Surveillance Cameras Disguised as Clothes Hooks
Schneier on Security
DECEMBER 14, 2023
This seems like a bad idea. And there are ongoing lawsuits against Amazon for selling them.

Schneier on Security
DECEMBER 14, 2023
This seems like a bad idea. And there are ongoing lawsuits against Amazon for selling them.

The Last Watchdog
DECEMBER 14, 2023
Here’s the final installment of leading technologists sharing their observations about cybersecurity developments in the year that’s coming to a close — and the year to come. Last Watchdog posed two questions: •What should be my biggest takeaway from 2023, with respect to mitigating cyber risks at my organization? •What should I be most concerned about – and focus on – in 2024?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

We Live Security
DECEMBER 14, 2023
ESET researchers document a series of new OilRig downloaders, all relying on legitimate cloud service providers for C&C communications.

Security Affairs
DECEMBER 14, 2023
French police arrested a Russian national who is suspected of laundering money resulting from the criminal activity of the Hive ransomware gang. The French authorities arrested in Paris a Russian national who is suspected of laundering criminal proceeds for the Hive ransomware gang. “A Russian, suspected of having recovered in cryptocurrencies the money taken from French victims of the powerful Hive ransomware , dismantled in January, was arrested last week, AFP learned on Tuesday Decemb

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Bleeping Computer
DECEMBER 14, 2023
Since yesterday, customers of Ubiquiti networking devices, ranging from routers to security cameras, have reported seeing other people's devices and notifications through the company's cloud services. [.

Security Affairs
DECEMBER 14, 2023
Users of Ubiquiti WiFi products started reporting that they are accessing other people’s devices when logging into their accounts. Some users of Ubiquiti wifi products started reporting unexpected access to security camera footage, photos, and other devices upon logging into their accounts. Ubiquiti allows its customers to access and manage their devices through a proprietary cloud-based UniFi platform.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Security Affairs
DECEMBER 14, 2023
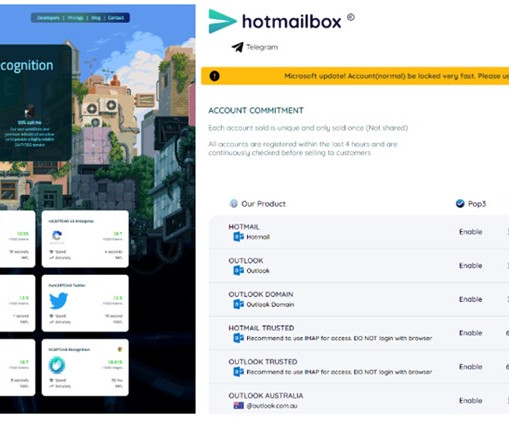
Microsoft’s Digital Crimes Unit seized multiple domains used by cybercrime group Storm-1152 to sell fraudulent Outlook accounts. Microsoft’s Digital Crimes Unit seized multiple domains used by a cybercrime group, tracked as Storm-1152, to sell fraudulent accounts. Storm-1152 operates illicit websites and social media pages, selling fake Microsoft accounts and tools to bypass identity verification software on popular technology platforms. “These services reduce the time and effo

SecureList
DECEMBER 14, 2023
During an incident response performed by Kaspersky’s Global Emergency Response Team ( GERT ) and GReAT, we uncovered a novel multiplatform threat named “NKAbuse” The malware utilizes NKN technology for data exchange between peers, functioning as a potent implant, and equipped with both flooder and backdoor capabilities. Written in Go, it is flexible enough to generate binaries compatible with various architectures.

Penetration Testing
DECEMBER 14, 2023
Subhunter A subdomain takeover occurs when an attacker gains control over a subdomain of a target domain. Typically, this happens when the subdomain has a canonical name (CNAME) in the Domain Name System (DNS),... The post Subhunter: A highly efficient and powerful subdomain takeover tool appeared first on Penetration Testing.

Duo's Security Blog
DECEMBER 14, 2023
An attack in action Logging into work on a typical day, John, an employee at Acme Corp. receives an email from the IT department. The email informs John that the company suffered a security breach, and it is essential for all employees to update their passwords immediately. John clicks the link provided, which takes him to a website that looks exactly like his company’s login page.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
DECEMBER 14, 2023
Kytch, the company that tried to fix McDonald’s broken ice cream machines, has unearthed a 3-year-old email it says proves claims of an alleged plot to undermine their business.

Security Boulevard
DECEMBER 14, 2023
Microsoft seized parts of the infrastructure of a prolific Vietnam-based threat group that the IT giant said was responsible for creating as many as 750 million fraudulent Microsoft accounts that were then sold to other bad actors and used to launch a range of cyberattacks – from ransomware to phishing to identity theft – against. The post Microsoft Targets Threat Group Behind Fake Accounts appeared first on Security Boulevard.

Security Affairs
DECEMBER 14, 2023
Russia-linked cyber espionage group APT29 has been targeting JetBrains TeamCity servers since September 2023. Experts warn that the Russia-linked APT29 group has been observed targeting JetBrains TeamCity servers to gain initial access to the targets’ networks. The APT29 group (aka SVR group , Cozy Bear , Nobelium , BlueBravo , Midnight Blizzard , and The Dukes ) exploited the flaw CVE-2023-42793 in TeamCity to carry out multiple malicious activities.

