are incorporated in, and so on. Most interesting to me is the home countries of these companies.

The Last Watchdog
JUNE 9, 2021
Data leaks and data theft are part and parcel of digital commerce, even more so in the era of agile software development. Related: GraphQL APIs stir new exposures. Many of the high-profile breaches making headlines today are the by-product of hackers pounding away at Application Programming Interfaces (APIs) until they find a crease that gets them into the pathways of the data flowing between an individual user and myriad cloud-based resources.
Krebs on Security
JUNE 23, 2021
In 2015, police departments worldwide started finding ATMs compromised with advanced new “shimming” devices made to steal data from chip card transactions.
Adam Shostack
JUNE 28, 2021
At Blackhat USA, I’ll be teaching Applied Threat Modeling. This hands-on, interactive class will focus on learning to threat model by executing each of the steps.
Troy Hunt
JUNE 3, 2021
Supporting national CERTs with free API domain searches across their assets is becoming an increasing focus for Have I Been Pwned and today I'm happy to welcome the 19th government on board, Belgium.
Let's personalize your content