Public Surveillance of Bars
Schneier on Security
JULY 2, 2024
This article about an app that lets people remotely view bars to see if they’re crowded or not is filled with commentary—on both sides—about privacy and openness.

Schneier on Security
JULY 2, 2024
This article about an app that lets people remotely view bars to see if they’re crowded or not is filled with commentary—on both sides—about privacy and openness.

Tech Republic Security
JULY 2, 2024
Which is better, Surfshark or IPVanish? Use our guide to help you compare pricing, features and more.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JULY 2, 2024
Prudential Financial confirmed that more than 2.5 million individuals were affected by the data breach it suffered in February 2024. The insurance company Prudential Financial confirmed that the data breach it suffered in February 2024 affected over 2.5 million individuals. The incident occurred on February 4, 2024, and was discovered on February 5, 2024.

Security Boulevard
JULY 2, 2024
Tim looks grim: 10 year old vulnerabilities in widely used dev tool include a CVSS 10.0 remote code execution bug. The post ‘Perfect 10’ Apple Supply Chain Bug — Millions of Apps at Risk of CocoaPods RCE appeared first on Security Boulevard.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Affairs
JULY 2, 2024
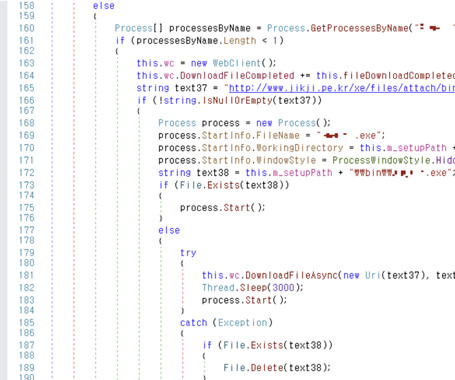
Cisco fixed an actively exploited NX-OS zero-day, the flaw was exploited to install previously unknown malware as root on vulnerable switches. Cisco addressed an NX-OS zero-day, tracked as CVE-2024-20399 (CVSS score of 6.0), that the China-linked group Velvet Ant exploited to deploy previously unknown malware as root on vulnerable switches. The flaw resides in the CLI of Cisco NX-OS Software, an authenticated, local attacker can exploit the flaw to execute arbitrary commands as root on the und
The Hacker News
JULY 2, 2024
An unnamed South Korean enterprise resource planning (ERP) vendor's product update server has been found to be compromised to deliver a Go-based backdoor dubbed Xctdoor.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
The Hacker News
JULY 2, 2024
Modern CPUs from Intel, including Raptor Lake and Alder Lake, have been found vulnerable to a new side-channel attack that could be exploited to leak sensitive information from the processors.

Security Affairs
JULY 2, 2024
Fintech firms Wise and Affirm confirmed they were both impacted by the recent data breach suffered by Evolve Bank. Fintech companies Wise and Affirm have confirmed that they were both affected by the recent data breach at Evolve Bank. At the end of June, the LockBit gang announced that it had breached the systems of the Federal Reserve of the United States and exfiltrated 33 TB of sensitive data, including “Americans’ banking secrets.

The Last Watchdog
JULY 2, 2024
Security teams rely on an ever-growing stack of cybersecurity tools to keep their organization safe. Related: The worst year ever for breaches Yet there remains a glaring disconnect between security systems and employees. Now comes a start-up, Amplifier Security , with a bold new approach to orchestrate security actions. Just after RSAC 2024 , I spoke with Thomas Donnelly , Amplifier’s co-founder and CTO, about how that they’re utilizing large language models (LLMs) and to emphasize continual em

The Hacker News
JULY 2, 2024
Cybersecurity researchers have discovered an attack campaign that targets various Israeli entities with publicly-available frameworks like Donut and Sliver.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Affairs
JULY 2, 2024
An Australian man has been charged with carrying out ‘Evil Twin’ Wi-Fi attack during a domestic flight to steal user credentials and data. An Evil Twin Wi-Fi attack is a type of cyberattack where a threat actor sets up a rogue wireless access point that mimics a legitimate one. The goal is to trick users into connecting to the fake access point, thereby allowing the attacker to intercept, capture, and manipulate data transmitted by the victim.
The Hacker News
JULY 2, 2024
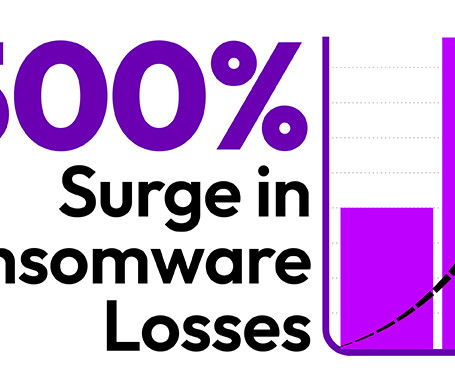
The cybersecurity threat landscape has witnessed a dramatic and alarming rise in the average ransomware payment, an increase exceeding 500%.

