Microsoft is Soft-Launching Security Copilot
Schneier on Security
OCTOBER 25, 2023
Microsoft has announced an early access program for its LLM-based security chatbot assistant: Security Copilot. I am curious whether this thing is actually useful.

Schneier on Security
OCTOBER 25, 2023
Microsoft has announced an early access program for its LLM-based security chatbot assistant: Security Copilot. I am curious whether this thing is actually useful.

We Live Security
OCTOBER 25, 2023
ESET Research discover campaigns by the Winter Vivern APT group that exploit a zero-day XSS vulnerability in the Roundcube Webmail server and target governmental entities and a think tank in Europe.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
OCTOBER 25, 2023
The Pwn2Own Toronto 2023 hacking contest has begun and during the first day, participants received $438,750 in prizes! During the Day 1 of the Pwn2Own Toronto 2023 hacking contest, the organization has awarded a total of $438,750 in prizes! Team Orca of Sea Security received the greatest rewards of the day, the researchers chained two issues using an OOB Read and UAF against the Sonos Era 100.

The Hacker News
OCTOBER 25, 2023
VMware has released security updates to address a critical flaw in the vCenter Server that could result in remote code execution on affected systems. The issue, tracked as CVE-2023-34048 (CVSS score: 9.8), has been described as an out-of-bounds write vulnerability in the implementation of the DCE/RPC protocol.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Affairs
OCTOBER 25, 2023
Citrix warned of attacks actively exploiting the vulnerability CVE-2023-4966 in NetScaler ADC and Gateway appliances. Citrix is urging administrators to secure all NetScaler ADC and Gateway appliances against the CVE-2023-4966 vulnerability, which is actively exploited in attacks. On October 10, Citrix published a security bulletin related to a critical vulnerability, tracked as CVE-2023-4966, in Citrix NetScaler ADC/Gateway devices. “ Exploits of CVE-2023-4966 on unmitigated appliances have bee

WIRED Threat Level
OCTOBER 25, 2023
Inauthentic accounts on X flocked to its owner’s post about Ukrainian president Vlodymr Zelensky, hailing “Comrade Musk” and boosting pro-Russia propaganda.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
OCTOBER 25, 2023
Critical security flaws have been disclosed in the Open Authorization (OAuth) implementation of popular online services such as Grammarly, Vidio, and Bukalapak, building upon previous shortcomings uncovered in Booking[.]com and Expo.

Security Affairs
OCTOBER 25, 2023
VMware addressed a critical out-of-bounds write vulnerability, tracked as CVE-2023-34048, that impacts vCenter Server. vCenter Server is a critical component in VMware virtualization and cloud computing software suite. It serves as a centralized and comprehensive management platform for VMware’s virtualized data centers. The vulnerability CVE-2023-34048 (CVSS score 9.8) is an out-of-bounds write vulnerability in the implementation of the DCERPC protocol. “ vCenter Server contains an

Bleeping Computer
OCTOBER 25, 2023
A custom Flipper Zero firmware called 'Xtreme' has added a new feature to perform Bluetooth spam attacks on Android and Windows devices.

Dark Reading
OCTOBER 25, 2023
VMware vCenter Servers need immediate patch against critical RCE bug as race against threat actors begins.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
OCTOBER 25, 2023
VMware issued security updates to fix a critical vCenter Server vulnerability that can be exploited to gain remote code execution attacks on vulnerable servers. [.

Dark Reading
OCTOBER 25, 2023
In the race over Citrix's latest vulnerability, the bad guys have a huge head start, with broad implications for businesses and critical infrastructure providers worldwide.

SecureList
OCTOBER 25, 2023
Introduction It’s just another cryptocurrency miner… Nobody would even suspect the mining malware was merely a mask, masquerading behind an intricate modular framework that supports both Linux and Windows. It comes equipped with a built-in TOR network tunnel for communication with command servers, along with update and delivery functionality through trusted services such as GitLab, GitHub, and Bitbucket, all using custom encrypted archives.

GlobalSign
OCTOBER 25, 2023
Discover the features and benefits of G-Cloud 13 and how it can revolutionize the way government businesses operate.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Bleeping Computer
OCTOBER 25, 2023
Microsoft is testing support for the Discovery of Network-designated Resolvers (DNR) internet standard, which enables automated client-side discovery of encrypted DNS servers on local area networks. [.

Security Boulevard
OCTOBER 25, 2023
Security flaws in the implementation of the OAuth authentication standard left hundreds of millions of users to at least three popular online sites exposed to possible account takeover by bad actors, according to researchers at Salt Security. The vulnerability resulting from how OAuth (Open Authorization) is integrated into web services platforms is the latest uncovered.

Dark Reading
OCTOBER 25, 2023
Cyber threats on satellite technology will persist and evolve. We need a comprehensive cybersecurity framework to protect them from attackers.

