James Bamford on Section 702 Extension
Schneier on Security
JUNE 28, 2024
Longtime NSA-watcher James Bamford has a long article on the reauthorization of Section 702 of the Foreign Intelligence Surveillance Act (FISA).

Schneier on Security
JUNE 28, 2024
Longtime NSA-watcher James Bamford has a long article on the reauthorization of Section 702 of the Foreign Intelligence Surveillance Act (FISA).

Malwarebytes
JUNE 28, 2024
Chinese online shopping giant Temu is facing a lawsuit filed by State of Arkansas Attorney General Tim Griffin, alleging that the retailer’s mobile app spies on users. “Temu purports to be an online shopping platform, but it is dangerous malware, surreptitiously granting itself access to virtually all data on a user’s cellphone.” Temu quickly denied the allegations.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
JUNE 28, 2024
Chinese fast-fashion-cum-junk retailer “is a data-theft business.” The post Temu is Malware — It Sells Your Info, Accuses Ark. AG appeared first on Security Boulevard.
Security Affairs
JUNE 28, 2024
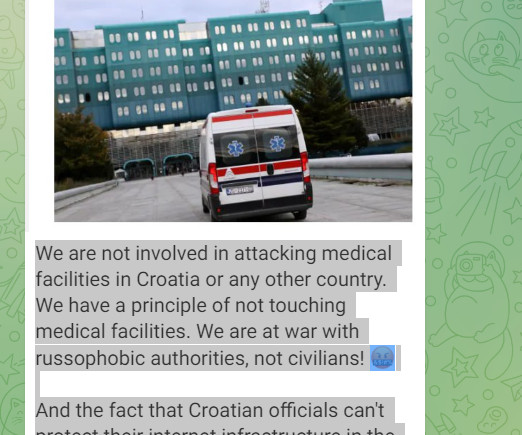
A cyber attack started targeting the University Hospital Centre Zagreb (KBC Zagreb) on Wednesday night, reported the Croatian Radiotelevision. A cyber attack began targeting the University Hospital Centre Zagreb (KBC Zagreb), the largest Croatian hospital, on Wednesday night, according to a report by Croatian Radiotelevision. The hospital has shut down its IT infrastructure in response to the cyber attack.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
JUNE 28, 2024
The North Korea-linked threat actor known as Kimsuky has been linked to the use of a new malicious Google Chrome extension that's designed to steal sensitive information as part of an ongoing intelligence collection effort.

Security Boulevard
JUNE 28, 2024
A threat group dubbed Unfurling Hemlock infects targeted campaign with a single compressed file that, once executed, launches a 'cluster bomb' of as many as 10 pieces of malware that include loaders, stealers, and backdoors. The post Unfurling Hemlock Tossing ‘Cluster Bombs’ of Malware appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Boulevard
JUNE 28, 2024
Microsoft details Skeleton Key, a new jailbreak technique in which a threat actor can convince an AI model to ignore its built-in safeguards and respond to requests for harmful, illegal, or offensive requests that might otherwise have been refused. The post Skeleton Key the Latest Jailbreak Threat to AI Models: Microsoft appeared first on Security Boulevard.

The Hacker News
JUNE 28, 2024
GitLab has released security updates to address 14 security flaws, including one critical vulnerability that could be exploited to run continuous integration and continuous deployment (CI/CD) pipelines as any user. The weaknesses, which affect GitLab Community Edition (CE) and Enterprise Edition (EE), have been addressed in versions 17.1.1, 17.0.3, and 16.11.5.

Security Boulevard
JUNE 28, 2024
For two decades or so now, web applications have been the backbone of many businesses, making their security paramount. Dynamic Application Security Testing (DAST) and penetration testing are crucial for identifying and mitigating security vulnerabilities in web application security. While both aim to enhance application security, they differ significantly in their approach, execution, and outcomes. … DAST Vs.

The Hacker News
JUNE 28, 2024
Security researchers have shed more light on the cryptocurrency mining operation conducted by the 8220 Gang by exploiting known security flaws in the Oracle WebLogic Server.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

eSecurity Planet
JUNE 28, 2024
Millions of WordPress websites are under threat after a critical security breach involving several popular plugins. Security researchers discovered malicious code injected into these plugins, granting hackers the ability to create unauthorized administrator accounts. This compromise can lead to severe consequences for website owners, including data breaches and total website takeovers.

The Hacker News
JUNE 28, 2024
Multiple security flaws have been disclosed in Emerson Rosemount gas chromatographs that could be exploited by malicious actors to obtain sensitive information, induce a denial-of-service (DoS) condition, and even execute arbitrary commands. The flaws impact GC370XA, GC700XA, and GC1500XA and reside in versions 4.1.5 and prior.

Bleeping Computer
JUNE 28, 2024
RMM software developer TeamViewer says a Russian state-sponsored hacking group known as Midnight Blizzard is believed to be behind a breach of their corporate network this week. [.

