Breaking the M-209
Schneier on Security
JUNE 25, 2024
Interesting paper about a German cryptanalysis machine that helped break the US M-209 mechanical ciphering machine. The paper contains a good description of how the M-209 works.

Schneier on Security
JUNE 25, 2024
Interesting paper about a German cryptanalysis machine that helped break the US M-209 mechanical ciphering machine. The paper contains a good description of how the M-209 works.
Penetration Testing
JUNE 25, 2024
A security researcher has published a proof-of-concept (PoC) exploit code targeting a recent high-severity vulnerability (CVE-2024-30088) in Microsoft Windows. This critical flaw holds a risk severity score of 7.0 and impacts systems across the... The post PoC Exploit Published for Windows Kernel Elevation of Privilege Vulnerability (CVE-2024-30088) appeared first on Cybersecurity News.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Hacker News
JUNE 25, 2024
Google has taken steps to block ads for e-commerce sites that use the Polyfill.io service after a Chinese company acquired the domain and modified the JavaScript library ("polyfill.js") to redirect users to malicious and scam sites. More than 110,000 sites that embed the library are impacted by the supply chain attack, Sansec said in a Tuesday report.

Duo's Security Blog
JUNE 25, 2024
As MFA fatigue attacks continue to wreak havoc on organizations of all sizes, security teams are left with difficult choices about how best to secure their workforces. More stringent security requirements often come with a large user experience cost, which can frustrate employees and reduce productivity. Duo’s Risk-Based Authentication (RBA) helps solve this by adapting MFA requirements based on the level of risk an individual login attempt poses to an organization.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.
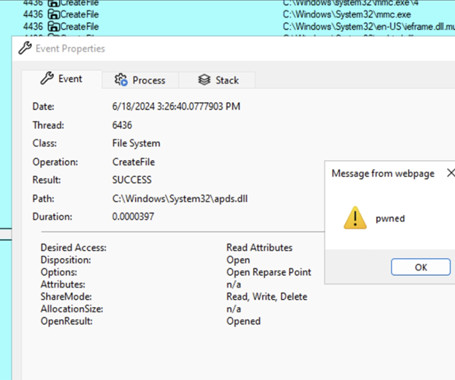
The Hacker News
JUNE 25, 2024
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management Console (MMC) and evade security defenses. Elastic Security Labs has codenamed the approach GrimResource after identifying an artifact ("sccm-updater.

Security Boulevard
JUNE 25, 2024
Copying users’ files and deleting some? Even a cartoon hound knows this isn’t fine. The post Microsoft Privacy FAIL: Windows 11 Silently Backs Up to OneDrive appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
JUNE 25, 2024
Red Teaming security assessments aim to demonstrate to clients how attackers in the real world might link together various exploits and attack methods to reach their objectives. The post Stepping Into the Attacker’s Shoes: The Strategic Power of Red Teaming (Insights from the Field) appeared first on Security Boulevard.
SecureList
JUNE 25, 2024
Small and medium-sized businesses (SMBs) are increasingly targeted by cybercriminals. Despite adopting digital technology for remote work, production, and sales, SMBs often lack robust cybersecurity measures. SMBs face significant cybersecurity challenges due to limited resources and expertise. The cost of data breaches can cripple operations, making preventive measures essential.

Security Boulevard
JUNE 25, 2024
The LockBit ransomware group is claiming that it hacked into systems at the U.S. Federal Reserve and stole 33TB of data that it will begin leaking as early as Tuesday if the institution doesn’t pay the unspecified ransom. The notorious cybercriminals announced the attack on its dark web leak site on June 23, giving the. The post LockBit Claims Ransomware Attack on U.S.

Security Affairs
JUNE 25, 2024
Researchers warn that a Mirai-based botnet is exploiting a recently disclosed critical vulnerability in EoL Zyxel NAS devices. Researchers at the Shadowserver Foundation warn that a Mirai -based botnet has started exploiting a recently disclosed vulnerability tracked as CVE-2024-29973 (CVSS score 9.8) in end-of-life NAS devices Zyxel NAS products. The flaw is a command injection vulnerability in the “setCookie” parameter in Zyxel NAS326 firmware versions before V5.21(AAZF.17)C0 and NAS542 firmwa

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Boulevard
JUNE 25, 2024
By introducing a mobile device management (MDM) platform into the existing infrastructure, administrators gain the ability to restrict sideloading on managed devices. The post EU Opens the App Store Gates: A Call to Arms for MDM Implementation appeared first on Security Boulevard.

Bleeping Computer
JUNE 25, 2024
Over 100,000 sites have been impacted in a supply chain attack by the Polyfill.io service after a Chinese company acquired the domain and the script was modified to redirect users to malicious and scam sites. [.

Security Affairs
JUNE 25, 2024
WikiLeaks founder Julian Assange has been released in the U.K. and has left the country after five years in Belmarsh prison. Julian Assange is free after five years in Belmarsh prison, the WikiLeaks founder has been released in the U.K. and is flying to the island of Saipan in the Northern Mariana Islands, to make a brief court appearance before flying to Australia where he will be a free man in Australia.

