On Passkey Usability
Schneier on Security
FEBRUARY 12, 2024
Matt Burgess tries to only use passkeys. The results are mixed.

Schneier on Security
FEBRUARY 12, 2024
Matt Burgess tries to only use passkeys. The results are mixed.

Tech Republic Security
FEBRUARY 12, 2024
Google Cloud’s Director of Office of the CISO Nick Godfrey reminds business leaders to integrate security into conversations around financial and business targets.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Hacker News
FEBRUARY 12, 2024
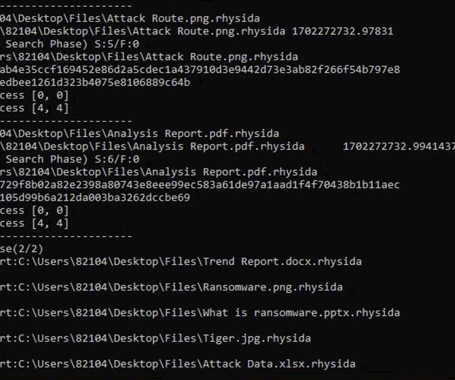
Cybersecurity researchers have uncovered an "implementation vulnerability" that has made it possible to reconstruct encryption keys and decrypt data locked by Rhysida ransomware. The findings were published last week by a group of researchers from Kookmin University and the Korea Internet and Security Agency (KISA).

Tech Republic Security
FEBRUARY 12, 2024
Read our comprehensive review of Perimeter 81 VPN. Discover its features, pricing, security measures and more to determine if it's the right VPN for you.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Malwarebytes
FEBRUARY 12, 2024
The Federal Communications Commission (FCC) has announced that calls made with voices generated with the help of Artificial Intelligence (AI) will be considered “artificial” under the Telephone Consumer Protection Act (TCPA). Effective immediately, that makes robocalls that implement voice cloning technology and target consumers illegal. Robocalls are automated phone calls, often associated with scams, which can be a nuisance to individuals and businesses alike.
Security Affairs
FEBRUARY 12, 2024
Exploring the Risks: Unveiling 9 Potential Techniques Hackers Employ to Exploit Public Wi-Fi and Compromise Your Sensitive Data We’ve all used public Wi-Fi: it’s convenient, saves our data, and speeds up browsing. But while we enjoy its benefits, hackers do too. Here, we’ll explore how cybercriminals exploit public Wi-Fi to access your private data and possibly steal your identity.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
FEBRUARY 12, 2024
Threat actors are leveraging a recently disclosed security flaw impacting Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy a backdoor codenamed DSLog on susceptible devices. That's according to findings from Orange Cyberdefense, which said it observed the exploitation of CVE-2024-21893 within hours of the public release of the proof-the-concept (PoC) code.

Bleeping Computer
FEBRUARY 12, 2024
Bank of America is warning customers of a data breach exposing their personal information after one of its service providers was hacked last year. [.

The Hacker News
FEBRUARY 12, 2024
When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple work for hackers, MFA provides an essential layer of protection against breaches. However, it's important to remember that MFA isn't foolproof. It can be bypassed, and it often is.

Security Affairs
FEBRUARY 12, 2024
A bug in the split tunneling feature implemented in ExpressVPN exposed the domains visited by the users. ExpressVPN addressed a bug in the split tunneling feature that exposed the domains visited by the users to configured DNS servers. The company opted to temporarily remove the feature in the Windows app to address the issue. The bug will be enabled in a future release when the company will fix it.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

The Hacker News
FEBRUARY 12, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a medium-severity security flaw impacting Roundcube email software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The issue, tracked as CVE-2023-43770 (CVSS score: 6.

Security Affairs
FEBRUARY 12, 2024
The Canadian government is going to ban the tool Flipper Zero because it is abused by crooks to steal vehicles in the country. The Canadian government announced that it plans to ban the tool Flipper Zero , and similar hacking devices, to curb the surge in car thefts. Flipper Zero is a portable multi-tool for pentesters and geeks in a toy-like body. It allows hacking digital stuff, such as radio protocols, access control systems, hardware, and more, reads the official website.

The Hacker News
FEBRUARY 12, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that it's partnering with the Open Source Security Foundation (OpenSSF) Securing Software Repositories Working Group to publish a new framework to secure package repositories.

WIRED Threat Level
FEBRUARY 12, 2024
Top congressional lawmakers are meeting in private to discuss the future of a widely unpopular surveillance program, worrying members devoted to reforming Section 702.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Security Affairs
FEBRUARY 12, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Roundcube Webmail Persistent Cross-Site Scripting (XSS) Vulnerability to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a Roundcube Webmail Persistent Cross-Site Scripting (XSS) vulnerability, tracked as CVE-2023-43770 , to its Known Exploited Vulnerabilities (KEV) catalog.

