Ransomware Remains a ‘Brutal’ Threat in 2024
Lohrman on Security
JULY 21, 2024
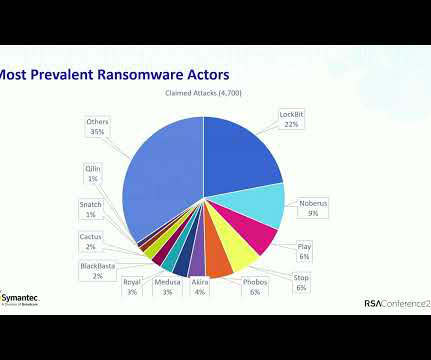
Several recently released cyber industry reports show steady or growing ransomware numbers in 2024 so far, and impacts on business and government have never been greater.
Lohrman on Security
JULY 21, 2024
Several recently released cyber industry reports show steady or growing ransomware numbers in 2024 so far, and impacts on business and government have never been greater.
Troy Hunt
JULY 21, 2024
It feels weird to be writing anything right now that isn't somehow related to Friday's CrowdStrike incident, but given I recorded this video just a few hours before all hell broke loose, it'll have to wait until next week. This week, the issue that really has me worked up is data breach victim notification or more specifically, lack thereof.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Hacker News
JULY 21, 2024
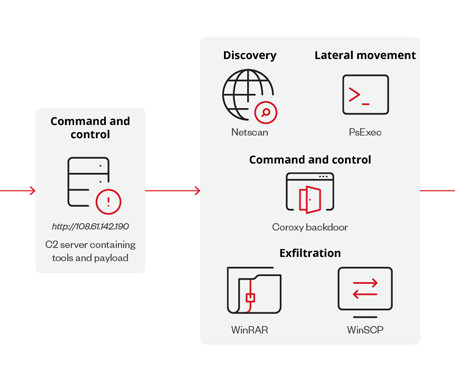
Cybersecurity researchers have discovered a new Linux variant of a ransomware strain known as Play (aka Balloonfly and PlayCrypt) that's designed to target VMWare ESXi environments.

Bleeping Computer
JULY 21, 2024
Microsoft has released a custom WinPE recovery tool to find and remove the faulty CrowdStrike update that crashed an estimated 8.5 million Windows devices on Friday. [.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.
The Hacker News
JULY 21, 2024
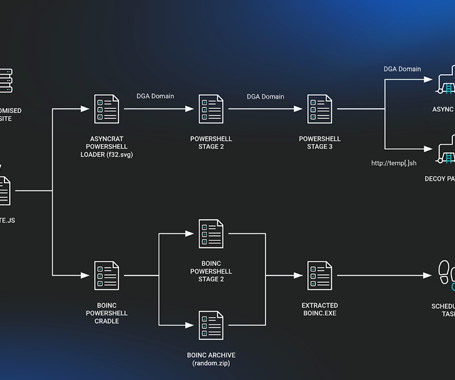
The JavaScript downloader malware known as SocGholish (aka FakeUpdates) is being used to deliver a remote access trojan called AsyncRAT as well as a legitimate open-source project called BOINC.

Bleeping Computer
JULY 21, 2024
Threat actors are exploiting the massive business disruption from CrowdStrike's glitchy update on Friday to target companies with data wipers and remote access tools. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
JULY 21, 2024
Threat actors are exploiting the massive business disruption from CrowdStrike's glitchy update on Friday to target companies with data wipers and remote access tools. [.

Security Affairs
JULY 21, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Hardening of HardBit 10,000 Victims a Day: Infostealer Garden of Low-Hanging Fruit This Meeting Should Have Been an Email Ransomware Detection Model Based on Adaptive Graph Neural Network Learning SEXi ransomware rebrands to APT INC, continues VMware ESXi attacks Facebook ads for Windows desktop themes push info-stealing malware Akira Ransomware Targets the LATAM

Trend Micro
JULY 21, 2024
Intruders are drawn to enterprise IT environments the way mice are attracted to houses. And once either kind of invader is inside, they can be hard to get out. Network detection and response (NDR) lets you trace intruders’ pathways to find out where they’re coming in—and seal the gaps.

Security Affairs
JULY 21, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Hardening of HardBit 10,000 Victims a Day: Infostealer Garden of Low-Hanging Fruit This Meeting Should Have Been an Email Ransomware Detection Model Based on Adaptive Graph Neural Network Learning SEXi ransomware rebrands to APT INC, continues VMware ESXi attacks Facebook ads for Windows desktop themes push info-stealing malware Akira Ransomware Targets the LATAM

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

We Live Security
JULY 21, 2024
Some adware is far more than an annoyance – it can expose the system to even more dangerous threats that can run code at the highest privilege level in Windows.

Security Affairs
JULY 21, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Adobe Commerce and Magento, SolarWinds Serv-U, and VMware vCenter Server bugs to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the following vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog : CVE-2024-34102 Adobe Commerce and Magento Open Source Improper Restriction of XML External Entity Reference (XXE) Vulnerability CVE-2024-28995 SolarW
Penetration Testing
JULY 21, 2024
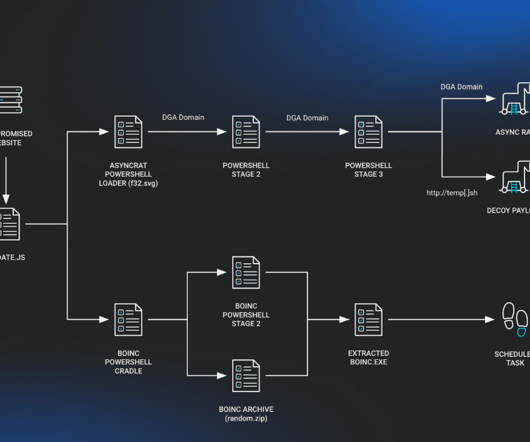
Huntress, a prominent cybersecurity firm, has recently uncovered a new wave of malicious activities involving the well-known SocGholish or FakeUpdates malware. The attackers have recently been observed leveraging the legitimate BOINC (Berkeley Open Infrastructure... The post Fake Browser Updates Lead to Malicious BOINC Installations appeared first on Cybersecurity News.

