The Story of the Mirai Botnet
Schneier on Security
JANUARY 16, 2024
Over at Wired, Andy Greenberg has an excellent story about the creators of the 2016 Mirai botnet.

Schneier on Security
JANUARY 16, 2024
Over at Wired, Andy Greenberg has an excellent story about the creators of the 2016 Mirai botnet.

Tech Republic Security
JANUARY 16, 2024
Small and midsize businesses are increasingly being targeted by cybercriminals — but they often lack the resources and expertise to develop comprehensive security policies to help defend against threats. This set of policies from TechRepublic Premium will help your company establish guidelines and procedures to reduce the risks. The pack comprises seven documents: IT Staff.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Penetration Testing
JANUARY 16, 2024
A new threat looms large for users of Confluence Data Center and Confluence Server, marked by the alarming designation CVE-2023-22527. This vulnerability, with a CVSS score of 10, signifies the highest level of severity... The post CVE-2023-22527 (CVSS 10): Critical RCE Flaw in Confluence Data Center and Server appeared first on Penetration Testing.

Tech Republic Security
JANUARY 16, 2024
Data in transit means data is at risk if the proper precautions aren’t followed. Data stored inside a securely monitored environment is much less likely to fall into the wrong hands than data exchanged between people and systems. With this in mind, it is essential for company personnel to adhere to firm and clear guidelines.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
JANUARY 16, 2024
Patching every device affected by the LeftoverLocals vulnerability—which includes some iPhones, iPads, and Macs—may prove difficult.

We Live Security
JANUARY 16, 2024
By eliminating these mistakes and blind spots, your organization can take massive strides towards optimizing its use of cloud without exposing itself to cyber-risk
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Affairs
JANUARY 16, 2024
Google has addressed the first Chrome zero-day vulnerability of the year that is actively being exploited in the wild. Google has released security updates to address the first Chrome zero-day vulnerability of the year that is actively being exploited in the wild. The high-serverity vulnerability, tracked as CVE-2024-0519 , is an out of bounds memory access in the Chrome JavaScript engine.

SecureList
JANUARY 16, 2024
Introduction In the ever-evolving landscape of mobile security, hunting for malware in the iOS ecosystem is akin to navigating a labyrinth with invisible walls. Imagine having a digital compass that not only guides you through this maze, but also reveals the hidden mechanisms of iOS malware previously shrouded in mystery. This is not a tool – this is the nature of digital forensic artifacts.

Security Affairs
JANUARY 16, 2024
Atlassian warns of a critical remote code execution issue in Confluence Data Center and Confluence Server that impacts older versions. Atlassian warns of a critical remote code execution vulnerability, tracked as CVE-2023-22527 (CVSS score 10.0), in Confluence Data Center and Confluence Server that impacts older versions. The vulnerability is a template injection vulnerability that can allow remote attackers to execute arbitrary code on vulnerable Confluence installs.

Malwarebytes
JANUARY 16, 2024
GitLab has issued a warning about a critical vulnerability in GitLab Community Edition (CE) and Enterprise Edition (EE). GitLab is an online DevOps platform that allows developers to collaborate on creating software. Organizations have a choice to install GitLab on their own server(s) or under GitLab’s control on GitLab.com. The vulnerability allows a successful attacker to easily take over users’ accounts without any interaction.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
JANUARY 16, 2024
VMware warns customers of a critical vulnerability impacting its Aria Automation multi-cloud infrastructure automation platform. VMware Aria Automation (formerly vRealize Automation ) is a modern cloud automation platform that simplifies and streamlines the deployment, management, and governance of cloud infrastructure and applications. It provides a unified platform for automating tasks across multiple cloud environments, including VMware Cloud on AWS, VMware Cloud on Azure, and VMware Cloud Fo

Bleeping Computer
JANUARY 16, 2024
Google has released security updates to fix the first Chrome zero-day vulnerability exploited in the wild since the start of the year. [.
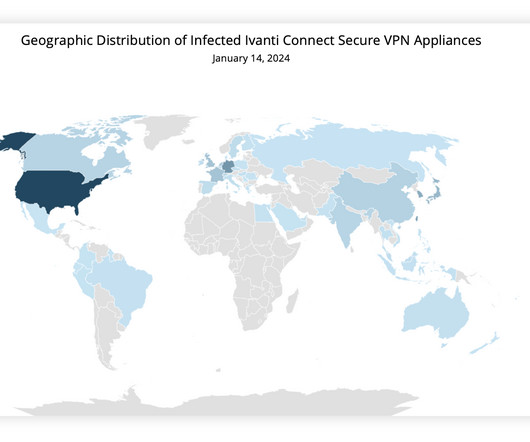
Security Affairs
JANUARY 16, 2024
Experts warn that recently disclosed Ivanti Connect Secure VPN and Policy Secure vulnerabilities are massively exploited in the wild. Last week, software firm Ivanti reported that threat actors are exploiting two zero-day vulnerabilities (CVE-2023-46805, CVE-2024-21887) in Connect Secure (ICS) and Policy Secure to remotely execute arbitrary commands on targeted gateways.

