Voice Cloning with Very Short Samples
Schneier on Security
JANUARY 15, 2024
New research demonstrates voice cloning, in multiple languages, using samples ranging from one to twelve seconds. Research paper.

Schneier on Security
JANUARY 15, 2024
New research demonstrates voice cloning, in multiple languages, using samples ranging from one to twelve seconds. Research paper.

Troy Hunt
JANUARY 15, 2024
Geez it's nice to be back in Oslo! This city has such a special place in my heart for so many reasons, not least of which by virtue of being Charlotte's home town we have so many friends and family here. Add in NDC Security this week with so many more mutual connections, beautiful snowy weather, snowboarding, sledging and even curling, it's just an awesome time.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JANUARY 15, 2024
Researchers from Bishop Fox found over 178,000 SonicWall next-generation firewalls (NGFW) publicly exploitable. SonicWall next-generation firewall (NGFW) series 6 and 7 devices are affected by two unauthenticated denial-of-service vulnerabilities, tracked as CVE-2022-22274 and CVE-2023-0656 , that could potentially lead to remote code execution. Despite a proof-of-concept exploit for the flaw CVE-2023-0656 was publicly released, the vendor is not aware of attack in the wild exploiting the vulner

Graham Cluley
JANUARY 15, 2024
A WordPress plugin used on over 300,000 websites has been found to contain vulnerabilities that could allow hackers to seize control. Security researchers at Wordfence found two critical flaws in the POST SMTP Mailer plugin. Read more in my article on the Tripwire State of Security blog.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
JANUARY 15, 2024
Adblock and Adblock Plus users report performance issues on YouTube, initially blamed on Google but later determined to be an issue in the popular ad-blocking extension. [.

Security Affairs
JANUARY 15, 2024
Researchers warn of high-severity vulnerability affecting Bosch BCC100 thermostats. Researchers from Bitdefender discovered a high-severity vulnerability affecting Bosch BCC100 thermostats. The researchers discovered a vulnerability, tracked as CVE-2023-49722 (CVSS score: 8.3), that can be exploited by an attacker on the same network to replace the device firmware with a rogue version.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Affairs
JANUARY 15, 2024
Balada Injector malware infected more than 7100 WordPress sites using a vulnerable version of the Popup Builder plugin. In September, Sucuri researchers reported that more than 17,000 WordPress websites had been compromised in September with the Balada Injector. The researchers noticed that the number of Balada Injector infections has doubled compared with August 2023.

Security Boulevard
JANUARY 15, 2024
Mark Rasch examines 2023 cybercrime cases that appear to be the most impactful—not the most extensive or expensive—just the most “interesting.” The post Stupid Human Tricks: Top 10 Cybercrime Cases of 2023 appeared first on Security Boulevard.
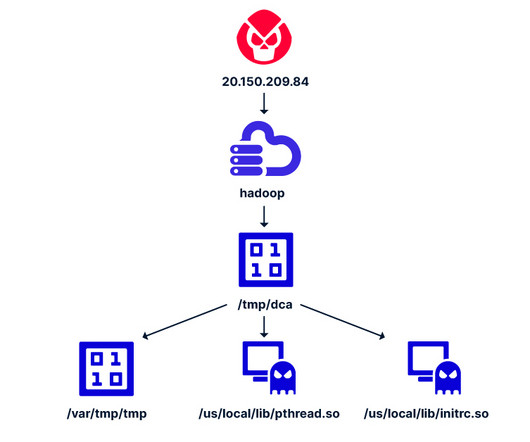
Security Affairs
JANUARY 15, 2024
Researchers devised a new attack that exploits misconfigurations in Apache Hadoop and Flink to deploy cryptocurrency miners. Cybersecurity researchers from cyber security firm Aqua have uncovered a new attack targeting Apache Hadoop and Flink applications. The attacks exploit misconfigurations in Apache Hadoop and Flink to deploy cryptocurrency cryptocurrency miners.

Bleeping Computer
JANUARY 15, 2024
A Phemedrone information-stealing malware campaign exploits a Microsoft Defender SmartScreen vulnerability (CVE-2023-36025) to bypass Windows security prompts when opening URL files. [.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Security Affairs
JANUARY 15, 2024
Threat actors exploit a recent Windows SmartScreen bypass flaw CVE-2023-36025 to deliver the Phemedrone info stealer. Trend Micro researchers uncovered a malware campaign exploiting the vulnerability CVE-2023-36025 (CVSS score 8.8) to deploy a previously unknown strain of the malware dubbed Phemedrone Stealer. The vulnerability was addressed by Microsoft with the release of Patch Tuesday security updates for November 2023.

Bleeping Computer
JANUARY 15, 2024
Microsoft is working to fix a known issue causing 0x80070643 errors when installing the KB5034441 security update that patches the CVE-2024-20666 BitLocker vulnerability. [.

Security Boulevard
JANUARY 15, 2024
The last couple of years have seen a wave of state privacy law proposals across the United States. As of 2018, only California had passed a comprehensive privacy law. By late 2022, the federal government and 29 states were playing the game, with even more getting in line. Among this deluge of legislation and bills […] The post New Jersey Privacy Act: What to Expect appeared first on Centraleyes.