Security Boulevard
JULY 21, 2024
Authors/Presenters:Olivier Blazy, Ioana Boureanu, Pascal Lafourcade, Cristina Onete, Léo Robert Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open Access. Originating from the conference’s events situated at the Anaheim Marriott ; and via the organizations YouTube channel.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Penetration Testing
JULY 21, 2024
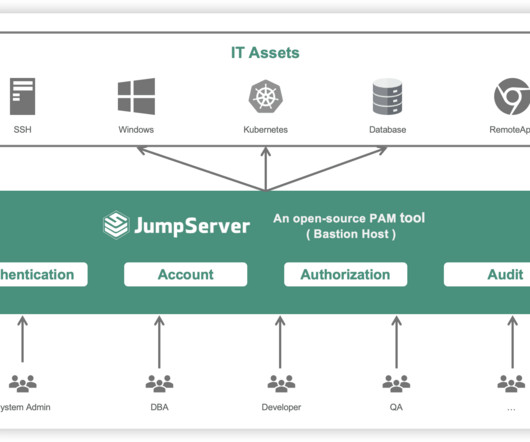
JumpServer, a widely used open-source privileged access management (PAM) tool, has disclosed two critical vulnerabilities that could allow attackers to gain unauthorized access to sensitive systems and data. The vulnerabilities, identified as CVE-2024-40628 and... The post CVE-2024-40628 & CVE-2024-40629: Two Maximum Severity Flaws in JumpServer appeared first on Cybersecurity News.

Security Affairs
JULY 21, 2024
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Threat actors attempted to capitalize CrowdStrike incident Russian nationals plead guilty to participating in the LockBit ransomware group MediSecure data breach impacted 12.9 million individuals CrowdStrike update epic fail crashed Windows systems worldw
Penetration Testing
JULY 21, 2024
In a recent series of events that disrupted major operations, the KADOKAWA Corporation experienced service outages that extended to multiple websites. What initially appeared to be a technical glitch soon escalated into a full-blown... The post BlackSuit’s Advanced Ransomware Tactics Exposed: Masquerades as Antivirus appeared first on Cybersecurity News.

Security Affairs
JULY 21, 2024
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Threat actors attempted to capitalize CrowdStrike incident Russian nationals plead guilty to participating in the LockBit ransomware group MediSecure data breach impacted 12.9 million individuals CrowdStrike update epic fail crashed Windows systems worldw

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
Penetration Testing
JULY 21, 2024
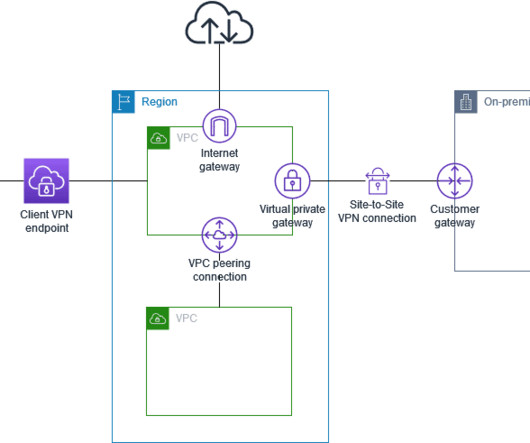
Amazon Web Services (AWS) has issued a security bulletin regarding two vulnerabilities discovered in its Client VPN service. These flaws, identified as CVE-2024-30164 and CVE-2024-30165, could potentially allow malicious actors with access to a... The post AWS Security Update: CVE-2024-30164 and CVE-2024-30165 Flaws Found in Client VPN appeared first on Cybersecurity News.

Penetration Testing
JULY 21, 2024
In the wake of a widespread system outage triggered by a faulty CrowdStrike update, cybercriminals have wasted no time exploiting the chaos. Within 24 hours of the incident, which affected millions of Windows devices... The post Cybercriminals Seize Chaos Amidst CrowdStrike Outage, Deploying Deceptive Domains appeared first on Cybersecurity News.

Penetration Testing
JULY 21, 2024
The Apache Software Foundation has issued a security advisory regarding a critical vulnerability (CVE-2024-41107) in its open-source cloud computing platform, Apache CloudStack. This flaw affects the Security Assertion Markup Language (SAML) authentication mechanism, potentially... The post CVE-2024-41107: Apache CloudStack Vulnerability Exposes User Accounts to Compromise appeared first on Cybersecurity News.

Penetration Testing
JULY 21, 2024
Issues with the software update from CrowdStrike Holdings Inc. impacted 8.5 million devices worldwide running the Microsoft Windows operating system. Representatives from Microsoft Corp. clarified that the affected devices constitute less than 1% of... The post Widespread Outage: CrowdStrike Update Affects 8.5 Million Windows Users appeared first on Cybersecurity News.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content