Take a Selfie Using a NY Surveillance Camera
Schneier on Security
AUGUST 23, 2024
This site will let you take a selfie with a New York City traffic surveillance camera.

Schneier on Security
AUGUST 23, 2024
This site will let you take a selfie with a New York City traffic surveillance camera.
Krebs on Security
AUGUST 23, 2024
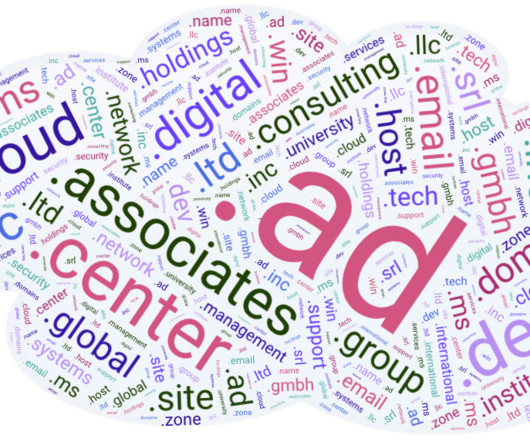
The proliferation of new top-level domains (TLDs) has exacerbated a well-known security weakness: Many organizations set up their internal Microsoft authentication systems years ago using domain names in TLDs that didn’t exist at the time. Meaning, they are continuously sending their Windows usernames and passwords to domain names they do not control and which are freely available for anyone to register.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Troy Hunt
AUGUST 23, 2024
It should be so simple: you're a customer who wants to purchase something so you whip out the credit card and buy it. I must have done this thousands of times, and it's easy! I've bought stuff with plastic credit cards, stuff with Apple Pay on my phone and watch and, like all of us, loads of stuff simply by entering credit card details into a website.

Tech Republic Security
AUGUST 23, 2024
A new malware called NGate allows cybercriminals to steal near field communication data from Android phones via sophisticated social engineering. The data is relayed to the fraudsters before being used to steal cash.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
AUGUST 23, 2024
The threat actors behind a recently observed Qilin ransomware attack have stolen credentials stored in Google Chrome browsers on a small set of compromised endpoints. The use of credential harvesting in connection with a ransomware infection marks an unusual twist, and one that could have cascading consequences, cybersecurity firm Sophos said in a Thursday report.

Penetration Testing
AUGUST 23, 2024
Microsoft has released an urgent security update for its Edge browser, patching a critical vulnerability that is currently being exploited by malicious actors. This zero-day flaw, tracked as CVE-2024-7971, exists... The post Urgent Edge Security Update: Microsoft Patches Zero-day & RCE Vulnerabilities appeared first on Cybersecurity News.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Malwarebytes
AUGUST 23, 2024
Some scammers have the morals of an alley cat. But some sink even lower. Over the last few months, Malwarebytes Labs has discovered scammers active on Facebook that prey on bereaved people by using stolen images and phony funeral live stream links to steal money and/or credit card details. These scammers are becoming more active and new cybercriminals are picking up the method as well, which is something we see very often.
Security Affairs
AUGUST 23, 2024
Sophos researchers investigated a Qilin ransomware breach attack that led to the theft of credentials stored in Google Chrome browsers. Sophos researchers investigated a Qilin ransomware attack where operators stole credentials stored in Google Chrome browsers of a limited number of compromised endpoints. The experts pointed out that the credential harvesting activity is usually not associated with ransomware infections.

