AI Voice Scam
Schneier on Security
MAY 1, 2024
Scammers tricked a company into believing they were dealing with a BBC presenter. They faked her voice, and accepted money intended for her.

Schneier on Security
MAY 1, 2024
Scammers tricked a company into believing they were dealing with a BBC presenter. They faked her voice, and accepted money intended for her.

Tech Republic Security
MAY 1, 2024
Researchers can earn up to $10,000 for critical vulnerabilities in the generative AI products.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Hacker News
MAY 1, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited Vulnerabilities (KEV) catalog, owing to active exploitation in the wild. Tracked as CVE-2023-7028 (CVSS score: 10.

Tech Republic Security
MAY 1, 2024
Are virtual private networks legal to use? Discover if VPNs are legal, restricted or banned in your geolocation and what activities are legal vs. illegal when using a VPN.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Bleeping Computer
MAY 1, 2024
Microsoft says the April 2024 Windows security updates break VPN connections on Windows 11, Windows 10, and Windows Server systems. [.

The Hacker News
MAY 1, 2024
A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
MAY 1, 2024
Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPress sites as relays for its actual command-and-control (C2) servers for detection evasion. The malware, codenamed Wpeeper, is an ELF binary that leverages the HTTPS protocol to secure its C2 communications.

Security Affairs
MAY 1, 2024
A flaw in the R programming language enables the execution of arbitrary code when parsing specially crafted RDS and RDX files. A vulnerability, tracked as CVE-2024-27322 (CVSS v3: 8.8), in the R programming language could allow arbitrary code execution upon deserializing specially crafted R Data Serialization (RDS) or R package files (RDX). R is an open-source programming language widely used for statistical computing and graphics.

The Hacker News
MAY 1, 2024
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from HTTP GET and POST requests.

Bleeping Computer
MAY 1, 2024
Cloud storage firm DropBox says hackers breached production systems for its DropBox Sign eSignature platform and gained access to authentication tokens, MFA keys, hashed passwords, and customer information. [.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Hacker News
MAY 1, 2024
The authors behind the resurfaced ZLoader malware have added a feature that was originally present in the Zeus banking trojan that it's based on, indicating that it's being actively developed. "The latest version, 2.4.1.

Security Affairs
MAY 1, 2024
Panda Restaurant Group disclosed a data breach that occurred in March, resulting in the theft of associates’ personal information. Panda Restaurant Group disclosed a data breach that occurred in March, resulting in the theft of personal information belonging to its associates. Panda Restaurant Group , Inc. is the parent company of Panda Inn, Panda Express and Hibachi-San.

Bleeping Computer
MAY 1, 2024
A new malware named 'Cuttlefish' has been spotted infecting enterprise-grade and small office/home office (SOHO) routers to monitor data that passes through them and steal authentication information. [.

Security Affairs
MAY 1, 2024
A former U.S. NSA employee has been sentenced to nearly 22 years in prison for attempting to sell classified documents to Russia. Jareh Sebastian Dalke (32), of Colorado Springs, is a former employee of the U.S. National Security Agency (NSA) who has been sentenced to nearly 22 years (262 months) in prison for attempting to transmit classified National Defense Information (NDI) to Russia.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Bleeping Computer
MAY 1, 2024
Microsoft has confirmed customer reports of NTLM authentication failures and high load after installing last month's Windows Server security updates. [.
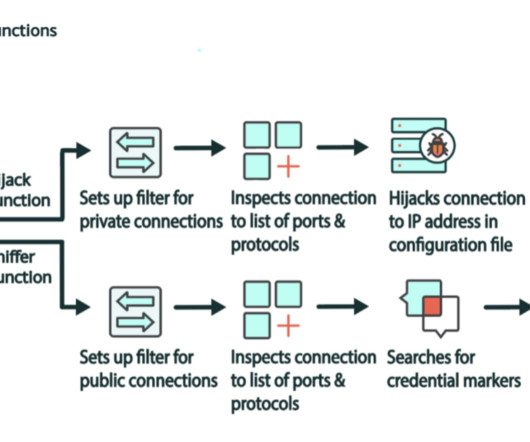
Security Affairs
MAY 1, 2024
A new malware named Cuttlefish targets enterprise-grade and small office/home office (SOHO) routers to harvest public cloud authentication data. Researchers at Lumen’s Black Lotus Labs discovered a new malware family, named Cuttlefish, which targets enterprise-grade and small office/home office (SOHO) routers to harvest public cloud authentication data from internet traffic.

