Digital Car Keys Are Coming
Schneier on Security
NOVEMBER 28, 2023
Soon we will be able to unlock and start our cars from our phones. Let’s hope people are thinking about security.

Schneier on Security
NOVEMBER 28, 2023
Soon we will be able to unlock and start our cars from our phones. Let’s hope people are thinking about security.

Tech Republic Security
NOVEMBER 28, 2023
60% of Australian small businesses don’t survive a cyber breach. What can the overworked IT pros in small businesses do with limited budgets against the cyber crime wave?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
NOVEMBER 28, 2023
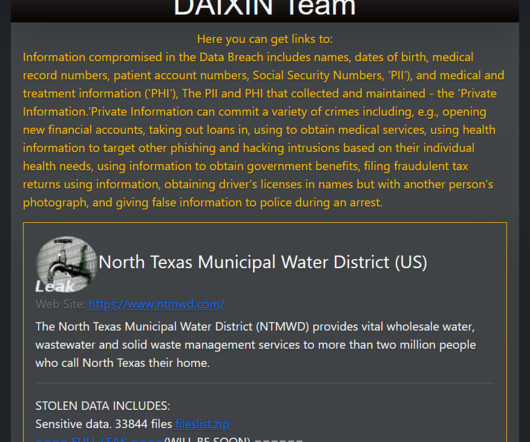
The Daixin Team group claims to have hacked the North Texas Municipal Water District (US) and threatened to leak the stolen data. The North Texas Municipal Water District (NTMWD) is a regional water district that provides wholesale water, wastewater treatment, and solid waste services to a group of member cities and customers in North Texas, United States.

Tech Republic Security
NOVEMBER 28, 2023
At AWS re:Invent, NVIDIA contributed GPUs to Amazon's cloud efforts and added a retriever system to its AI Enterprise Software platform on AWS Marketplace.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Affairs
NOVEMBER 28, 2023
An international law enforcement operation dismantled the core of a ransomware group operating from Ukraine. A joint law enforcement operation led by Europol and Eurojust, with the support of the police from seven nations, has arrested in Ukraine the core members of a ransomware group. Today EUROPOL in conjunction with the Ukraine National Police arrested individuals operating a ransomware group out of Ukraine.

WIRED Threat Level
NOVEMBER 28, 2023
Dozens of advocacy groups are pressuring the US Congress to abandon plans to ram through the renewal of a controversial surveillance program that they say poses an “alarming threat to civil rights.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

We Live Security
NOVEMBER 28, 2023
While it may be too late to introduce wholesale changes to your security policies, it doesn’t hurt to take a fresh look at where the biggest threats are and which best practices can help neutralize them

Security Affairs
NOVEMBER 28, 2023
Threat actors started exploiting a critical ownCloud vulnerability (CVE-2023-49103) that can lead to sensitive information disclosure. ownCloud is an open-source software platform designed for file synchronization and sharing. It allows individuals and organizations to create their own private cloud storage services, giving them control over their data while facilitating collaboration and file access across multiple devices.

Bleeping Computer
NOVEMBER 28, 2023
Researchers at Eurecom have developed six new attacks collectively named 'BLUFFS' that can break the secrecy of Bluetooth sessions, allowing for device impersonation and man-in-the-middle (MitM) attacks. [.

PCI perspectives
NOVEMBER 28, 2023
Risk analysis is a foundational tool to help organizations identify and prioritize potential threats and vulnerabilities within their environment. PCI DSS v4.0 introduced the concept of targeted risk analysis (TRA) with two different types of TRAs to provide entities with the flexibility to evaluate risk and determine the security impact of specific requirement controls, as appropriate for their environment.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
NOVEMBER 28, 2023
Google has fixed the sixth Chrome zero-day vulnerability this year in an emergency security update released today to counter ongoing exploitation in attacks. [.

Security Boulevard
NOVEMBER 28, 2023
Generative AI can help maintain a competitive advantage, but organizations should be mindful of the security and data privacy challenges of a new deployment. The post The Necessity of Security Best Practices When Implementing Generative AI appeared first on Security Boulevard.

Graham Cluley
NOVEMBER 28, 2023
Warnings are spreading on social media about NameDrop, a new way for iPhone users to quickly share their contact information with others. Should you be worried, and what should you do about it? Read more in my article on the Hot for Security blog.

Bleeping Computer
NOVEMBER 28, 2023
In cooperation with Europol and Eurojust, law enforcement agencies from seven nations have arrested in Ukraine the core members of a ransomware group linked to attacks against organizations in 71 countries. [.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Security Boulevard
NOVEMBER 28, 2023
The 32-year-old head of a threat group alleged to be responsible for ransomware attacks against corporations in 71 countries was arrested last week as part of a four-year investigation by European and U.S. law enforcement agencies. Arrested in Ukraine along with the unnamed ringleader were four other members of the group, which is accused of. The post Ringleader of Ransomware Group in Ukraine Arrested: Europol appeared first on Security Boulevard.