Trend Micro
DECEMBER 14, 2023
In this blog entry, we discuss the technical details of CVE-2023-50164, a critical vulnerability that affects Apache Struts 2 and enables unauthorized path traversal.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Graham Cluley
DECEMBER 14, 2023
Security researchers have discovered the latest evolution in call-back phishing campaigns. Read more in my article on the Tripwire State of Security blog.

Malwarebytes
DECEMBER 14, 2023
Reportedly , Apple has plans to make it harder for iPhone thieves to steal your personal information even if they have your device’s passcode. A new feature called Stolen Device Protection is included in the bet version of iOS 17.3. The feature limits access to your private information in case someone gets hold of both your iPhone and your passcode.

Digital Shadows
DECEMBER 14, 2023
The ReliaQuest Threat Research Team reveals predictions about prominent cyber threats in 2024, to help cybersecurity professionals prioritize and assign resources.

Malwarebytes
DECEMBER 14, 2023
Last week, we reported on how US government agencies have been asking Apple and Google for metadata related to push notifications, but the companies aren’t allowed to tell users about it happening. The content of the notifications is diverse. It ranges from a weather app warning you about rain to an alert that you have new mail, which often included the subject line and the sender.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Tech Republic Security
DECEMBER 14, 2023
Zero-trust security operates on the fundamental premise that trust should never be assumed, regardless of whether a user or device is inside or outside the corporate network. In this TechRepublic Premium guide, we will explore the benefits of incorporating zero-trust security into your organization’s cybersecurity framework to prevent data breaches and strengthen the protection of.

Bleeping Computer
DECEMBER 14, 2023
The Idaho National Laboratory (INL) confirmed that attackers stole the personal information of more than 45,000 individuals after breaching its cloud-based Oracle HCM HR management platform last month. [.

Identity IQ
DECEMBER 14, 2023
IDIQ Chief Marketing and Innovation Officer Michael Scheumack Joins the Identity Theft Resource Center’s Alliance for Identity Resilience Advisory Board IdentityIQ – IDIQ leadership to play a crucial role in advising the ITRC on combatting identity theft crime – TEMECULA, CA – December 13, 2023 – IDIQ ®, a leader in financial and identity protection, announced today that Michael Scheumack, IDIQ chief marketing and innovation officer, will be joining the Identity Theft Resource Center’s (IT

Digital Guardian
DECEMBER 14, 2023
In this blog we take a high level look at some of the vulnerabilities or flaws in a system that can lead to data loss, the stages of exploiting a vulnerability, the impact, and how to best safeguard your data against vulnerabilities.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Centraleyes
DECEMBER 14, 2023
What is DORA? DORA, or the Digital Operational Resilience Act , marks a transformative milestone in financial regulation. Published in the Official Journal of the European Union on December 27, 2022, DORA officially came into force on January 16, 2023, with its full implementation slated for January 17, 2025. The European Commission initially proposed this forward-looking regulatory framework in September 2020.

Penetration Testing
DECEMBER 14, 2023
Upload_Bypass Upload_Bypass is a powerful tool designed to assist Pentesters and Bug Hunters in testing file upload mechanisms. It leverages various bug bounty techniques to simplify the process of identifying and exploiting vulnerabilities, ensuring thorough... The post Upload_Bypass: File upload restrictions bypass appeared first on Penetration Testing.

Bleeping Computer
DECEMBER 14, 2023
Discord has made security key multi-factor authentication (MFA) available for all accounts on the platform, bringing significant security and anti-phishing benefits to its 500+ million registered users. [.

Veracode Security
DECEMBER 14, 2023
The landscape of coding is changing as developers embrace AI, automation, microservices, and third-party libraries to boost productivity. While each new approach enhances efficiency, like a double-edged sword, flaws and vulnerabilities are also introduced faster than teams can fix them. Learn about one of the latest innovations solving this in a recap of what our security experts discussed at AWS re:Invent 2023.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

The Hacker News
DECEMBER 14, 2023
Cybersecurity researchers have identified a set of 116 malicious packages on the Python Package Index (PyPI) repository that are designed to infect Windows and Linux systems with a custom backdoor. "In some cases, the final payload is a variant of the infamous W4SP Stealer, or a simple clipboard monitor to steal cryptocurrency, or both," ESET researchers Marc-Etienne M.

SecureWorld News
DECEMBER 14, 2023
In the rapidly evolving realm of global cybersecurity, there has been a growing alarm regarding China's military cyber prowess. An increase in documented cyber incidents implies that the People's Liberation Army is ramping up its attempts to breach vital U.S. infrastructure, such as power grids, water utilities, and transportation networks. A startling report by The Washington Post unveiled the depth of China's military cyber operations, signaling an escalating threat to critical U.S. infrastruc

Heimadal Security
DECEMBER 14, 2023
Dena, the reputed German Energy Agency, is said to have fallen victim to the notorious LockBit ransomware group. The Dena cyberattack was revealed through a post on the threat actor’s dark web platform, where they disclose data breach incidents and add affected entities to their growing victim list. LockBit Ransomware’s Message (source) Dena has previously […] The post LockBit Ransomware Targets German Energy Agency Dena appeared first on Heimdal Security Blog.

WIRED Threat Level
DECEMBER 14, 2023
Ten years in, Microsoft’s DCU has honed its strategy of using both unique legal tactics and the company’s technical reach to disrupt global cybercrime and state-backed actors.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content