22,000 CyberPanel Servers Exposed: Zero-Click RCE Vulnerability Discovered, PoC Published
Penetration Testing
OCTOBER 29, 2024
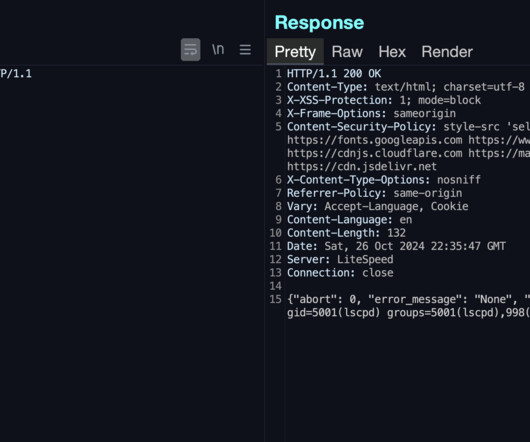
A new critical vulnerability has been discovered in CyberPanel, a popular open-source web hosting control panel, by security researcher DreyAnd. The flaw, a zero-click pre-authentication root remote code execution (RCE),... The post 22,000 CyberPanel Servers Exposed: Zero-Click RCE Vulnerability Discovered, PoC Published appeared first on Cybersecurity News.














Let's personalize your content