How to Set Up & Use a VPN on Android (A Step-by-Step Guide)
Tech Republic Security
MAY 15, 2024
Trying to configure or set up a VPN on your Android? Learn how to get started with our step-by-step guide.

Tech Republic Security
MAY 15, 2024
Trying to configure or set up a VPN on your Android? Learn how to get started with our step-by-step guide.

The Hacker News
MAY 15, 2024
Google has rolled out fixes to address a set of nine security issues in its Chrome browser, including a new zero-day that has been exploited in the wild. Assigned the CVE identifier CVE-2024-4947, the vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
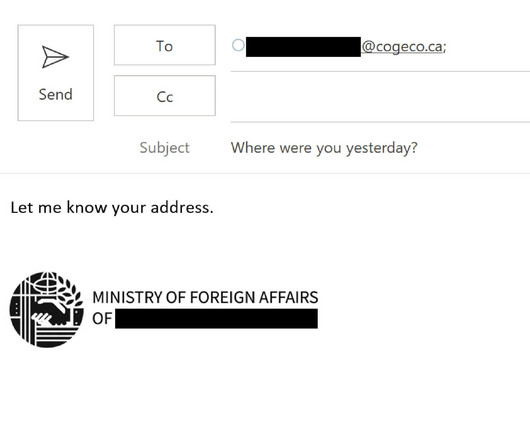
We Live Security
MAY 15, 2024
ESET researchers provide technical analysis of the Lunar toolset, likely used by the Turla APT group, that infiltrated a European ministry of foreign affairs

The Hacker News
MAY 15, 2024
Microsoft has addressed a total of 61 new security flaws in its software as part of its Patch Tuesday updates for May 2024, including two zero-days which have been actively exploited in the wild. Of the 61 flaws, one is rated Critical, 59 are rated Important, and one is rated Moderate in severity.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Trend Micro
MAY 15, 2024
This report describes how Waterbear and Deuterbear — two of the tools in Earth Hundun's arsenal — operate, based on a campaign from 2024.

The Hacker News
MAY 15, 2024
The Microsoft Threat Intelligence team said it has observed a threat it tracks under the name Storm-1811 abusing the client management tool Quick Assist to target users in social engineering attacks. "Storm-1811 is a financially motivated cybercriminal group known to deploy Black Basta ransomware," the company said in a report published on May 15, 2024.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
MAY 15, 2024
Law enforcement agencies have officially seized control of the notorious BreachForums platform, an online bazaar known for peddling stolen data, for the second time within a year. The website ("breachforums[.]st") has been replaced by a seizure banner stating the clearnet cybercrime forum is under the control of the Federal Bureau of Investigation (FBI).

Security Boulevard
MAY 15, 2024
Phish Ahoy! Hacker took advantage of Dell’s lack of anti-scraping defense. The post Dell Hell Redux — More Personal Info Stolen by ‘Menelik’ appeared first on Security Boulevard.
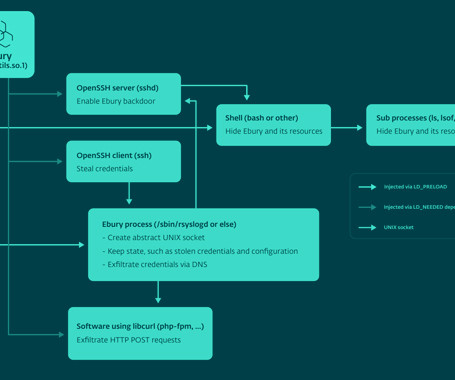
The Hacker News
MAY 15, 2024
A malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from Slovak cybersecurity firm ESET, which characterized it as one of the most advanced server-side malware campaigns for financial gain. "Ebury actors have been pursuing monetization activities [.

Malwarebytes
MAY 15, 2024
BreachForums—probably the largest dark web marketplace for stolen data to be leaked and sold—has been seized by law enforcement. Now, both the regular and the TOR domain of BreachForums are plastered with a message telling visitors the site is now under control of the FBI. The FBI said BreachForums and its predecessor Raidforums was: “…operating as a clear-net marketplace for cybercriminals to buy, sell, and trade contraband, including stolen access devices, means of identification, hackin

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Hacker News
MAY 15, 2024
Here’s How to Enhance Your Cyber Resilience with CVSS In late 2023, the Common Vulnerability Scoring System (CVSS) v4.0 was unveiled, succeeding the eight-year-old CVSS v3.0, with the aim to enhance vulnerability assessment for both industry and the public.

