Deepfake Fraud
Schneier on Security
FEBRUARY 5, 2024
A deepfake video conference call—with everyone else on the call a fake— fooled a finance worker into sending $25M to the criminals’ account.

Schneier on Security
FEBRUARY 5, 2024
A deepfake video conference call—with everyone else on the call a fake— fooled a finance worker into sending $25M to the criminals’ account.

The Last Watchdog
FEBRUARY 5, 2024
Even in the cloud era, Microsoft Exchange Server remains a staple business communications tool across the globe. Related: The need for robust data recovery policies. One critical issue faced by organizations that rely on Exchange Server is the risk of a corrupt Exchange Server database cropping up. Fortunately, effective tools and wise best practices can help mitigate this this exposure enabling companies to indefinitely leverage Exchange Server as a productive, resilient and secure communicatio
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
FEBRUARY 5, 2024
Learn how to set up your account, store and secure your passwords and maximize the features of Enpass with this step-by-step guide.

Penetration Testing
FEBRUARY 5, 2024
Google, a titan in the digital realm, has once again demonstrated its commitment to user security with the release of its February 2024 security updates for Android. This latest security bulletin brings to the... The post CVE-2024-0031: Critical Android Remote Code Execution Vulnerability appeared first on Penetration Testing.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
FEBRUARY 5, 2024
Enpass’ offline password storage and support for third-party cloud services are two feature offerings you won’t find in many other password managers today.

Security Affairs
FEBRUARY 5, 2024
Scammers stole HK$200 million (roughly $25,5 million) from a multi-national company using a deepfake conf call to trick an employee into transferring the funds. Scammers successfully stole HK$200 million (approximately $25.5 million) from a multinational company in Hong Kong by employing a deepfake video call to deceive an employee into transferring the funds.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
FEBRUARY 5, 2024
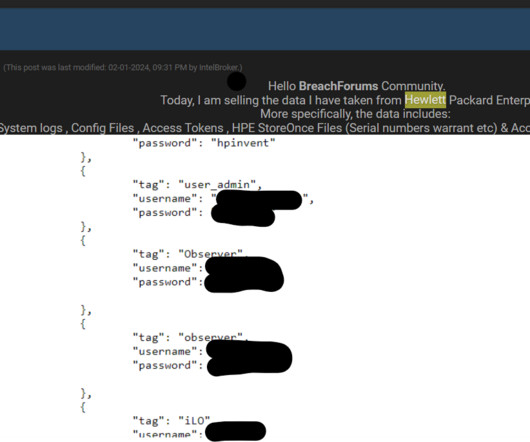
Hewlett Packard Enterprise (HPE) is investigating a new data breach after a threat actor claimed to have stolen data on a hacking forum. Hewlett Packard Enterprise (HPE) is investigating a new data breach, following the discovery of an offer on a hacking forum where a threat actor claimed to be selling the allegedly stolen data. According to Bleeping Computer , the company has yet to find any evidence suggesting a new security breach.

Security Boulevard
FEBRUARY 5, 2024
Secureworks threat score capability leverages artificial intelligence (AI) within its Taegris extended detection and response (XDR) platform. The post Secureworks Applies Multiple Forms of AI to Assess Threat Risks appeared first on Security Boulevard.

Security Affairs
FEBRUARY 5, 2024
Airbus Navblue Flysmart+ Manager allowed attackers to tamper with the engine performance calculations and intercept data. Flysmart+ is a suite of apps for pilot EFBs, helping deliver efficient and safe departure and arrival of flights. Researchers from Pen Test Partners discovered a vulnerability in Navblue Flysmart+ Manager that can be exploited to tamper with the engine performance calculations.
Security Boulevard
FEBRUARY 5, 2024
As the cybersecurity landscape evolves, organizations must adapt their strategies to combat emerging threats. The post Top Trends in Cybersecurity, Ransomware and AI in 2024 appeared first on Security Boulevard.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
FEBRUARY 5, 2024
The Ivanti SSRF vulnerability tracked as CVE-2024-21893 is actively exploited in attacks in the wild by multiple threat actors. The Ivanti Server-Side Request Forgery (SSRF) vulnerability, identified as CVE-2024-21893 , is currently being actively exploited in real-world attacks by various threat actors. Last week Ivanti warned of two new high-severity vulnerabilities in its Connect Secure and Policy Secure solutions respectively tracked as CVE-2024-21888 (CVSS score: 8.8) and CVE-2024-21893 (

IT Security Guru
FEBRUARY 5, 2024
What Is Nanotechnology? Nanotechnology is concerned with nano-scale materials and structures. Nano-scale refers to particles and devices that are less than 100 microns in size. A sheet of paper has a thickness of 100,000 nano-meters, while a person who stands six feet tall has a thickness of 2 billion nano-meters! The properties of materials at the nanoscale can vary significantly, providing unique functionalities and applications for technology.

Security Boulevard
FEBRUARY 5, 2024
Bad hoax blood: Spearphish pivots to deepfake Zoom call, leads to swift exit of cash. The post CFO Deepfake Fools Staff — Fakers Steal $26M via Video appeared first on Security Boulevard.