Heimadal Security
OCTOBER 25, 2023
BHI Energy, a US energy services company linked to Westinghouse Electric Company, has revealed specifics about a cyberattack on their systems. The Akira ransomware group is responsible for the breach that took place on May 30, 2023. As a division of Westinghouse Electric Company, BHI Energy provides specialized engineering services and staffing solutions to oil […] The post US Energy Company Reveals How Akira Ransomware Compromised its Systems appeared first on Heimdal Security Blog.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Dark Reading
OCTOBER 25, 2023
We have too much cybersecurity awareness. It's time to implement repeatable, real-world practice that ingrains positive habits and security behaviors.

The Hacker News
OCTOBER 25, 2023
The threat actor known as Winter Vivern has been observed exploiting a zero-day flaw in Roundcube webmail software on October 11, 2023, to harvest email messages from victims' accounts. "Winter Vivern has stepped up its operations by using a zero-day vulnerability in Roundcube," ESET security researcher Matthieu Faou said in a new report published today.

Bleeping Computer
OCTOBER 25, 2023
Windows 11 will let admins mandate SMB client encryption for all outbound connections, starting with today's Windows 11 Insider Preview Build 25982 rolling out to Insiders in the Canary Channel. [.

The Hacker News
OCTOBER 25, 2023
In today's digital landscape, around 60% of corporate data now resides in the cloud, with Amazon S3 standing as the backbone of data storage for many major corporations. Despite S3 being a secure service from a reputable provider, its pivotal role in handling vast amounts of sensitive data (customer personal information, financial data, intellectual property, etc.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Bleeping Computer
OCTOBER 25, 2023
A proof-of-concept (PoC) exploit is released for the 'Citrix Bleed' vulnerability, tracked as CVE-2023-4966, that allows attackers to retrieve authentication session cookies from vulnerable Citrix NetScaler ADC and NetScaler Gateway appliances. [.

The Hacker News
OCTOBER 25, 2023
Users of Mirth Connect, an open-source data integration platform from NextGen HealthCare, are being urged to update to the latest version following the discovery of an unauthenticated remote code execution vulnerability. Tracked as CVE-2023-43208, the vulnerability has been addressed in version 4.4.1 released on October 6, 2023.

Malwarebytes
OCTOBER 25, 2023
VMWare has issued an update to address one out-of-bounds write and one information disclosure vulnerability in its server management software, vCenter Server. Since there are no in-product workarounds, customers are advised to apply the updates urgently. The affected products are VMware vCenter Server versions 7.0 and 8.0 and VMware Cloud Foundation versions 5.x and 4.x.

The Hacker News
OCTOBER 25, 2023
The popularity of Brazil's PIX instant payment system has made it a lucrative target for threat actors looking to generate illicit profits using a new malware called GoPIX. Kaspersky, which has been tracking the active campaign since December 2022, said the attacks are pulled off using malicious ads that are served when potential victims search for "WhatsApp web" on search engines.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

Malwarebytes
OCTOBER 25, 2023
In what may come as a surprise, subscription-based face search engine PimEyes seems to have realized that their service can be used for nefarious purposes. PimEyes’ CEO Giorgi Gobronidze told the New York Times that it has taken technical measures to block such searches as part of a “no harm policy.” PimEyes is a search service that uses facial recognition technology to find online photos of people.
The Hacker News
OCTOBER 25, 2023
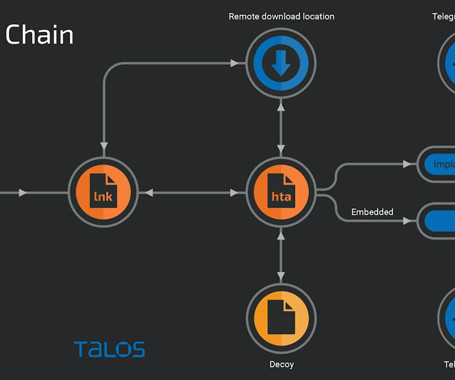
A relatively new threat actor known as YoroTrooper is likely made up of operators originating from Kazakhstan. The assessment, which comes from Cisco Talos, is based on their fluency in Kazakh and Russian, use of Tenge to pay for operating infrastructure, and very limited targeting of Kazakhstani entities, barring the government's Anti-Corruption Agency.

The Last Watchdog
OCTOBER 25, 2023
North Andover, Mass., Oct.25, 2023— DataPivot Technologies , a prominent provider of Data Center, Cloud and Data Protection Solutions, understands that healthcare providers today are scrambling to solve complex clinical, operational and patient data backup & recovery challenges. In response to this industry’s data growth and complexity, DataPivot is delivering innovative data protection solutions that are modern, flexible and scalable, empowering their clients to navigate the complexitie

Bleeping Computer
OCTOBER 25, 2023
The Winter Vivern Russian hacking group has been exploiting a Roundcube Webmail zero-day since at least October 11 to attack European government entities and think tanks. [.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content