Security Boulevard
JUNE 25, 2024
Security analysts at Google are developing a framework that they hope will enable large language models (LLMs) to eventually be able to run automated vulnerability research, particularly analyses of malware variants. The analysts with Google’s Project Zero – a group founded a decade ago whose job it is to find zero-day vulnerabilities – have been. The post Google’s Project Naptime Aims for AI-Based Vulnerability Research appeared first on Security Boulevard.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

eSecurity Planet
JUNE 25, 2024
Kaspersky Lab is a widely known name in the world of cybersecurity. Founded in 1997, the Russian firm has grown into a global leader, boasting millions of users for its antivirus software and other security solutions. With a presence in over 200 countries and territories, Kaspersky Lab protects individuals, businesses, and critical infrastructure from a wide range of cyber threats.

Bleeping Computer
JUNE 25, 2024
P2PInfect, originally a dormant peer-to-peer malware botnet with unclear motives, has finally come alive to deploy a ransomware module and a cryptominer in attacks on Redis servers. [.

The Hacker News
JUNE 25, 2024
Browser security is becoming increasingly popular, as organizations understand the need to protect at the point of risk - the browser. Network and endpoint solutions are limited in their ability to protect from web-borne threats like phishing websites or malicious browser extensions. They also do not protect from internal data exfiltration, like employees pasting sensitive data to ChatGPT.

Malwarebytes
JUNE 25, 2024
Luxury retail chain Neiman Marcus has begun to inform customers about a cyberattack it discovered in May. The attacker compromised a database platform storing customers’ personal information. The letter tells customers: “Promptly after learning of the issue, we took steps to contain it, including by disabling access to the relevant database platform.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Boulevard
JUNE 25, 2024
Effective April 30, 2024 Airbnb, the global vacation rental giant, announced a significant policy change: the prohibition of all indoor security cameras in its listings worldwide. This decision, aims to bolster the privacy of guests and address longstanding concerns about hidden cameras. While the majority of Airbnb’s over 7 million listings did not report having […] The post Airbnb’s Ban on Indoor Security Cameras: What It Means for Your Personal Cybersecurity appeared first on BlackCloak |

We Live Security
JUNE 25, 2024
VPNs are not all created equal – make sure to choose the right provider that will help keep your data safe from prying eyes

Security Boulevard
JUNE 25, 2024
Let’s explore some of the details behind this escalating threat to SaaS applications, what may be driving it, and what you can do to better protect your SaaS footprint from these types of threats. The post Why SaaS Identity Abuse is This Year’s Ransomware appeared first on RevealSecurity. The post Why SaaS Identity Abuse is This Year’s Ransomware appeared first on Security Boulevard.

Bleeping Computer
JUNE 25, 2024
The FBI is warning of cybercriminals posing as law firms and lawyers that offer cryptocurrency recovery services to victims of investment scams and steal funds and personal information. [.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Security Boulevard
JUNE 25, 2024
Designing software from the ground up to be secure, as recommended by the Secure by Design initiative from the Cybersecurity and Infrastructure Security Agency (CISA) , has its challenges, especially if it's done at scale. The post How platform engineering helps you get a good start on Secure by Design appeared first on Security Boulevard.

Jane Frankland
JUNE 25, 2024
Gordon Moore, a co-founder of Intel, the “father of Silicon Valley,” and well known for “Moore’s Law” once famously said, “Whatever has been done can be outdone.” Tech leaders understand this. They know that becoming agile, strategic, and resilient is not just a goal but a necessity. To compete and win in challenging times such as these, means investing in tech wisely, reducing CapEx and OpEx spend, attracting and retaining top talent, innovating continu

Bleeping Computer
JUNE 25, 2024
A threat actor modified the source code of at least five plugins hosted on WordPress.org to include malicious PHP scripts that create new accounts with administrative privileges on websites running them. [.

Heimadal Security
JUNE 25, 2024
If you’re in the market for an endpoint detection and response (XDR) product, there are plenty of options available. But within the word salad of overlapping terms (XDR, EDR, ASM, and more), it can be a real challenge to actually understand what features you need and where they’re available. This means choosing the right XDR […] The post Sophos vs.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.
Google Security
JUNE 25, 2024
Oliver Chang, Jonathan Metzman, OSS-Fuzz and Alex Rebert, Security Engineering The US Defense Advanced Research Projects Agency, DARPA , recently kicked off a two-year AI Cyber Challenge (AIxCC) , inviting top AI and cybersecurity experts to design new AI systems to help secure major open source projects which our critical infrastructure relies upon.

Trend Micro
JUNE 25, 2024
To test the effectiveness of managed services like our Trend Micro managed detection and response offering, MITRE Engenuity™ combined the tools, techniques, and practices of two globally notorious bad actors: menuPass and ALPHV/BlackCat. This blog tells the story of why they were chosen and what makes them threats to be reckoned with.

WIRED Threat Level
JUNE 25, 2024
How accurate are gunshot detection systems, really? For years, it's been a secret, but new reports from San Jose and NYC show these systems have operated well below their advertised accuracy rates.

Penetration Testing
JUNE 25, 2024
A critical vulnerability (CVE-2024-5806) in the widely used MOVEit Transfer file transfer software has been disclosed and is already under active exploitation. Progress Software, the developer of MOVEit, released information about the vulnerability on... The post CVE-2024-5806: MOVEit Transfer Vulnerability Under Active Exploit, PoC Published appeared first on Cybersecurity News.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content