Rare Interviews with Enigma Cryptanalyst Marian Rejewski
Schneier on Security
MAY 3, 2024
The Polish Embassy has posted a series of short interview segments with Marian Rejewski, the first person to crack the Enigma. Details from his biography.

Schneier on Security
MAY 3, 2024
The Polish Embassy has posted a series of short interview segments with Marian Rejewski, the first person to crack the Enigma. Details from his biography.

The Last Watchdog
MAY 3, 2024
Businesses today need protection from increasingly frequent and sophisticated DDoS attacks. Service providers, data center operators, and enterprises delivering critical infrastructure all face risks from attacks. Related: The care and feeding of DDoS defenses But to protect their networks, they’ll need to enable accurate attack detection while keeping operations manageable and efficient.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
MAY 3, 2024
I have spoken at several TED conferences over the years. TEDxPSU 2010: “ Reconceptualizing Security ” TEDxCambridge 2013: “ The Battle for Power on the Internet ” TEDMed 2016: “ Who Controls Your Medical Data ?” I’m putting this here because I want all three links in one place.

Tech Republic Security
MAY 3, 2024
According to the M-Trends report, the average time it takes for an organisation to detect an attacker in their environment has decreased from 16 days in 2022 to 10 days in 2023.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Penetration Testing
MAY 3, 2024
A significant security vulnerability has been identified in WordPress, the world’s most popular content management system, which could potentially allow attackers to take control of affected websites. The vulnerability, tracked as CVE-2024-4439 and rated... The post CVE-2024-4439: Unauthenticated Stored Cross-Site Scripting Vulnerability in WordPress Core appeared first on Penetration Testing.

Tech Republic Security
MAY 3, 2024
The U.K.'s National Cyber Security Centre, along with U.S. and Canadian cyber authorities, has identified a rise in attacks against OT operators since 2022.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
MAY 3, 2024
The year 2024 is bringing a return to stable tech salary growth in APAC, with AI and data jobs leading the way. This follows downward salary pressure in 2023, after steep increases in previous years.

Bleeping Computer
MAY 3, 2024
A Mullvad VPN user has discovered that Android devices leak DNS queries when switching VPN servers even though the "Always-on VPN" feature was enabled with the "Block connections without VPN" option. [.
Security Affairs
MAY 3, 2024
Zloader continues to evolve, its authors added an anti-analysis feature that was originally present in the Zeus banking trojan. Zloader (aka Terdot, DELoader, or Silent Night) is a modular trojan based on the leaked ZeuS source code. After a hiatus of almost two years, Zloader reappeared with new obfuscation techniques, domain generation algorithm (DGA), and network communication.

The Hacker News
MAY 3, 2024
Threat actors have been increasingly weaponizing Microsoft Graph API for malicious purposes with the aim of evading detection. This is done to "facilitate communications with command-and-control (C&C) infrastructure hosted on Microsoft cloud services," the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Security Affairs
MAY 3, 2024
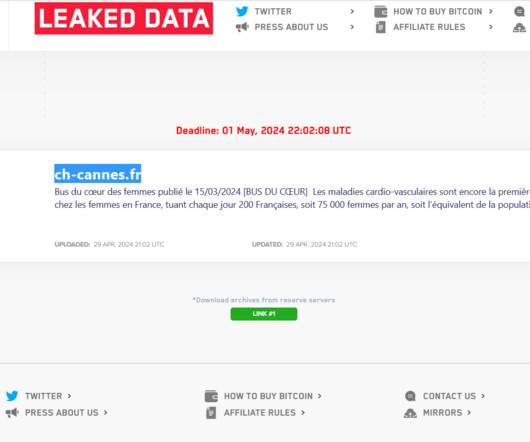
LockBit ransomware operators have published sensitive data allegedly stolen from the Simone Veil hospital in Cannes. In April, a cyber attack hit the Hospital Simone Veil in Cannes (CHC-SV), impacting medical procedures and forcing personnel to return to pen and paper. Non-urgent surgical procedures and consultations scheduled at the time of the attack were postponed.

The Last Watchdog
MAY 3, 2024
SAN FRANCISCO — On the eve of what promises to be a news-packed RSA Conference 2024 , opening here on Monday, Microsoft is putting its money where its mouth is. Related: Shedding light on LLM vulnerabilities More precisely the software titan is putting money within reach of its senior executives’ mouths. Screenshot In a huge development, Microsoft announced today that it is revising its security practices, organizational structure, and, most importantly, its executive compensation in an at

Bleeping Computer
MAY 3, 2024
Microsoft announced that Windows users can now log into their Microsoft consumer accounts using a passkey, allowing users to authenticate using password-less methods such as Windows Hello, FIDO2 security keys, biometric data (facial scans or fingerprints), or device PINs. [.

The Hacker News
MAY 3, 2024
The U.S. government on Thursday published a new cybersecurity advisory warning of North Korean threat actors' attempts to send emails in a manner that makes them appear like they are from legitimate and trusted parties. The joint bulletin was published by the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Department of State.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Bleeping Computer
MAY 3, 2024
The NSA and FBI warned that the APT43 North Korea-linked hacking group exploits weak email Domain-based Message Authentication Reporting and Conformance (DMARC) policies to mask spearphishing attacks. [.

Security Affairs
MAY 3, 2024
Microsoft devised an attack technique, dubbed ‘Dirty Stream,’ impacting widely used Android applications, billions of installations are at risk. Microsoft is warning Android users about a new attack technique, named Dirty Stream, that can allow threat actors to take control of apps and steal sensitive data. The IT giant describes Dirty Stream as an attack pattern, linked to path traversal, that affects various popular Android apps.