We Live Security
JULY 2, 2024
While AI can liberate us from tedious tasks and even eliminate human error, it's crucial to remember its weaknesses and the unique capabilities that humans bring to the table

Security Boulevard
JULY 2, 2024
As cyber threats evolve, the European Union has taken significant steps to bolster cybersecurity across its member states. Central to this effort is the European Cybersecurity Certification Scheme on Common Criteria (EUCC), spearheaded by the European Union Agency for Cybersecurity (ENISA). Released in early 2024, the EUCC aims to create a unified security benchmark for.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Bleeping Computer
JULY 2, 2024
Google has launched kvmCTF, a new vulnerability reward program (VRP) first announced in October 2023 to improve the security of the Kernel-based Virtual Machine (KVM) hypervisor that comes with $250,000 bounties for full VM escape exploits. [.

Security Boulevard
JULY 2, 2024
Qualys this week reported the discovery of a Remote Unauthenticated Code Execution (RCE) vulnerability in OpenSSH servers (sshd) that could potentially impact more than 14 million Linux systems. The post Latest OpenSSH Vulnerability Might Impact 14M Linux Systems appeared first on Security Boulevard.

Malwarebytes
JULY 2, 2024
In February 2024, Prudential Financial reported it had fallen victim to a ransomware attack. The attack was discovered one day after it started, but not before some 2.5 million people had been impacted by the resulting data breach. As one of the largest insurance companies in the US, Prudential employs 40,000 people worldwide and reported revenues of over $50 billion in 2023.

Security Boulevard
JULY 2, 2024
Critical infrastructure and public sector organizations such as government and municipalities, manufacturing units, communication networks, transportation services, power and water treatment plants, et. al, have been battling a growing wave of breaches and cyberattacks. The post 7 Steps To Secure Critical Infrastructure appeared first on Security Boulevard.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
JULY 2, 2024
Multiple owners of Google Pixel 6 series phones (6, 6a, 6 Pro) have been reporting in the past week that their devices were "bricked" after they performed a factory reset. [.

Security Boulevard
JULY 2, 2024
For OEMs and dealerships, a written information security plan is essential for protecting sensitive data, securing networked vehicle systems, ensuring regulatory compliance and preparing for potential security incidents. But merely having a plan in place isn’t enough—here’s why it should be an updated, dynamic document if you really want to reduce risks from increased cyber threats.

SecureWorld News
JULY 2, 2024
Global cyber insurance premiums are declining despite an uptick in ransomware attacks, according to a recent report by insurance broker Howden. This trend reflects improved business security practices, evolving insurance industry dynamics, and changing attitudes toward cyber risk management. According to Reuters , the Howden report indicates that the cyber insurance market experienced double-digit price reductions in 2023/24, a stark contrast to the skyrocketing premiums seen in 2021 and 2022 du

Bleeping Computer
JULY 2, 2024
Buy now, pay later loan company Affirm is warning that holders of its payment cards had their personal information exposed due to a data breach at its third-party issuer, Evolve Bank & Trust (Evolve). [.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

GlobalSign
JULY 2, 2024
Root Ubiquity is a seal of trust among security providers. This blog explores what it is and why it’s so important.

SecureBlitz
JULY 2, 2024
This post will show you our guide to material resource planning for businesses… In the ever-changing world of contemporary corporate operations, competitiveness and sustainable development depend heavily on efficiency and adaptability. The foundation for inventory management, supply chain synchronization, and manufacturing process optimization is Material Resource Planning (MRP).

Bleeping Computer
JULY 2, 2024
Patelco Credit Union has disclosed it experienced a ransomware attack that led to the proactive shutdown of several of its customer-facing banking systems to contain the incident's impact. [.

SecureBlitz
JULY 2, 2024
Here, I will talk about how to attract and retain clients. Building a successful salon business requires more than just excellent services; it demands effective brand development strategies. Attracting and retaining clients hinges on creating a distinct brand identity. Clients today seek memorable experiences and personalized services. Effective brand building ensures that a salon stands […] The post Brand Building for Salons: How to Attract and Retain Clients appeared first on SecureBlitz

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Penetration Testing
JULY 2, 2024
A severe security flaw, CVE-2024-36401 (CVSS 9.8), has been discovered in GeoServer, a widely-used open-source software platform for managing and sharing geospatial data. This vulnerability could potentially allow attackers to execute arbitrary code on... The post CVE-2024-36401 (CVSS 9.8): Urgent Patch Needed for GeoServer RCE Vulnerability appeared first on Cybersecurity News.

Graham Cluley
JULY 2, 2024
Find out why AI is stupid, what Toys "R" Us has done that's even more annoying than putting that "R" in its name, why Graham Cluley has an angry AI girlfriend, and much much more in episode five of "The AI Fix" podcast

Tech Republic Security
JULY 2, 2024
If you’re a Linux admin, you probably take care of any number of servers, all of which contain numerous users. Those users log in via various means or protocols, such as SSH, FTP and HTTP. In order to successfully log in, those users have to have — passwords. A single word that sends shivers through.

Penetration Testing
JULY 2, 2024
Juniper Networks, a leading provider of networking solutions, has issued a critical security advisory warning users of a high-severity vulnerability affecting their SRX Series firewalls. This vulnerability, tracked as CVE-2024-21586 (CVSSv4 8.7), allows unauthenticated... The post CVE-2024-21586: Juniper SRX Vulnerability Leaves Networks Open to Attack appeared first on Cybersecurity News.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content