Security Affairs
MAY 15, 2024
Adobe addressed multiple code execution vulnerabilities in several products, including Adobe Acrobat and Reader. Adobe addressed multiple code execution vulnerabilities in its products, including Adobe Acrobat and Reader software The software giant released its Patch Tuesday updates to fix 35 security vulnerabilities 12 of these issues impact Adobe Acrobat and Reader software.
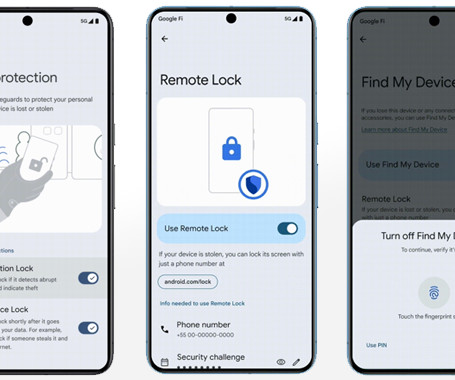
The Hacker News
MAY 15, 2024
Google has announced a slew of privacy and security features in Android, including a suite of advanced protection features to help secure users' devices and data in the event of a theft.

Security Affairs
MAY 15, 2024
One of the developers of the Tornado Cash cryptocurrency mixer has been sentenced to 64 months in prison. Alexey Pertsev (29), one of the main developers of the Tornado Cash cryptocurrency mixer has been sentenced to 64 months in prison for helping launder more than $2 billion worth of cryptocurrency. The mixers are essential components for cybercriminals that use them for money laundering, it was used to launder the funds stolen from the victims.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Hacker News
MAY 15, 2024
An unnamed European Ministry of Foreign Affairs (MFA) and its three diplomatic missions in the Middle East were targeted by two previously undocumented backdoors tracked as LunarWeb and LunarMail.

Duo's Security Blog
MAY 15, 2024
“The best way to break in is through the front door.” We’ve heard some version of this phrase many times over, whether it pertains to a bad actor physically breaking into a secured building or socially engineering an unsuspecting victim to provide access to protected information. The cybersecurity landscape is littered with front doors, while modern society’s reliance on digital technologies is only increasing.
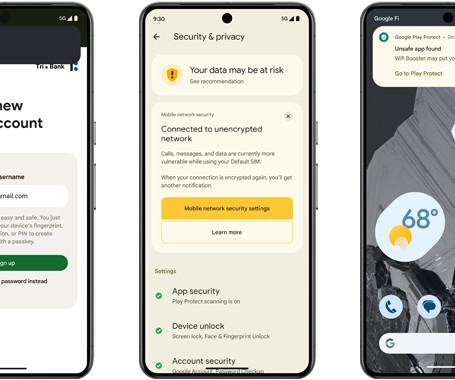
The Hacker News
MAY 15, 2024
Google is unveiling a set of new features in Android 15 to prevent malicious apps installed on the device from capturing sensitive data. This constitutes an update to the Play Integrity API that third-party app developers can take advantage of to secure their applications against malware.

Security Boulevard
MAY 15, 2024
The operators behind the Ebury server-side malware botnet have been doing business since at least 2009 and, according to the threat researchers who have been tracking it for the last decade, are stronger and more active than ever. The malware has compromised at least 400,000 Linux servers over the past 15 years, with about 100,000. The post 15-Year-Old Ebury Botnet Compromised 400,000 Linux Servers appeared first on Security Boulevard.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

The Hacker News
MAY 15, 2024
A Dutch court on Tuesday sentenced one of the co-founders of the now-sanctioned Tornado Cash cryptocurrency mixer service to 5 years and 4 months in prison. While the name of the defendant was redacted in the verdict, it's known that Alexey Pertsev, a 31-year-old Russian national, has been awaiting trial in the Netherlands on money laundering charges.