Security Boulevard
AUGUST 23, 2024
Oink, oink, FAIL—you’re in jail: Kansas bank chief exec Shan Hanes stole money from investors, a church and others to buy cryptocurrency to feed a scam. The post Pig Butchering at Heart of Bank Failure — CEO Gets 24 Years in Jail appeared first on Security Boulevard.
Security Affairs
AUGUST 23, 2024
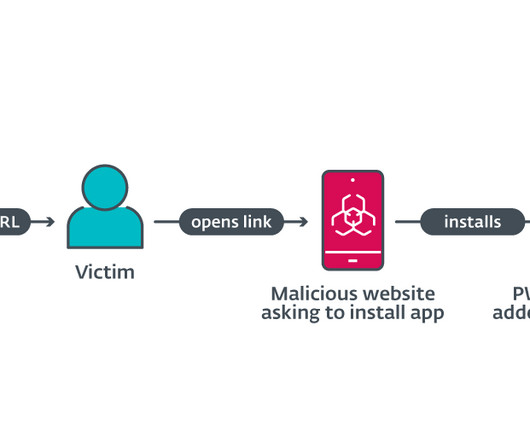
Cybercriminals use progressive web applications (PWA) to impersonate banking apps and steal credentials from mobile users. ESET researchers detailed a phishing campaign against mobile users that uses Progressive Web Applications (PWAs). The threat actors used fake apps almost indistinguishable from real banking apps on both iOS and Android. The technique was first disclosed in Poland in July 2023 and later observed in Czechia and other countries like Hungary and Georgia.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Hacker News
AUGUST 23, 2024
Let's be honest. The world of cybersecurity feels like a constant war zone. You're bombarded by threats, scrambling to keep up with patches, and drowning in an endless flood of alerts. It's exhausting, isn’t it? But what if there was a better way? Imagine having every essential cybersecurity tool at your fingertips, all within a single, intuitive platform, backed by expert support 24/7.
Security Affairs
AUGUST 23, 2024
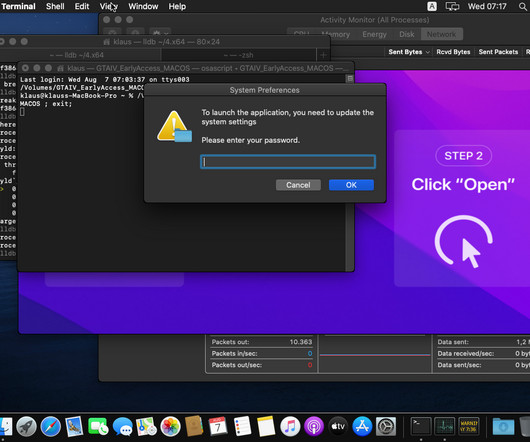
Cato Security found a new info stealer, called Cthulhu Stealer, that targets Apple macOS and steals a wide range of information. Cado Security researchers have discovered a malware-as-a-service (MaaS) targeting macOS users dubbed Cthulhu Stealer. Cthulhu Stealer targets macOS users via an Apple disk image (DMG) that disguises itself as legitimate software.

The Hacker News
AUGUST 23, 2024
Read the full article for key points from Intruder’s VP of Product, Andy Hornegold’s recent talk on exposure management. If you’d like to hear Andy’s insights first-hand, watch Intruder’s on-demand webinar. To learn more about reducing your attack surface, reach out to their team today.
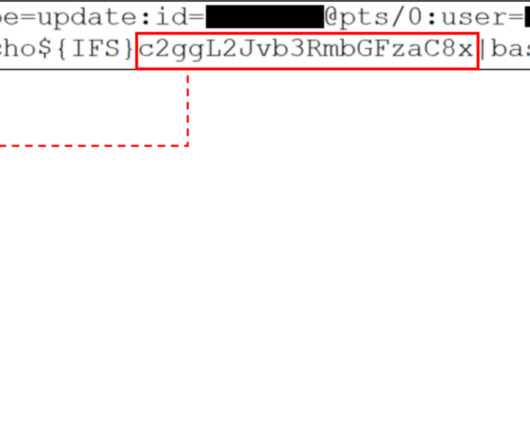
Security Affairs
AUGUST 23, 2024
China-linked APT group Velvet Ant exploited a recently disclosed zero-day in Cisco switches to take over the network appliance. Researchers at cybersecurity firm Sygnia reported that the China-linked APT group Velvet Ant has exploited the recently disclosed zero-day CVE-2024-20399 in Cisco switches to take over the network devices. In July 2024, Cisco addressed the NX-OS zero-day CVE-2024-20399 (CVSS score of 6.0) that China-linked group Velvet Ant exploited to deploy previously unknown malw

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
AUGUST 23, 2024
Implementing shared threat intelligence across an alliance of cybersecurity experts creates a more robust security approach. The post Pool Your Cybersecurity Resources to Build the Perfect Security Ecosystem appeared first on Security Boulevard.

SecureWorld News
AUGUST 23, 2024
Halliburton, one of the world's leading oilfield service companies, has confirmed that its corporate networks have been impacted by an unspecified issue following reports of a cyberattack. The incident has raised concerns within the energy sector, as Halliburton plays a crucial role in global oilfield operations, and any disruption to its networks could have far-reaching implications.

