US to Launch Cyber Trust Mark to Label Secure Smart Devices
Tech Republic Security
JANUARY 8, 2025
The Cyber Trust Mark will help consumers make more informed decisions about the cybersecurity of products, according to the White House.

Tech Republic Security
JANUARY 8, 2025
The Cyber Trust Mark will help consumers make more informed decisions about the cybersecurity of products, according to the White House.

Zero Day
JANUARY 8, 2025
The Accenture Technology Vision 2025 report explores how AI-powered autonomy is shaping technology development, customer experience, the physical world, and the future workforce, where people and AI agents work together to drive customer success.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
JANUARY 8, 2025
The White House announced the launch of the US Cyber Trust Mark which aims to help buyers make an informed choice about the purchase of wireless internet-connected devices, such as baby monitors, doorbells, thermostats, and more. The cybersecurity labeling program for wireless consumer Internet of Things (IoT) products is voluntary but the participants include several major manufacturers, retailers, and trade associations for popular electronics, appliances, and consumer products.

Zero Day
JANUARY 8, 2025
The latest updates for both browsers squash several high-severity security bugs. Here's how to grab them.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Penetration Testing
JANUARY 8, 2025
The open-source VPN software OpenVPN has patched three significant vulnerabilities in OpenVPN 2.6.11, released on June 21, 2024. The post CVE-2024-5594 (CVSS 9.1): Critical Vulnerability in OpenVPN Enables Code Execution appeared first on Cybersecurity News.

Zero Day
JANUARY 8, 2025
AI was featured in nearly every consumer tech category at CES. Here's what stood out.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Zero Day
JANUARY 8, 2025
If you like the idea of AI but don't want to share your content or information with a third party, you can always install an LLM on your Apple desktop or laptop. You'll be surprised at how easy it is.

Security Boulevard
JANUARY 8, 2025
IEI-IEI, Oh: Running an obsolete OS, on obsolete hardware, configured with obsolete settings. The post Insecure Medical Devices Illumina DNA Sequencer Illuminates Risks appeared first on Security Boulevard.

Zero Day
JANUARY 8, 2025
The most powerful desktop of all time will be arriving soon - and it will be running Linux.

The Hacker News
JANUARY 8, 2025
The European General Court on Wednesday fined the European Commission, the primary executive arm of the European Union responsible for proposing and enforcing laws for member states, for violating the bloc's own data privacy regulations. The development marks the first time the Commission has been held liable for infringing stringent data protection laws in the region.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Zero Day
JANUARY 8, 2025
The audio brand Audio-Technica announced the new ATH-CKS50TW2 earbuds at CES 2025.

The Hacker News
JANUARY 8, 2025
2024 had its fair share of high-profile cyber attacks, with companies as big as Dell and TicketMaster falling victim to data breaches and other infrastructure compromises. In 2025, this trend will continue. So, to be prepared for any kind of malware attack, every organization needs to know its cyber enemy in advance.

Zero Day
JANUARY 8, 2025
Our quest to go hands-on with every new laptop announced at CES has led us to these five picks, which stood out thanks to features, design, and value.

The Hacker News
JANUARY 8, 2025
The U.S. government on Tuesday announced the launch of the U.S. Cyber Trust Mark, a new cybersecurity safety label for Internet-of-Things (IoT) consumer devices. "IoT products can be susceptible to a range of security vulnerabilities," the U.S. Federal Communications Commission (FCC) said.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Zero Day
JANUARY 8, 2025
Smart home tech is one of the main events at CES and we've gathered the best you can find at the showcase.
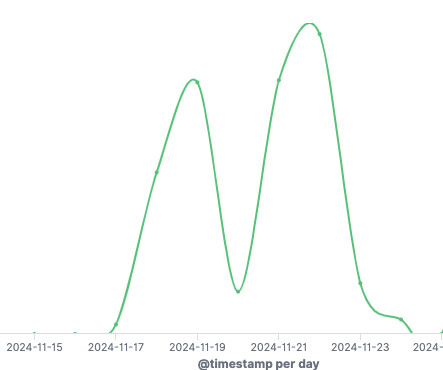
Security Affairs
JANUARY 8, 2025
Gayfemboy, a Mirai botnet variant, has been exploiting a flaw in Four-Faith industrial routers to launch DDoS attacks since November 2024. The Gayfemboy botnet was first identified in February 2024, it borrows the code from the basic Mirai variant and now integrates N-day and 0-day exploits. By November 2024, Gayfemboy exploited 0-day vulnerabilities in Four-Faith industrial routers and Neterbit routers and Vimar smart home devices, with over 15,000 daily active nodes.