Bleeping Computer
MAY 15, 2024
The FBI has seized the notorious BreachForums hacking forum that leaked and sold stolen corporate data to other cybercriminals. [.

The Hacker News
MAY 15, 2024
While cloud adoption has been top of mind for many IT professionals for nearly a decade, it’s only in recent months, with industry changes and announcements from key players, that many recognize the time to make the move is now.

Digital Shadows
MAY 15, 2024
"Black Basta" ransomware group uses new email spam and vishing to spread malware. Learn more about protective measures for your organization.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Malwarebytes
MAY 15, 2024
Apple and Google have announced an industry specification for Bluetooth tracking devices which help alert users to unwanted tracking. The specification, called Detecting Unwanted Location Trackers , will make it possible to alert users across both iOS and Android if a device is unknowingly being used to track them. The alert would be pushed to the users device and would say “[Item] Found Moving With You.

SecureWorld News
MAY 15, 2024
Google has been forced to release an emergency security update for its Chrome browser just days after patching a previous Zero-Day vulnerability that was being actively exploited in the wild. This marks the sixth actively exploited Chrome Zero-Day addressed so far in 2024. The latest high-severity flaw is tracked as CVE-2024-4761 and stems from an out-of-bounds write vulnerability in Chrome's V8 JavaScript engine.

Bleeping Computer
MAY 15, 2024
Nissan North America (Nissan) suffered a data breach last year when a threat actor targeted the company's external VPN and shut down systems to receive a ransom. [.

Security Boulevard
MAY 15, 2024
In Microsoft’s May 2024 Patch Tuesday, the company reported significant updates aimed at enhancing the security of various systems by addressing a total of 61 vulnerabilities. This update is crucial, as it includes patches for one critical vulnerability and three zero-day vulnerabilities, with two of these zero-days actively exploited in the wild. The updates also encompass earlier fixes for six.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Penetration Testing
MAY 15, 2024
Cybersecurity firm Rapid7 has uncovered a widespread malvertising campaign that is actively targeting individuals searching for popular utilities like WinSCP and PuTTY. This sophisticated attack uses malicious ads on common search engines like Bing,... The post New Malvertising Campaign Leads to Ransomware Through Trojanized Installers of WinSCP and PuTTY appeared first on Penetration Testing.

Graham Cluley
MAY 15, 2024
Remember when a US mother was accused of distributing explicit deepfake photos and videos to try to get her teenage daughter's cheerleading rivals kicked off the team? Well, there has been a surprising development. And learn how cybercriminals have been stealing boomers' one-time-passcodes via a secretive online service. All this and more is discussed in the latest edition of the award-winning "Smashing Security" podcast by cybersecurity veterans Graham Cluley and Carole Theriault.
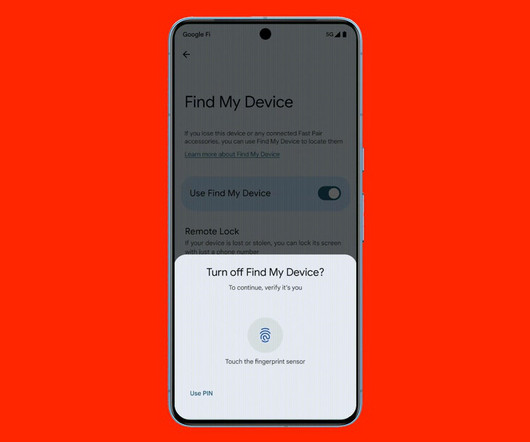
WIRED Threat Level
MAY 15, 2024
Google is introducing new AI-powered safety tools in Android 15 that can lock down your phone if thieves nab it.

Penetration Testing
MAY 15, 2024
The Git project, a cornerstone of software development, has recently addressed a series of critical security vulnerabilities that could expose users to remote code execution (CVE-2024-32002, CVE-2024-32004) and unauthorized data manipulation. Critical Flaws Discovered:... The post Git Patches Critical RCE Vulnerabilities – CVE-2024-32002 & CVE-2024-32004 appeared first on Penetration Testing.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content