Closer to the Edge: Hyperscaling Have I Been Pwned with Cloudflare Workers and Caching
Troy Hunt
NOVEMBER 20, 2024
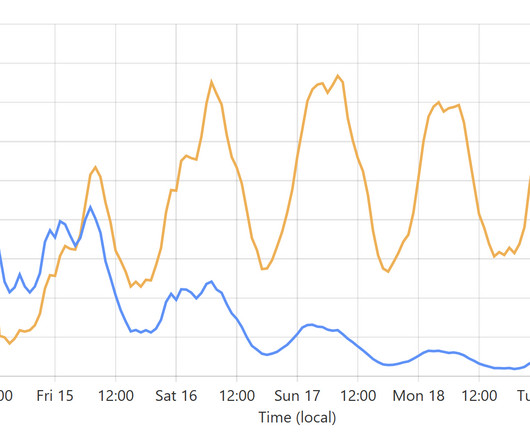
I've spent more than a decade now writing about how to make Have I Been Pwned (HIBP) fast. Really fast. Fast to the extent that sometimes, it was even too fast: The response from each search was coming back so quickly that the user wasn’t sure if it was legitimately checking subsequent addresses they entered or if there was a glitch. Over the years, the service has evolved to use emerging new techniques to not just make things fast, but make them scale more under load, increase avail










































Let's personalize your content