Security Boulevard
AUGUST 23, 2024
DOJ inspectors have found the FBI is not labeling hard drives and other storage devices holding sensitive that are slated for destruction, making them hard to track, and that boxes of them can sit in a poorly secured facility for months. The post Audit: FBI is Losing Track of Storage Devices Holding Sensitive Data appeared first on Security Boulevard.

Security Affairs
AUGUST 23, 2024
The Russian national Deniss Zolotarjovs has been charged in a U.S. court for his role in the Karakurt cybercrime gang. Deniss Zolotarjovs (33), a Russian cybercriminal, has been charged in a U.S. court for his role in the Russian Karakurt cybercrime gang. The man has been charged with money laundering, wire fraud, and extortion. The man was arrested in Georgia in December 2023 and recently extradited to the U.S. “According to court documents, Zolotarjovs is a member of a known cybercrimina

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

SecureWorld News
AUGUST 23, 2024
Traditional perimeter-based security models are no longer sufficient to protect against sophisticated attacks that can easily bypass firewalls and other boundary defenses. As a result, many organizations are turning to Zero Trust. In fact, data shows that more than 60% of organizations have already fully or partially adopted a Zero Trust strategy. However, implementing Zero Trust can be complex, and many organizations face challenges that hinder successful implementation.

Security Boulevard
AUGUST 23, 2024
Authors/Presenters:Yanmao Man, University of Arizona; Raymond Muller, Purdue University; Ming Li, University of Arizona; Z. Berkay Celik, Purdue University; Ryan Gerdes, Virginia Tech Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open Access. Originating from the conference’s events situated at the Anaheim Marriott ; and via the organizations YouTube channel.

WIRED Threat Level
AUGUST 23, 2024
The Telegram channel and website Deep State uses public data and insider intelligence to power its live tracker of Ukraine’s ever-shifting front line.

Zero Day
AUGUST 23, 2024
Code faster and work smarter with a Microsoft Visual Studio Professional 2022 license, now on sale for 92% off.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

We Live Security
AUGUST 23, 2024
ESET researchers have recently revealed an uncommon type of phishing campaign using Progressive Web Apps (PWAs) that targeted the clients of a prominent Czech bank.

Zero Day
AUGUST 23, 2024
Microsoft's project management solutions include timesheet support, org charts, and more to help you stay organized -- and they're on sale for 92% off.

Security Boulevard
AUGUST 23, 2024
According to an updated advisory from the United States (US) Cybersecurity and Infrastructure Security Agency and the Federal Bureau of Investigation (FBI), the BlackSuit ransomware strain is known to have had demands totaling up to $500 million in payments. In this article, we’ll dive into the details of the ransomware attacks, determine who the key […] The post BlackSuit Ransomware Threat Actors Demand Up To $500 Million appeared first on TuxCare.

Penetration Testing
AUGUST 23, 2024
A new and insidious threat has emerged, targeting the widely used PostgreSQL database management system. Aqua Nautilus researchers have identified a novel malware strain, named “PG_MEM,” which employs a sophisticated... The post New PostgreSQL Threat: PG_MEM Malware Strikes Databases appeared first on Cybersecurity News.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Security Boulevard
AUGUST 23, 2024
In response to the recent CISA Advisory (AA24-234A) outlining best practices for event logging and threat detection, AttackIQ, in alignment with CISA’s guidance, strongly encourages organizations to engage in continuous testing against known, real-world adversary behaviors and TTPs through rigorous security control validation. The post Response to CISA Advisory (AA24-234A): Strengthening Defenses Through Effective Event Logging and Threat Detection appeared first on AttackIQ.

Penetration Testing
AUGUST 23, 2024
In a recent cybersecurity alert, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has highlighted the active exploitation of a severe vulnerability identified as CVE-2024-39717. This flaw, found within Versa... The post CVE-2024-39717: Versa Networks Director GUI Flaw Under Active Attack, CISA Issues Urgent Patching Directive appeared first on Cybersecurity News.

Security Boulevard
AUGUST 23, 2024
In today’s hyper-connected digital landscape, APIs are the lifeblood of innovation, powering everything from customer experiences to internal operations. However, with this growing reliance on APIs comes a dark side—zombie and shadow APIs. These hidden, forgotten, or undocumented endpoints present significant security risks that traditional approaches simply can’t address.

Digital Guardian
AUGUST 23, 2024
As ransomware, misconfigurations, and other vulnerabilities continue to be stubborn threats to mitigate, CISA and the FBI promise election security, and the FAA is pushing for tighter regulations. Learn about these top stories and more in this week's Friday Five!

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content