WIRED Threat Level
MAY 3, 2024
“Yahoo Boy” cybercriminals are openly running dozens of scams across Facebook, WhatsApp, Telegram, TikTok, YouTube, and more. And they’re not afraid to show it off online.
Security Affairs
MAY 3, 2024
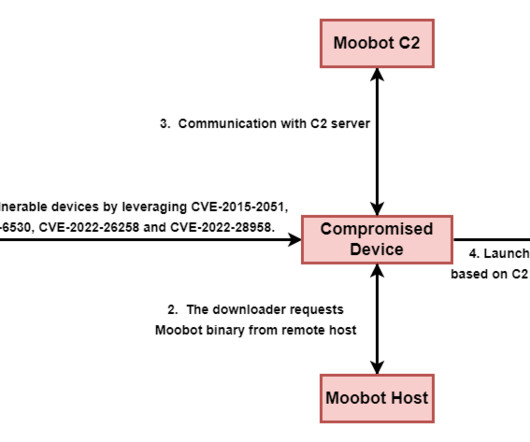
The Ubiquiti EdgeRouter botnet is still used by Russia-linked group APT28 and cybercriminals organizations. Trend Micro researchers reported that the EdgeRouter botnet , called Moobot , used by the APT28 group is still active and is also used by cyber criminal organizations. In January, the Federal Bureau of Investigation (FBI), National Security Agency (NSA), US Cyber Command, and international partners released a joint Cybersecurity Advisory (CSA) to warn that Russia-linked threat actors are u

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Security Boulevard
MAY 3, 2024
In a digital+ world, there is no escaping “vulnerabilities.” As software development grows more complex and APIs become more central to new software architectures, vulnerabilities can stem from various sources, whether it’s an issue within open-source components or a mistake made by one of your developers. The critical question we need to address is: what […] The post Understanding the Link Between API Exposure and Vulnerability Risks appeared first on OX Security.

Bleeping Computer
MAY 3, 2024
Google has rolled back a recent release of its reCaptcha captcha script after a bug caused the service to no longer work on Firefox for Windows. [.

Malwarebytes
MAY 3, 2024
Microsoft is rolling out passkey support for all consumer accounts. Passkeys are a very secure replacement for passwords that can’t be cracked, guessed or phished, and let you log in easily, without having to type a password every time. After enabling them in Windows 11 last year, Microsoft account owners can now generate passkeys across multiple platforms including Windows, Android, and iOS.

The Hacker News
MAY 3, 2024
In today's rapidly evolving digital landscape, the threat of Distributed Denial of Service (DDoS) attacks looms more significant than ever. As these cyber threats grow in sophistication, understanding and countering them becomes crucial for any business seeking to protect its online presence.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

Bleeping Computer
MAY 3, 2024
A Mullvad VPN user has discovered that Android devices leak DNS queries when switching VPN servers even though the "Always-on VPN" feature was enabled with the "Block connections without VPN" option. [.

The Hacker News
MAY 3, 2024
SaaS applications are dominating the corporate landscape. Their increased use enables organizations to push the boundaries of technology and business. At the same time, these applications also pose a new security risk that security leaders need to address, since the existing security stack does not enable complete control or comprehensive monitoring of their usage.

Penetration Testing
MAY 3, 2024
BadExclusions Now With Better Opsec BadExclusionsNWBO is an evolution from BadExclusions to identify folder custom or undocumented exclusions on AV/EDR. How it works? BadExclusionsNWBO copies and runs Hook_Checker.exe in all folders and subfolders of... The post BadExclusionsNWBO: identify folder custom or undocumented exclusions on AV/EDR appeared first on Penetration Testing.

Security Boulevard
MAY 3, 2024
Failure to configure authentication allowed malicious actors to exploit Airsoftc3.com's database, exposing the sensitive data of a vast number of the gaming site's users. The post Airsoft Data Breach Exposes Data of 75,000 Players appeared first on Security Boulevard.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.

Penetration Testing
MAY 3, 2024
Hackers are actively exploiting a vulnerability in the LiteSpeed Cache Plugin for WordPress, a tool currently installed on over 5 million websites worldwide. The vulnerability, known as CVE-2023-40000, allows attackers to create administrative accounts,... The post WordPress Sites Under Widespread Attack – LiteSpeed Cache Plugin Exploit Puts Millions at Risk appeared first on Penetration Testing.

Security Boulevard
MAY 3, 2024
This year, virtual CISOs must begin making a difference in our industry. For the longest time, small and medium businesses (SMBs) have been abandoned by the cybersecurity industry. But, SMBs need security leaders to guide them through the maze of cyber risk and craft practical strategies that align with their unique ever-evolving business objectives.

Penetration Testing
MAY 3, 2024
Nvidia has released a security advisory addressing critical vulnerabilities in its Triton Inference Server, a widely-used platform that streamlines AI inferencing across various environments, including cloud, data centers, and edge devices. The vulnerabilities, if... The post CVE-2024-0087: NVIDIA Releases Security Patch for Critical Flaw in Triton Inference Server appeared first on Penetration Testing.

Security Boulevard
MAY 3, 2024
Prisma SASE 3.0 promises to make it simpler and faster to apply zero-trust policies. The post Palo Alto Networks Extends SASE Reach to Unmanaged Devices appeared first on Security Boulevard.

Advertisement
Leverage the Cloud Development Environment Maturity Model to elevate your software development practices with scalable, secure cloud-based workspaces. This model offers a structured approach to modernizing development, aligning technology, developer experience, security, and workflows. By implementing Cloud Development Environments (CDEs), teams can boost efficiency, improve security, and streamline operations through centralized governance.
Let's personalize your content