Data Exfiltration Using Indirect Prompt Injection
Schneier on Security
DECEMBER 22, 2023
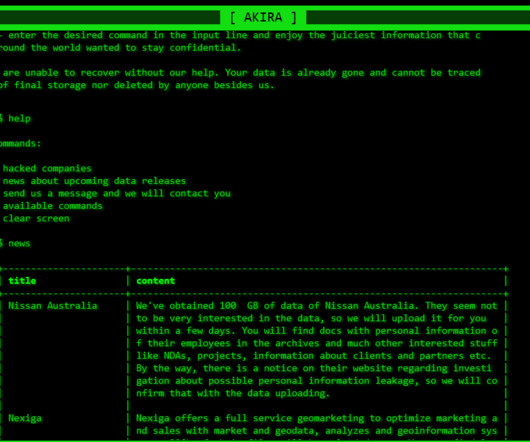
Interesting attack on a LLM: In Writer, users can enter a ChatGPT-like session to edit or create their documents. In this chat session, the LLM can retrieve information from sources on the web to assist users in creation of their documents. We show that attackers can prepare websites that, when a user adds them as a source, manipulate the LLM into sending private information to the attacker or perform other malicious activities.











































Let's personalize your content