New Chrome Zero-Day
Schneier on Security
SEPTEMBER 10, 2024
According to Microsoft researchers, North Korean hackers have been using a Chrome zero-day exploit to steal cryptocurrency.

Schneier on Security
SEPTEMBER 10, 2024
According to Microsoft researchers, North Korean hackers have been using a Chrome zero-day exploit to steal cryptocurrency.

The Last Watchdog
SEPTEMBER 10, 2024
Singapore, Sept. 10, 2024, CyberNewsWire — Seventh Sense , a pioneer in advanced cybersecurity solutions, announces the launch of SenseCrypt , a revolutionary new platform that sets a new standard in secure, privacy-preserving identity verification. SenseCrypt introduces a first-of-its-kind face-based public key infrastructure (PKI) and electronic identity (eID) solution.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
SEPTEMBER 10, 2024
Microsoft Corp. today released updates to fix at least 79 security vulnerabilities in its Windows operating systems and related software, including multiple flaws that are already showing up in active attacks. Microsoft also corrected a critical bug that has caused some Windows 10 PCs to remain dangerously unpatched against actively exploited vulnerabilities for several months this year.

Tech Republic Security
SEPTEMBER 10, 2024
Microsoft will disable ActiveX controls by default in the Office suite, starting in October with the release of Office 2024.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Kali Linux
SEPTEMBER 10, 2024
With summer coming to an end, so are package migrations, and Kali 2024.3 can now be released. You can now start downloading or upgrading if you have an existing Kali installation. The summary of the changelog since the 2024.2 release from June is: Qualcomm NetHunter Pro Devices - Qualcomm Snapdragon SDM845 SoC now supported New Tools - 11x new tools in your arsenal Our focus has been on a lot of behind the scenes updates and optimizations since the last release.

Tech Republic Security
SEPTEMBER 10, 2024
A Mark of the Web security alert vulnerability and three others have been exploited in the wild and are now covered by Redmond’s monthly patch batch.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
SEPTEMBER 10, 2024
Microsoft on Tuesday disclosed that three new security flaws impacting the Windows platform have come under active exploitation as part of its Patch Tuesday update for September 2024. The monthly security release addresses a total of 79 vulnerabilities, of which seven are rated Critical, 71 are rated Important, and one is rated Moderate in severity.

The Last Watchdog
SEPTEMBER 10, 2024
Cary, NC, Sept. 10, 2024, CyberNewsWire — As cyber threats grow, small to medium-sized businesses (SMBs) are disproportionately targeted. According to the recent Hiscox annual cyber readiness report , 41% of SMBs in the US fell victim to a cyberattack in 2023, a figure that has nearly doubled since 2021. INE Security , a global leader in cybersecurity training and certifications, recognizes this as a critical issue and is leading an initiative for change by working with SMBs to bridge the

The Hacker News
SEPTEMBER 10, 2024
A new side-channel attack dubbed PIXHELL could be abused to target air-gapped computers by breaching the "audio gap" and exfiltrating sensitive information by taking advantage of the noise generated by the pixels on the screen. "Malware in the air-gap and audio-gap computers generates crafted pixel patterns that produce noise in the frequency range of 0 - 22 kHz," Dr.

Security Affairs
SEPTEMBER 10, 2024
Poland ‘s security officials announced that they successfully thwarted cyberattacks that were carried out by Russia and Belarus. Poland security services announced they have thwarted a cyber operation orchestrated by Russia and Belarus, aimed at destabilizing the country, according to Deputy Prime Minister and Minister for digital affairs Krzysztof Gawkowski. “The Belarusian and Russian foreign services… had a specific goal – to extort information, to blackmail individual

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
The Hacker News
SEPTEMBER 10, 2024
A trio of threat activity clusters linked to China has been observed compromising more government organizations in Southeast Asia as part of a renewed state-sponsored operation codenamed Crimson Palace, indicating an expansion in the scope of the espionage effort.

Security Affairs
SEPTEMBER 10, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds SonicWall SonicOS, ImageMagick and Linux Kernel bugs to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added SonicWall SonicOS, ImageMagick and Linux Kernel vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog.

The Hacker News
SEPTEMBER 10, 2024
Ivanti has released software updates to address multiple security flaws impacting Endpoint Manager (EPM), including 10 critical vulnerabilities that could result in remote code execution. A brief description of the issues is as follows - CVE-2024-29847 (CVSS score: 10.0) - A deserialization of untrusted data vulnerability that allows a remote unauthenticated attacker to achieve code execution.