Veracode Security
JUNE 28, 2024
In today's digital landscape, Application Programming Interfaces (APIs) play an important role in driving innovation. They allow you to integrate new applications with existing systems, reuse code and deliver software more efficiently. But, APIs are also prime targets for hackers due to their public availability and the large amounts of web data they transmit.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
JUNE 28, 2024
Crypto-Agility Required to Migrate to a New Certificate Authority (CA) Seamlessly and Highlights Need for Post-Quantum Cryptography (PQC) Readiness This week Google announced that the Google Chrome browser will no longer trust TLS certificates issued by the Entrust Certificate Authority (CA) starting November 1, 2024. Certificates issued by Entrust before October 31, 2024 will remain […] The post Attention: Google To Distrust Entrust TLS Certificates appeared first on Security Boulevard.

The Hacker News
JUNE 28, 2024
The modern kill chain is eluding enterprises because they aren’t protecting the infrastructure of modern business: SaaS. SaaS continues to dominate software adoption, and it accounts for the greatest share of public cloud spending. But enterprises and SMBs alike haven’t revised their security programs or adopted security tooling built for SaaS.

Security Boulevard
JUNE 28, 2024
Insight #1 Most ransomware deploys a remote-access Trojan (RAT), which allows for secondary infections to occur and enables access to victims’ networks to be sold in Darkweb forums. Insight #2 Most ransomware is delivered initially through the exploitation of a vulnerability. Runtime Security can mitigate this: It’s a highly effective exploit prevention for zero days , unknown vulnerabilities and a broad array of exploit techniques.

Graham Cluley
JUNE 28, 2024
More of Microsoft's clients are being warned that emails they exchanged with the company were accessed by Russian hackers who broke into its systems and spied on staff inboxes. Read more in my article on the Hot for Security blog.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
JUNE 28, 2024
Ticketmaster has started to notify customers who were impacted by a data breach after hackers stole the company's Snowflake database, containing the data of millions of people. [.

Heimadal Security
JUNE 28, 2024
A new critical authentication bypass flaw in Progress MOVEit Transfer was disclosed, and threat actors are already trying their best to exploit it. The new security flaw, which goes by the number CVE-2024-5806, enables attackers to get around the Secure File Transfer Protocol (SFTP) module’s authentication procedure, which is in charge of handling file transfers […] The post New MOVEit Transfer Critical Vulnerability Targeted by Threat Actors appeared first on Heimdal Security Blog.

Bleeping Computer
JUNE 28, 2024
The recent large scale supply chain attack conducted via multiple CDNs, namely Polyfill.io, BootCDN, Bootcss, and Staticfile that affected up to tens of millions of websites has been traced to a common operator. Researchers discovered a public GitHub repository with leaked API keys helping them draw a conclusion. [.

Digital Guardian
JUNE 28, 2024
Congress' sweeping privacy bill was stopped in its tracks, CISA's own tool was targeted in a January breach, concerns are arising over open-source code, & more. Read more about all these stories in this week's Friday Five.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

SecureBlitz
JUNE 28, 2024
Learn why small businesses should invest in managed IT. Running a small business is challenging enough without wrestling with tech issues. You're juggling countless tasks, from managing team members to keeping your customers happy. Amid all this, you can easily overlook your technological needs. But here's the thing: neglecting your Information Technology (IT) can cost […] The post Why Small Businesses Should Invest In Managed IT appeared first on SecureBlitz Cybersecurity.

Heimadal Security
JUNE 28, 2024
We are excited to announce a special release, substantiating our key cross-platform product direction. New features and improvements are rolling out for Linux Ubuntu, macOS, and Windows. The updates are available in the Release Candidate and Production versions of the Heimdal dashboard (4.2.2 RC and 4.1.4 Production), and in the dedicated agent versions: Heimdal for […] The post Cross-Platform Product Release: Heimdal Integrates with HaloPSA appeared first on Heimdal Security Blog.

Graham Cluley
JUNE 28, 2024
There's some possibly good news on the ransomware front. Companies are becoming more resilient to attacks, and the ransom payments extorted from businesses by hackers are on a downward trend. Read more in my article on the Tripwire State of Security blog.

Digital Guardian
JUNE 28, 2024
Congress' sweeping privacy bill was stopped in its tracks, CISA's own tool was targeted in a January breach, concerns are arising over open-source code, & more. Read more about all these stories in this week's Friday Five.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Bleeping Computer
JUNE 28, 2024
Infosys McCamish Systems (IMS) disclosed that the LockBit ransomware attack it suffered earlier this year impacted sensitive information of more than six million individuals. [.

Graham Cluley
JUNE 28, 2024
Car dealerships have been brought to a standstill across the United States after a software provider was hit by a ransomware attack. The attack, believed to be by the BlackSuit ransomware gang, forced CDK Global, makers of a platform widely used by car dealerships to conduct their everyday business, to down its IT systems and data centers. Read more in my article on the Exponential-e blog.

Bleeping Computer
JUNE 28, 2024
Agropur, one of the largest dairy cooperatives in North America, is notifying customers of a data breach after some of its shared online directories were exposed. [.

WIRED Threat Level
JUNE 28, 2024
WIRED was able to download stories from publishers like The New York Times and The Atlantic using Poe’s Assistant bot. One expert calls it “prima facie copyright infringement,” which Quora disputes.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content