Bleeping Computer
JANUARY 15, 2024
Security researchers have found over 178,000 SonicWall next-generation firewalls (NGFW) with the management interface exposed online are vulnerable to denial-of-service (DoS) and potential remote code execution (RCE) attacks. [.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Security Boulevard
JANUARY 15, 2024
In the dynamic realm of cybersecurity, staying ahead of potential threats is crucial for maintaining a secure computing environment. For Debian GNU/Linux users, keeping the system updated with the latest security patches is an essential step towards fortifying your digital fortress. These updates address several security vulnerabilities to enhance the overall system security.

Bleeping Computer
JANUARY 15, 2024
Microsoft says that tests of a controversial new Windows 11 feature that automatically opens the AI-powered Copilot assistant after Windows starts are limited to systems with 27-inch displays. [.

Penetration Testing
JANUARY 15, 2024
apk2url apk2url easily extracts URL and IP endpoints from an APK file to a.txt output. This is suitable for information gathering by the red team, penetration testers, and developers to quickly identify endpoints... The post apk2url: quickly extract IP and URL endpoints from APKs appeared first on Penetration Testing.

Malwarebytes
JANUARY 15, 2024
In November 2023, real estate services company Fidelity National Financial (FNF) got its systems knocked offline for a week after a cyberincident. As is often the case these days, it turns out that the cyberincident was very likely a ransomware attack that included a data breach. Ransomware operators typically steal data from the compromised systems to use as extra leverage against the victim.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Penetration Testing
JANUARY 15, 2024
LinikatzV2 LinikatzV2 is a bash script based on the Linikatz tool developed by a time machine. It allows post-exploitation tasks on UNIX computers joined to Active Directory, using various methods for credential mining. This... The post LinikatzV2: A tool to attack Active Directory on UNIX appeared first on Penetration Testing.

The Hacker News
JANUARY 15, 2024
Cybersecurity researchers have disclosed a security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be exploited to execute any file on the underlying operating system.

Penetration Testing
JANUARY 15, 2024
A new security vulnerability was found in the GRUB boot manager, CVE-2023-4001. This vulnerability, rated at a concerning 5.6 on the Common Vulnerability Scoring System (CVSS), presents a unique challenge in the realm of... The post Bypassing GRUB Security: How CVE-2023-4001 Exploits UEFI Systems appeared first on Penetration Testing.

Bleeping Computer
JANUARY 15, 2024
Two zero-day vulnerabilities affecting Ivanti's Connect Secure VPN and Policy Secure network access control (NAC) appliances are now under mass exploitation. [.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

The Hacker News
JANUARY 15, 2024
Threat actors have been observed leveraging a now-patched security flaw in Microsoft Windows to deploy an open-source information stealer called Phemedrone Stealer. “Phemedrone targets web browsers and data from cryptocurrency wallets and messaging apps such as Telegram, Steam, and Discord,” Trend Micro researchers Peter Girnus, Aliakbar Zahravi, and Simon Zuckerbraun said.

Bleeping Computer
JANUARY 15, 2024
In a seizure warrant application, the U.S. Secret Service sheds light on how threat actors stole $34,000 using fake antivirus renewal subscription emails. [.

Penetration Testing
JANUARY 15, 2024
In the landscape of cybersecurity, the energy sector remains a critical area vulnerable to sophisticated cyberattacks. Forescout Vedere Labs’ recent threat briefing sheds light on two distinct cyberattacks targeting this sector in Denmark and... The post Unmasking Sandworm: Forescout’s Analysis of Danish and Ukrainian Energy Cyberattacks appeared first on Penetration Testing.

The Hacker News
JANUARY 15, 2024
Multiple security vulnerabilities have been disclosed in Bosch BCC100 thermostats and Rexroth NXA015S-36V-B smart nutrunners that, if successfully exploited, could allow attackers to execute arbitrary code on affected systems.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.

Penetration Testing
JANUARY 15, 2024
In the realm of cybersecurity, the rise of sophisticated infostealers targeting macOS has emerged as a significant threat. These advanced malware variants, like KeySteal, Atomic InfoStealer, and CherryPie, are adept at evading detection and... The post The Silent Threat: Unmasking Undetected macOS InfoStealers appeared first on Penetration Testing.
Malwarebytes
JANUARY 15, 2024
Last week on Malwarebytes Labs: FCC wants cars to make life harder for stalkers Joomla! vulnerability is being actively exploited Act now! Ivanti vulnerabilities are being actively exploited Ransomware review: January 2024 Info-stealers can steal cookies for permanent access to your Google account Atomic Stealer rings in the new year with updated version Patch now!

The Hacker News
JANUARY 15, 2024
The operators behind the now-defunct Inferno Drainer created more than 16,000 unique malicious domains over a span of one year between 2022 and 2023.

Security Boulevard
JANUARY 15, 2024
Cloud operations involves more than technology; it's about a culture that values agility, flexibility and continuous improvement. The post Embedding Security Into Cloud Operations: 5 Key Considerations appeared first on Security Boulevard.

Advertisement
Leverage the Cloud Development Environment Maturity Model to elevate your software development practices with scalable, secure cloud-based workspaces. This model offers a structured approach to modernizing development, aligning technology, developer experience, security, and workflows. By implementing Cloud Development Environments (CDEs), teams can boost efficiency, improve security, and streamline operations through centralized governance.
Let's personalize your content