Where Next for Real ID, Facial Recognition and Airport Security?
Lohrman on Security
SEPTEMBER 22, 2024
There have been some new updates around airport security and identification. Here’s what you need to know.

Lohrman on Security
SEPTEMBER 22, 2024
There have been some new updates around airport security and identification. Here’s what you need to know.
Penetration Testing
SEPTEMBER 22, 2024
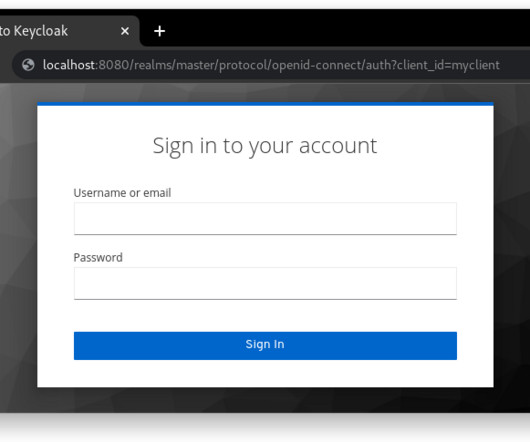
In a concerning development for organizations relying on Keycloak for secure identity and access management, a high-severity vulnerability has been discovered in its SAML signature validation process. Tracked as CVE-2024-8698,... The post CVE-2024-8698: Keycloak Vulnerability Puts SAML Authentication at Risk appeared first on Cybersecurity News.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
SEPTEMBER 22, 2024
Hacktivist group Twelve is back and targets Russian entities to destroy critical assets and disrupt their operations. The hacktivist group Twelve has been active since at least April 2023, it was formed in the wake of the conflict between Russia and Ukraine. The threat actor focuses on destroying critical assets, disrupting target business, and stealing sensitive data.

The Hacker News
SEPTEMBER 22, 2024
Threat actors with ties to North Korea have been observed using poisoned Python packages as a way to deliver a new malware called PondRAT as part of an ongoing campaign.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
SEPTEMBER 22, 2024
GreyNoise Intelligence firm warns of a mysterious phenomenon observed since January 2020, massive waves of spoofed traffic called Noise Storms. GreyNoise Intelligence has been tracking a mysterious phenomenon since January 2020 consisting of massive waves of spoofed traffic, tracked by the experts as ‘Noise Storms.’ Despite the investigation into the traffic, the company has yet to understand which is the reason behind these storms.

The Hacker News
SEPTEMBER 22, 2024
A suspected advanced persistent threat (APT) originating from China targeted a government organization in Taiwan, and possibly other countries in the Asia-Pacific (APAC) region, by exploiting a recently patched critical security flaw impacting OSGeo GeoServer GeoTools.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Penetration Testing
SEPTEMBER 22, 2024
A recently disclosed security advisory has unveiled a critical vulnerability affecting FreeBSD’s bhyve hypervisor. Identified as CVE-2024-41721, this flaw carries a CVSS score of 9.8, reflecting its high severity. The... The post FreeBSD Issues Critical Security Advisory for CVE-2024-41721 (CVSS 9.8) appeared first on Cybersecurity News.

Zero Day
SEPTEMBER 22, 2024
This lifetime license bundle deal gives you access to the entire Microsoft Office Pro 2021 suite and Windows 11 Pro for just $55 for a limited time.

Penetration Testing
SEPTEMBER 22, 2024
In a concerning development for Grafana users, a critical security vulnerability has been discovered in the Grafana Plugin SDK for Go. Tracked as CVE-2024-8986 and assigned a CVSS score of... The post CVE-2024-8986 (CVSS 9.1): Critical Grafana Plugin SDK Flaw Exposes Sensitive Information appeared first on Cybersecurity News.

