MY TAKE: Fostering Digital Trust – the role of ‘post-quantum crypto’ and ‘crypto agility’ in 2024
The Last Watchdog
DECEMBER 13, 2023
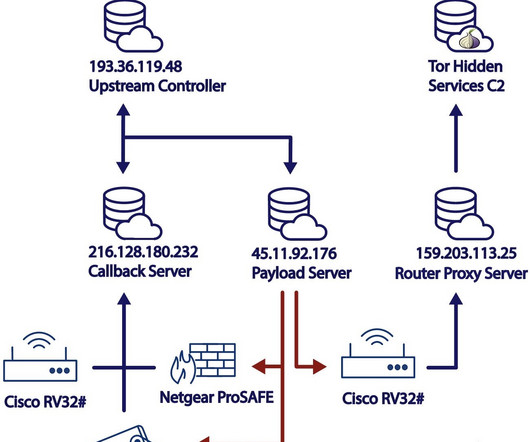
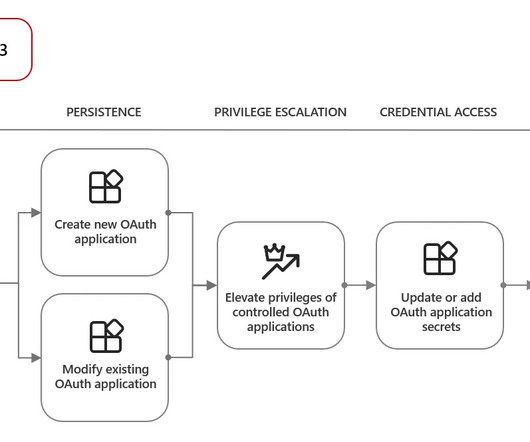
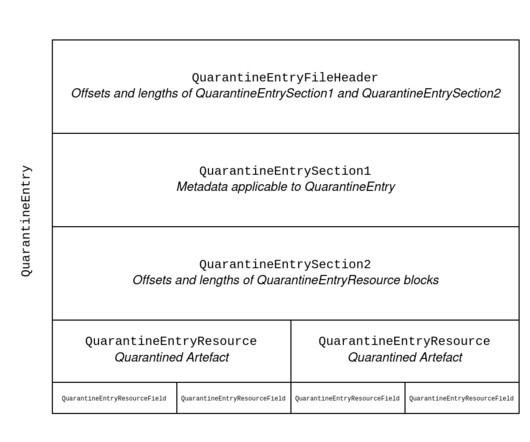
Notable progress was made in 2023 in the quest to elevate Digital Trust. Related: Why IoT standards matter Digital Trust refers to the level of confidence both businesses and consumers hold in digital products and services – not just that they are suitably reliable, but also that they are as private and secure as they need to be. We’re not yet at a level of Digital Trust needed to bring the next generation of connected IT into full fruition – and the target keeps moving.








































Let's personalize your content