The Hacker News
JANUARY 8, 2025
Cybersecurity researchers have found that bad actors are continuing to have success by spoofing sender email addresses as part of various malspam campaigns. Faking the sender address of an email is widely seen as an attempt to make the digital missive more legitimate and get past security mechanisms that could otherwise flag it as malicious.

NetSpi Technical
JANUARY 8, 2025
While everyone has been rushing to jump on the AI bandwagon, there has been a steady rise in AI/ML platforms that can be used in cloud service providers to run your data experiments. One of these platforms is the Azure Machine Learning (AML) service. The service is useful for handling large data processing tasks, as it seamlessly integrates with other Azure services that can feed it data.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Zero Day
JANUARY 8, 2025
I tried Halliday's AI smart glasses at CES 2025. With a display that's built into the frame - not the lens - they beat my Ray-Ban Metas in key ways.

The Hacker News
JANUARY 8, 2025
Cybersecurity researchers have shed light on a new remote access trojan called NonEuclid that allows bad actors to remotely control compromised Windows systems. "The NonEuclid remote access trojan (RAT), developed in C#, is a highly sophisticated malware offering unauthorised remote access with advanced evasion techniques," Cyfirma said in a technical analysis published last week.

Zero Day
JANUARY 8, 2025
If these smart glasses are any indication of what we're in for in 2025, it's going to be a wild ride.

SecureWorld News
JANUARY 8, 2025
The White House has officially launched the U.S. Cyber Trust Mark, a voluntary cybersecurity labeling program designed to help consumers make informed decisions about the security of their internet-connected devices. From baby monitors to home security systems, these IoT products have become integral to daily life, yet they also present significant cybersecurity risks.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Zero Day
JANUARY 8, 2025
Phishing is a form of social engineering where attackers try to get you to reveal your sensitive information through malicious links, SMS, QR codes, and more. Here's how to protect yourself in Chrome and Firefox.

Penetration Testing
JANUARY 8, 2025
Ivanti has issued a security advisory addressing two vulnerabilities in its Connect Secure, Policy Secure, and Neurons for The post CVE-2025-0282 (CVSS 9.0): Ivanti Confirms Active Exploitation of Critical Flaw appeared first on Cybersecurity News.

Zero Day
JANUARY 8, 2025
CES 2025 is in full swing, and there are plenty of audio products to check out. From open-ear headphones to booming sound systems, there's audio gear for everyone this year.

Penetration Testing
JANUARY 8, 2025
HPE Aruba Networking has issued a security advisory addressing multiple command injection vulnerabilities in its 501 Wireless Client The post CVE-2024-54006 & CVE-2024-54007: Command Injection Flaws in HPE Aruba Devices, PoC Publicly Available appeared first on Cybersecurity News.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

Zero Day
JANUARY 8, 2025
CES is in full swing, and we've seen major announcements from the likes of TCL, Roborock, MSI, and more. Here's our roundup of the new tech you don't want to miss.

Penetration Testing
JANUARY 8, 2025
Palo Alto Networks has issued a security advisory addressing multiple vulnerabilities in its Expedition migration tool, which could The post Mutiple Vulnerabilities Found in Palo Alto Networks Expedition Tool appeared first on Cybersecurity News.

Zero Day
JANUARY 8, 2025
We're at the final stretch of CES 2025, and we've seen major announcements from the likes of TCL, Roborock, Samsung, and more. Here's our roundup of the best tech you don't want to miss.

Penetration Testing
JANUARY 8, 2025
A detailed technical and a proof-of-concept (PoC) exploit code from security researcher Mickey Jin has unveiled a critical The post macOS Vulnerability CVE-2024-54527 Unveiled: TCC Bypass PoC Exploit Code Released appeared first on Cybersecurity News.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Let's personalize your content