Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies
Security Affairs
JANUARY 1, 2024
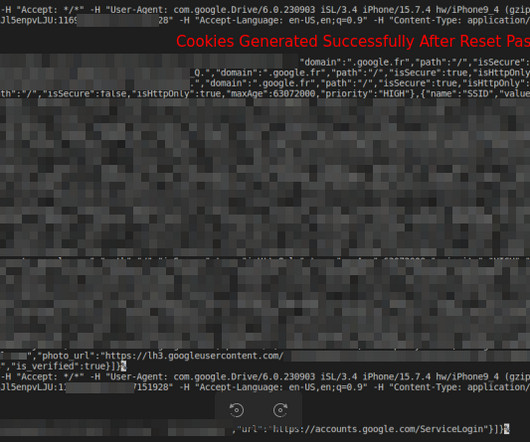
CloudSEK researchers analyzed a zero-day exploit that can allow the generation of persistent Google cookies through token manipulation. In October 2023, a developer known as PRISMA first uncovered an exploit that allows the generation of persistent Google cookies through token manipulation. An attacker can use the exploit to access Google services, even after a user’s password reset.








































Let's personalize your content