WIRED Threat Level
FEBRUARY 5, 2024
“They had, quite swiftly, begun an algorithmic scrub of any narrative of the president suffering a health emergency, burying those stories.” An exclusive excerpt from 2054: A Novel.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

We Live Security
FEBRUARY 5, 2024
With Valentine’s Day almost upon us, here’s some timely advice on how to prevent scammers from stealing a lotmore than your heart.

Bleeping Computer
FEBRUARY 5, 2024
Hewlett Packard Enterprise (HPE) is investigating a potential new breach after a threat actor put allegedly stolen data up for sale on a hacking forum, claiming it contains HPE credentials and other sensitive information. [.

Security Boulevard
FEBRUARY 5, 2024
Understanding the Basics of GDPR Compliance Within the sphere of cybersecurity, significant strides were made as the European Union (EU) introduced an innovative legislative tool called the General Data Protection Regulation (GDPR), unveiled on May 25, 2018. This regulation highlights the EU's unified approach to bolster the control of its citizens over their personal details, [.

Bleeping Computer
FEBRUARY 5, 2024
An Ivanti Connect Secure and Ivanti Policy Secure server-side request forgery (SSRF) vulnerability tracked as CVE-2024-21893 is currently under mass exploitation by multiple attackers. [.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Security Boulevard
FEBRUARY 5, 2024
These two examples of of core principles should help any SecOps team improve their cloud security operations. The post Two Practical Examples of Modern Cloud SecOps appeared first on Security Boulevard.

Bleeping Computer
FEBRUARY 5, 2024
A threat group named 'ResumeLooters' has stolen the personal data of over two million job seekers after compromising 65 legitimate job listing and retail sites using SQL injection and cross-site scripting (XSS) attacks. [.

The Hacker News
FEBRUARY 5, 2024
A recently disclosed server-side request forgery (SSRF) vulnerability impacting Ivanti Connect Secure and Policy Secure products has come under mass exploitation. The Shadowserver Foundation said it observed exploitation attempts originating from more than 170 unique IP addresses that aim to establish a reverse shell, among others.

Penetration Testing
FEBRUARY 5, 2024
In January 2024, FortiGuard Labs uncovered a disturbing Excel document that served as the initial gateway to a sinister malware campaign. This campaign, tied to a Vietnamese-based hacking group previously identified in August and... The post Behind the Mask: Dissecting the Latest VBA Script Cyber Espionage appeared first on Penetration Testing.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

The Hacker News
FEBRUARY 5, 2024
The threat actor known as Patchwork likely used romance scam lures to trap victims in Pakistan and India, and infect their Android devices with a remote access trojan called VajraSpy.

Bleeping Computer
FEBRUARY 5, 2024
Secretary of State Antony J. Blinken announced today a new visa restriction policy that will enable the Department of State to ban those linked to commercial spyware from entering the United States. [.

The Hacker News
FEBRUARY 5, 2024
The U.S. State Department said it's implementing a new policy that imposes visa restrictions on individuals who are linked to the illegal use of commercial spyware to surveil civil society members. "The misuse of commercial spyware threatens privacy and freedoms of expression, peaceful assembly, and association," Secretary of State Antony Blinken said.

Google Security
FEBRUARY 5, 2024
Posted by Lars Bergstrom – Director, Android Platform Tools & Libraries and Chair of the Rust Foundation Board Back in 2021, we announced that Google was joining the Rust Foundation. At the time, Rust was already in wide use across Android and other Google products. Our announcement emphasized our commitment to improving the security reviews of Rust code and its interoperability with C++ code.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

The Hacker News
FEBRUARY 5, 2024
A significant challenge within cyber security at present is that there are a lot of risk management platforms available in the market, but only some deal with cyber risks in a very good way. The majority will shout alerts at the customer as and when they become apparent and cause great stress in the process.

Penetration Testing
FEBRUARY 5, 2024
Fortinet, a renowned name in the cybersecurity realm, recently alerted its customers to two critical OS command injection vulnerabilities in its FortiSIEM supervisor. These vulnerabilities tracked as CVE-2024-23108 and CVE-2024-23109, have sent shockwaves through... The post CVE-2024-23108 & CVE-2024-23109 (CVSS 10): Critical Command Injection Flaws in Fortinet FortiSIEM appeared first on Penetration Testing.

eSecurity Planet
FEBRUARY 5, 2024
Critical multi-platform vulnerabilities impacting diverse systems dominated the past week’s cybersecurity headlines. Juniper Networks released updates for the high-severity flaws in SRX and EX Series. A coding vulnerability in Microsoft’s Azure Pipelines affected 70,000 open-source projects. Linux distros faced a heap-based buffer overflow issue.

The Hacker News
FEBRUARY 5, 2024
A 42-year-old Belarusian and Cypriot national with alleged connections to the now-defunct cryptocurrency exchange BTC-e is facing charges related to money laundering and operating an unlicensed money services business. Aliaksandr Klimenka, who was arrested in Latvia on December 21, 2023, was extradited to the U.S. If convicted, he faces a maximum penalty of 25 years in prison.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content