Malwarebytes
JANUARY 16, 2024
This week on the Lock and Code podcast… On Thursday, December 28, at 8:30 pm in the Utah town of Riverdale, the city police began investigating what they believed was a kidnapping. 17-year-old foreign exchange student Kai Zhuang was missing, and according to Riverdale Police Chief Casey Warren , Zhuang was believed to be “forcefully taken” from his home, and “being held against his will.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

WIRED Threat Level
JANUARY 16, 2024
The FTC forced a data broker to stop selling “sensitive location data.” But most companies can avoid such scrutiny by doing the bare minimum, exposing the lack of protections Americans truly have.

Penetration Testing
JANUARY 16, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a stern warning that’s reverberating through the web development community. The addition of a high-severity flaw in the Laravel Framework to its Known Exploited... The post CISA Warns of Actively Exploited Laravel Framework RCE Flaw appeared first on Penetration Testing.

Jane Frankland
JANUARY 16, 2024
In last week’s blog I started to explore the pros and cons of using an MDR provider and whether it’s better choosing a boutique provider over that of a traditional big brand. I began by discussing the first core feature – technology – I believe you should consider, along with the benefits and potential drawbacks. This week, I’m focused on the second feature – contract terms.

Malwarebytes
JANUARY 16, 2024
On January 4, 2017, Case Western Reserve University (CWRU), located in Cleveland, Ohio, became aware of an infection on more than 100 of its computers. The university was notified by an undisclosed third party, who provided information to help the team find and identify the malware. CWRU began working with the FBI, who determined that the systems had been infected for several years.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

NetSpi Executives
JANUARY 16, 2024
You’re about to have your first Red Team experience, or maybe your first one in the CISO seat of your organization. Maybe it’s just been a little while since your last one and you are curious how this one will go, what the Red Team will find, how your Blue Team will handle it, and what the longer tail takeaways post-engagement will be like. But before you begin, it’s important to consider: What am I not thinking about?

Bleeping Computer
JANUARY 16, 2024
Citrix urged customers on Tuesday to immediately patch Netscaler ADC and Gateway appliances exposed online against two actively exploited zero-day vulnerabilities. [.

Malwarebytes
JANUARY 16, 2024
This week on the Lock and Code podcast… On Thursday, December 28, at 8:30 pm in the Utah town of Riverdale, the city police began investigating what they believed was a kidnapping. 17-year-old foreign exchange student Kai Zhuang was missing, and according to Riverdale Police Chief Casey Warren , Zhuang was believed to be “forcefully taken” from his home, and “being held against his will.

Penetration Testing
JANUARY 16, 2024
In the intricate web of modern computing, the Linux kernel stands as a foundational element, powering systems worldwide. However, even the most robust structures have the weakness. Recently, two vulnerabilities were found in the... The post CVE-2024-0562 & CVE-2024-0565: The Linux Kernel Faces Two Major Vulnerabilities appeared first on Penetration Testing.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Security Boulevard
JANUARY 16, 2024
Taking a hands-off approach to cybersecurity is no longer good enough for any organization. In. The post Why the US Needs Comprehensive Cybersecurity Legislation appeared first on Security Boulevard.

The Hacker News
JANUARY 16, 2024
Google on Tuesday released updates to fix four security issues in its Chrome browser, including an actively exploited zero-day flaw. The issue, tracked as CVE-2024-0519, concerns an out-of-bounds memory access in the V8 JavaScript and WebAssembly engine, which can be weaponized by threat actors to trigger a crash.

Security Boulevard
JANUARY 16, 2024
Welcome to the world of online/digital privacy! Like its sister guide for cybersecurity, this privacy guide was written for complete privacy novices in mind. It is designed to be a starting point for anyone new to the world of online privacy. It also contains actionable advice for getting started on your privacy journey without the need for threat modeling (though it is certainly advised to set a direction for your efforts eventually.

The Hacker News
JANUARY 16, 2024
Citrix is warning of two zero-day security vulnerabilities in NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway) that are being actively exploited in the wild. The flaws are listed below - CVE-2023-6548 (CVSS score: 5.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

Security Boulevard
JANUARY 16, 2024
The volume of online scams relating to healthcare emanating from inexpensive TLDs is spiking—accounting for as much as 60% of daily domain registrations. The post Netcraft Report Surfaces Spike in Online Healthcare Product Scams appeared first on Security Boulevard.

The Hacker News
JANUARY 16, 2024
GitHub has revealed that it has rotated some keys in response to a security vulnerability that could be potentially exploited to gain access to credentials within a production container.

Penetration Testing
JANUARY 16, 2024
On Tuesday, Google rolled out a crucial update to patch a zero-day flaw in its widely-used Chrome browser. Tagged as CVE-2024-0519, this high-severity loophole marks the year’s first major security challenge for the popular... The post CVE-2024-0519: Google Chrome’s Latest Zero-Day Vulnerability appeared first on Penetration Testing.

The Hacker News
JANUARY 16, 2024
Over 178,000 SonicWall firewalls exposed over the internet are exploitable to at least one of the two security flaws that could be potentially exploited to cause a denial-of-service (DoS) condition and remote code execution (RCE).

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content