Bleeping Computer
NOVEMBER 28, 2023
Hackers are exploiting a critical ownCloud vulnerability tracked as CVE-2023-49103 that exposes admin passwords, mail server credentials, and license keys in containerized deployments. [.

Security Boulevard
NOVEMBER 28, 2023
A federal court in San Fransisco addressed whether the training of AI infringes copyright, and the decision has interesting implications for the technology's future. The post AI Gets a Legal Gift for Thanksgiving appeared first on Security Boulevard.

The Last Watchdog
NOVEMBER 28, 2023
San Francisco, Calif., Nov. 28, 2023 – AppDirect , the world’s leading B2B subscription commerce platform, today released key findings from its IT Business Leaders 2024 Outlook Report. The study, conducted by independent research firm Propeller Insights, dives into how IT business leaders feel about their security posture in a world where the technologies they embrace to grow and thrive are also vulnerable to constant and increasing threats.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Bleeping Computer
NOVEMBER 28, 2023
Google has fixed the fifth Chrome zero-day vulnerability this year in an emergency security update released today to counter ongoing exploitation in attacks. [.

Security Boulevard
NOVEMBER 28, 2023
In an era where digital assets have become an integral part of business operations, the need for a comprehensive cybersecurity plan has never been more critical. The digital realm is fraught with risks, and organizations must prioritize achieving their cyber security goals, which include protecting their valuable information and systems from unauthorized access, breaches, and … Defining Cyber Security Goals and Objectives: A Guide to Protecting Your Digital Empire Read More » The post Defining C

WIRED Threat Level
NOVEMBER 28, 2023
Musk’s recent use of the term “Q*Anon” is his most explicit endorsement of the movement to date. Conspiracists have since spent days dissecting its meaning and cheering on his apparent support.

The Hacker News
NOVEMBER 28, 2023
Google has rolled out security updates to fix seven security issues in its Chrome browser, including a zero-day that has come under active exploitation in the wild. Tracked as CVE-2023-6345, the high-severity vulnerability has been described as an integer overflow bug in Skia, an open source 2D graphics library.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Security Boulevard
NOVEMBER 28, 2023
Securing your organization’s information systems is a top priority in the ever-evolving digital landscape. Organizations face an ongoing battle against cyber threats; penetration testing is a powerful weapon to avoid these risks. The National Institute of Standards and Technology (NIST) Penetration Testing Framework, known as “nist pen testing,” offers a robust and structured approach to … Mastering NIST Penetration Testing: Your Essential Guide to Robust Cybersecurity Read More » The post Maste

Penetration Testing
NOVEMBER 28, 2023
In the world of data visualization and business intelligence, Apache Superset stands out as a modern, enterprise-ready web application. Renowned for its speed, lightness, and intuitive design, it empowers users across various skill levels... The post Critical Vulnerabilities Found in Apache Superset: Upgrade Urged appeared first on Penetration Testing.

Security Boulevard
NOVEMBER 28, 2023
Cybersecurity incidents are more than availability problems Malicious actors are using the legal process to their advantage Personal liability for cybersecurity mishandling is becoming more common Cybersecurity incidents, once dismissed as minor disruptions, have evolved into significant threats with far-reaching consequences. Initially seen as temporary setbacks, their impact on business operations was underestimated.

Graham Cluley
NOVEMBER 28, 2023
Join me, and the experts from JFrog, for a discussion about software supply chain security on December 5 2023.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

WIRED Threat Level
NOVEMBER 28, 2023
A WIRED analysis of more than 100 restricted channels shows these communities remain active, and content shared within them often spreads to channels accessible to the public.

The Hacker News
NOVEMBER 28, 2023
Cybersecurity researchers have detailed a "severe design flaw" in Google Workspace's domain-wide delegation (DWD) feature that could be exploited by threat actors to facilitate privilege escalation and obtain unauthorized access to Workspace APIs without super admin privileges.

Bleeping Computer
NOVEMBER 28, 2023
Today, Microsoft shared a temporary fix for a known issue causing Outlook Desktop to crash when sending emails from Outlook.com accounts. [.

The Last Watchdog
NOVEMBER 28, 2023
Boston, Mass. and Tel Aviv, Israel, Nov. 28, 2023 –A severe design flaw in Google Workspace’s domain-wide delegation feature discovered by threat hunting experts from Hunters’ Team Axon , can allow attackers to misuse existing delegations, enabling privilege escalation and unauthorized access to Workspace APIs without Super Admin privileges.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content