WIRED Threat Level
FEBRUARY 12, 2024
Cyberattacks and criminal scams can impact anyone. But communities of color and other marginalized groups are often disproportionately impacted and lack the support to better protect themselves.
Security Affairs
FEBRUARY 12, 2024
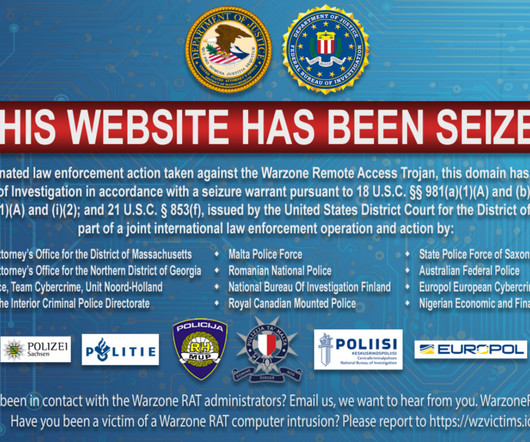
The U.S. Justice Department (DoJ) seized the infrastructure that was used to sell the remote access trojan (RAT) Warzone RAT. The Justice Department announced the seizure of internet domains used to sell the remote access Trojan Warzone RAT (www.warzone[.]ws). The seizure is the result of an international law enforcement operation, federal authorities in Atlanta and Boston charged individuals in Malta and Nigeria, for their involvement in selling the malware.

The Hacker News
FEBRUARY 12, 2024
Incident response (IR) is a race against time. You engage your internal or external team because there's enough evidence that something bad is happening, but you’re still blind to the scope, the impact, and the root cause. The common set of IR tools and practices provides IR teams with the ability to discover malicious files and outbound network connections.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.
Security Affairs
FEBRUARY 12, 2024
Researchers discovered a vulnerability in the code of the Rhysida ransomware that allowed them to develop a decryption tool. Cybersecurity researchers from Kookmin University and the Korea Internet and Security Agency (KISA) discovered an implementation vulnerability in the source code of the Rhysida ransomware. The experts exploited the vulnerability to reconstruct encryption keys and developed a decryptor that allows victims of the Rhysida ransomware to recover their encrypted data for free. &

Malwarebytes
FEBRUARY 12, 2024
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.

Security Affairs
FEBRUARY 12, 2024
Residential Proxies vs. Datacenter Proxies: this blog post examines the contours of each type and provides info on how to choose the perfect proxy option In the robust landscape of the digital era, our need for privacy, security, and accessibility on the internet has never been more acute. Whether it’s for gathering market intelligence, ensuring your privacy, or bypassing geographical restrictions, proxies have become the unsung heroes for individuals and enterprises alike.

Bleeping Computer
FEBRUARY 12, 2024
Hackers are exploiting a server-side request forgery (SSRF) vulnerability in Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy the new DSLog backdoor on vulnerable devices. [.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Security Boulevard
FEBRUARY 12, 2024
When sensitive information becomes available to outside sources, you have a data leak on your hands. Data leaks are real threats that are easy to ignore. But across all the places your company stores and moves data, it’s only a matter of time until an accidental exposure of information will put your business at risk. […] The post What is a Data Leak?

Trend Micro
FEBRUARY 12, 2024
This entry aims to provide additional context to CVE-2024-21412, how it can be used by threat actors, and how Trend protects customers from this specific vulnerability.

Bleeping Computer
FEBRUARY 12, 2024
At least 18 hospitals in Romania were knocked offline after a ransomware attack took down their healthcare management system. [.

Graham Cluley
FEBRUARY 12, 2024
Over 20 hospitals in Bucharest have reportedly been impacted by a ransomware attack after cybercriminals targeted an IT service provider. As a consequence medical staff have been forced to use pen-and-paper rather than computer systems.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

WIRED Threat Level
FEBRUARY 12, 2024
“This eruption of violence had been brewing for years, through successive economic collapses, pandemics, and the utter dysfunction that had become American life.” An exclusive excerpt from 2054: A Novel.

Graham Cluley
FEBRUARY 12, 2024
A simple-to-avoid security flaw allowed unauthorised parties to track the location of anyone wearing Livall ski and biking helmets, and listen to group conversations. Read more in my article on the Hot for Security blog.
Malwarebytes
FEBRUARY 12, 2024
Last week on Malwarebytes Labs: Ivanti urges customers to patch yet another critical vulnerability Ransomware in 2023 recap: 5 key takeaways FBI and CISA publish guide to Living off the Land techniques Warning from LastPass as fake app found on Apple App Store 2 million job seekers targeted by data thieves How to tell if your toothbrush is being used in a DDoS attack Facebook fatal accident scam still rages on State of Malware 2024: What consumers need to know Known ransomware attacks up 68% in

Security Boulevard
FEBRUARY 12, 2024
Ah, Valentine's Day—the time when love is in the air, and scam artists are ready to swoop in with their own version of a love story. Imagine this: you're swiping through a dating app, hoping to find the yin to your yang, only to find yourself entangled in a web of deception. The post A Valentine’s warning about heartbreak hackers appeared first on Security Boulevard.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content