The Last Watchdog
MAY 1, 2024
At the close of 2019, API security was a concern, though not necessarily a top priority for many CISOs. Related: GenAI ignites 100x innovation Then Covid 19 hit, and API growth skyrocketed, a trajectory that only steepened when Generative AI ( GenAI ) and Large Language Models ( LLMs ) burst onto the scene. As RSA Conference 2024 gets underway next week at San Francisco’s Moscone Center, dealing with the privacy and security fall out of those back-to-back disruptive developments will command a l

Security Boulevard
MAY 1, 2024
Venafi today launched an initiative to help organizations prepare to implement and manage certificates based on the Transport Layer Security (TLS) protocol. The post Venafi Launches 90-Day TLS Certificate Renewal Initiative appeared first on Security Boulevard.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Penetration Testing
MAY 1, 2024
Security researchers at Lumen Technologies’ Black Lotus Labs have uncovered a sophisticated new malware campaign targeting enterprise-grade small office/home office (SOHO) routers. Dubbed “Cuttlefish,” the malware is designed to remain undetected while stealing sensitive... The post New Cuttlefish Malware Evades Detection, Targets SOHO Routers appeared first on Penetration Testing.

The Hacker News
MAY 1, 2024
There’s a natural human desire to avoid threatening scenarios. The irony, of course, is if you hope to attain any semblance of security, you’ve got to remain prepared to confront those very same threats. As a decision-maker for your organization, you know this well.

Penetration Testing
MAY 1, 2024
Recently, HPE Aruba Networking announced a comprehensive update to its ArubaOS software, targeting multiple critical vulnerabilities that could potentially allow attackers to execute arbitrary code remotely and cause denial-of-service conditions. The advisory details patches... The post HPE Aruba Networking Patches Critical Vulnerabilities in Mobility Controllers and Gateways appeared first on Penetration Testing.

SecureWorld News
MAY 1, 2024
The U.S. Department of the Treasury's Federal Insurance Office (FIO) announced a major new initiative this week to improve the insurance industry's capabilities around modeling and underwriting terrorism and catastrophic cyber risks. At the 2024 International Forum of Terrorism Risk (Re)Insurance Pools (IFTRIP) Annual Conference, where the FIO began its chairmanship, the office unveiled a partnership with the National Science Foundation (NSF) to establish an Industry-University Cooperative Resea

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Security Boulevard
MAY 1, 2024
The RSA Conference 2024 will kick off on May 6. Known as the “Oscars of Cybersecurity,” the RSAC Innovation Sandbox has become a benchmark for innovation in the cybersecurity industry. Today, let’s get to know the company P0 Security. Introduction of P0 Security P0 Security was established in California in 2022. The company provides services […] The post RSAC 2024 Innovation Sandbox | P0 Security’s Cloud Access Governance Platform appeared first on NSFOCUS, Inc., a global network and cyber

Penetration Testing
MAY 1, 2024
Dropbox confirmed a security breach on April 24th within its Dropbox Sign (formerly HelloSign) service, exposing customer data including email addresses, usernames, phone numbers, and hashed passwords. API keys, OAuth tokens, and authentication information... The post Dropbox Sign Data Breach: What You Need to Know and How to Protect Yourself appeared first on Penetration Testing.

Trend Micro
MAY 1, 2024
Cheap and easy access to AI makes it harder to detect state-sponsored and homegrown campaigns during this election year

Bleeping Computer
MAY 1, 2024
HPE Aruba Networking has issued its April 2024 security advisory detailing critical remote code execution (RCE) vulnerabilities impacting multiple versions of ArubaOS, its proprietary network operating system. [.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Penetration Testing
MAY 1, 2024
A significant security flaw has been discovered in the widely used XML-Crypto npm package, a tool integral to the cryptographic security of XML documents. This vulnerability, identified as CVE-2024-32962, carries the highest severity score... The post CVE-2024-32962 (CVSS 10): Critical Vulnerability in XML-Crypto Affects Millions appeared first on Penetration Testing.

Bleeping Computer
MAY 1, 2024
Panda Restaurant Group, the parent company of Panda Express, Panda Inn, and Hibachi-San, disclosed a data breach after attackers compromised its corporate systems in March and stole the personal information of an undisclosed number of individuals. [.

WIRED Threat Level
MAY 1, 2024
Blockchain analysis firm Elliptic, MIT, and IBM have released a new AI model—and the 200-million-transaction dataset it's trained on—that aims to spot the “shape” of bitcoin money laundering.

NSTIC
MAY 1, 2024
The U.S. Small Business Administration is celebrating National Small Business Week from April 28 - May 4, 2024. This week recognizes and celebrates the small business community’s significant contributions to the nation. Organizations across the country participate by hosting in-person and virtual events, recognizing small business leaders and change-makers, and highlighting resources that help the small business community more easily and efficiently start and scale their businesses.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content