Security Boulevard
SEPTEMBER 22, 2024
Authors/Presenters:Zili Zhang, Chao Jin, Xin Jin Our sincere thanks to USENIX , and the Presenters & Authors for publishing their superb 21st USENIX Symposium on Networked Systems Design and Implementation (NSDI '24) content, placing the organizations enduring commitment to Open Access front and center. Originating from the conference’s events situated at the Hyatt Regency Santa Clara ; and via the organizations YouTube channel.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Penetration Testing
SEPTEMBER 22, 2024
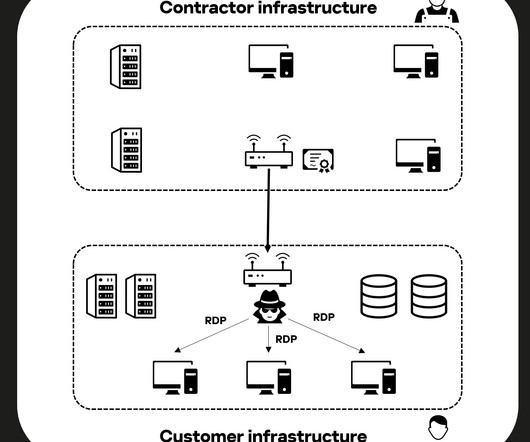
Mandiant has uncovered alarming evidence of a sophisticated Iranian state-sponsored cyber campaign orchestrated by UNC1860, a threat actor likely affiliated with Iran’s Ministry of Intelligence and Security (MOIS). Known for... The post Passive Backdoors, Active Threat: UNC1860’s Espionage Tools Exposed appeared first on Cybersecurity News.
Hacker's King
SEPTEMBER 22, 2024
In the world of cybersecurity, Telnet might seem outdated and was replaced by SSH protocol but it's still a powerful tool for penetration testers and hackers. Despite its age, this remote access protocol is valuable for network testing which allows you to connect to servers and devices. With the right techniques, ethical hackers can use Telnet to identify vulnerabilities , gather information, and launch attacks on networks—making it a valuable skill for penetration testing.
Penetration Testing
SEPTEMBER 22, 2024
The latest vulnerability disclosure identifies a significant security flaw in the Microchip Advanced Software Framework (ASF), specifically within its tinydhcp server implementation. This vulnerability, designated CVE-2024-7490, exposes IoT devices using... The post CVE-2024-7490: Urgent Warning for IoT Devices Using Microchip ASF, No Patch Available appeared first on Cybersecurity News.

Hacker's King
SEPTEMBER 22, 2024
In this article, we are going to learn Linux commands that help in blue teaming to work easily. While working as a Soc Analyst or Blue teaming you should be familiar with operating systems such as macOS , Linux , Windows. The skills of an SOC analyst without Linux knowledge may be quite inadequate as having some Linux knowledge is very important for the SOC analysts.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Penetration Testing
SEPTEMBER 22, 2024
Google security researchers recently brought attention to the lingering impact of info-stealing malware. One such threat is the RECORDSTEALER malware, also known as RecordBreaker and Raccoon Stealer V2. This info-stealer,... The post RecordStealer: A Case Study in the Persistent Threat of Info-Stealing Malware appeared first on Cybersecurity News.

Security Affairs
SEPTEMBER 22, 2024
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Hackers stole over $44 million from Asian crypto platform BingX OP KAERB: Europol dismantled phishing scheme targeting mobile users Ukraine bans Telegram for government agencies, military, and critical infrastructure Tor Project responded to claims that l

Penetration Testing
SEPTEMBER 22, 2024
Earlier reports suggested that Qualcomm, a major chip design company, has shown significant interest in Intel’s chip design division and may be considering an acquisition of Intel’s PC processor design... The post Qualcomm’s Bold Move: Intel Acquisition Bid Faces Antitrust Hurdle appeared first on Cybersecurity News.

Penetration Testing
SEPTEMBER 22, 2024
A serious security flaw has been uncovered in Dragonfly2, an open-source, peer-to-peer-based file distribution and image acceleration system. The vulnerability, CVE-2023-27584, carries a CVSS score of 9.8, reflecting its critical... The post Critical Dragonfly2 Flaw CVE-2023-27584: Hardcoded Key Threatens Admin Access appeared first on Cybersecurity News.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Penetration Testing
SEPTEMBER 22, 2024
GreyNoise Intelligence has recently released findings regarding a new and increasingly complex wave of “Noise Storms” – massive, enigmatic surges of fake traffic that have baffled experts since 2020. This... The post GreyNoise Intelligence Uncovers New Internet Noise Storm with Potential China Link and Cryptic “LOVE” Message appeared first on Cybersecurity News.

Penetration Testing
SEPTEMBER 22, 2024
Windows Server Update Services (WSUS) is a long-standing update service from Microsoft aimed at enterprises, allowing IT administrators to manage the pace of updates for internal network devices. Earlier this... The post Windows Server Update Services Deprecation: What It Means for Your Update Strategy appeared first on Cybersecurity News.
Let's personalize your content