PoC Exploit Releases for Windows Elevation of Privilege Vulnerability CVE-2024-26230
Penetration Testing
SEPTEMBER 8, 2024
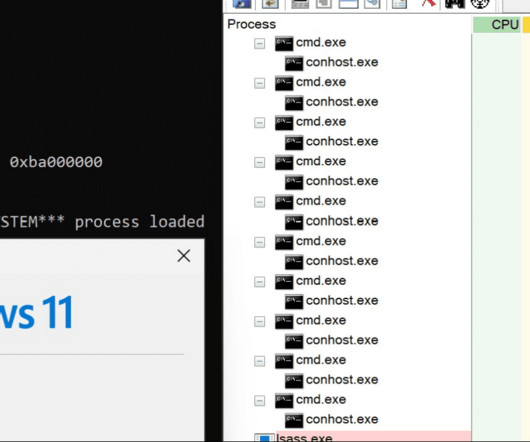
Security researcher published the technical details and a proof-of-concept (PoC) exploit for a patched elevation of privilege vulnerability in the Windows Telephony service tracked as CVE-2024-26230. This flaw, which has... The post PoC Exploit Releases for Windows Elevation of Privilege Vulnerability CVE-2024-26230 appeared first on Cybersecurity News.


















Let's personalize your content