Security Boulevard
SEPTEMBER 10, 2024
More than half (53%) of businesses in the U.S. and UK have been targeted by financial scams using deepfake technology, with 43% of those companies falling victim, according to a Medius survey of 1,533 finance professionals. The post AI-Powered Deepfake Scams Wreak Havoc on Businesses appeared first on Security Boulevard.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Hacker News
SEPTEMBER 10, 2024
The threat actor known as CosmicBeetle has debuted a new custom ransomware strain called ScRansom in attacks targeting small- and medium-sized businesses (SMBs) in Europe, Asia, Africa, and South America, while also likely working as an affiliate for RansomHub.
Security Affairs
SEPTEMBER 10, 2024
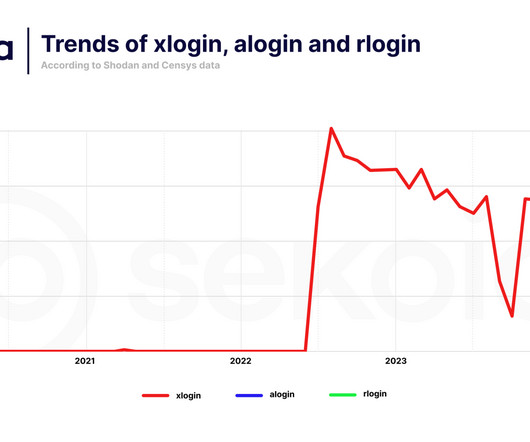
The Quad7 botnet evolves and targets new SOHO devices, including Axentra media servers, Ruckus wireless routers and Zyxel VPN appliances. The Sekoia TDR team identified additional implants associated with the Quad7 botnet operation. The botnet operators are targeting multiple SOHO devices and VPN appliances, including TP-LINK, Zyxel, Asus, D-Link, and Netgear, exploiting both known and previously unknown vulnerabilities.
The Hacker News
SEPTEMBER 10, 2024
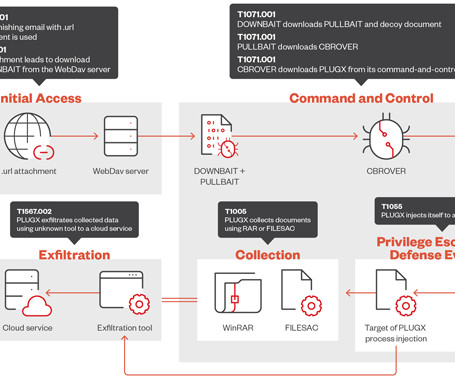
The threat actor tracked as Mustang Panda has refined its malware arsenal to include new tools in order to facilitate data exfiltration and the deployment of next-stage payloads, according to new findings from Trend Micro. The cybersecurity firm, which is monitoring the activity cluster under the name Earth Preta, said it observed "the propagation of PUBLOAD via a variant of the worm HIUPAN.

Malwarebytes
SEPTEMBER 10, 2024
Payment provider Slim CD has disclosed a security incident that may have exposed the full credit card information of anyone paying at a merchant that uses Slim CD’s services. The Florida-based gateway system, which allows merchants to take any kind of electronic payment, said on June 15 it noticed “suspicious activity” within its environment.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

The Hacker News
SEPTEMBER 10, 2024
Shadow apps, a segment of Shadow IT, are SaaS applications purchased without the knowledge of the security team. While these applications may be legitimate, they operate within the blind spots of the corporate security team and expose the company to attackers. Shadow apps may include instances of software that the company is already using.

SecureWorld News
SEPTEMBER 10, 2024
Avis Car Rental has begun notifying close to 300,000 individuals about a data breach that occurred in August 2024, resulting in the theft of sensitive personal information. The breach reportedly exposed customer names, addresses, driver license numbers, and other personal data. Following the discovery of the breach, Avis initiated an incident response plan, including engaging cybersecurity experts to assess the scope of the attack and bolster security.

Security Boulevard
SEPTEMBER 10, 2024
Manufacturing and industrial sectors are becoming bigger cyber-targets, and many of the intrusions are coming from China. Those are among the sobering takeaways from a report Tuesday by Ontinue’s Advanced Threat Operations team in its biannual Threat Intelligence Report. The two sectors endured a 105% increase in attacks during the first half of 2024, highlighting.

eSecurity Planet
SEPTEMBER 10, 2024
Air-gapped systems have long been the go-to solution for sensitive operations, especially in sectors like defense, finance, and critical infrastructure. These systems, disconnected from external networks, are believed to be nearly impervious to cyberattacks. However, the evolving landscape of cybersecurity threats has brought new methods to breach even these fortified digital fortresses.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Security Boulevard
SEPTEMBER 10, 2024
Just-in-time access has emerged as a game-changing approach to enhance the security posture of cloud environments. This innovative method aligns with the principle of least privilege, reducing the attack surface and minimizing potential security risks. The post Just-in-Time Access: Key Benefits for Cloud Platforms appeared first on Security Boulevard.

Malwarebytes
SEPTEMBER 10, 2024
As if they weren’t annoying enough already, scammers have recently introduced new pressure tactics to their sextortion and scam emails. Last week we reported how cybercriminals are using photographs of targets’ homes in order to scare them into paying money. Now they’re throwing in the name of targets’ partners, telling the receiver that their partner is cheating on them.

Security Boulevard
SEPTEMBER 10, 2024
The post Patch Tuesday Update - September 2024 appeared first on Digital Defense. The post Patch Tuesday Update – September 2024 appeared first on Security Boulevard.

Digital Shadows
SEPTEMBER 10, 2024
This report details the various stages of an Inc Ransomware attack intrusion lifecycle, from exploiting a firewall to the use of Windows log manager and PowerShell for defense evasion.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Security Boulevard
SEPTEMBER 10, 2024
Introduction Following the 2024 ThreatLabz Phishing Report, Zscaler ThreatLabz has been closely tracking domains associated with typosquatting and brand impersonation - common techniques used by threat actors to proliferate phishing campaigns. Typosquatting involves registering domains with misspelled versions of popular websites or brands to capitalize on user errors, while brand impersonation involves creating fake online entities that closely mimic a brand’s official presence.

Zero Day
SEPTEMBER 10, 2024
Apple may be known for its slick design and marketing, but it's the company's engineering prowess that powers the iPhone 16 Pro to new heights.

Security Boulevard
SEPTEMBER 10, 2024
Software developers, as key players in the digital ecosystem, must proactively adapt to these changes to ensure compliance and uphold the privacy rights of users. The post Looking Toward U.S. Federal Privacy Regulation, How Software Companies can Prepare appeared first on Security Boulevard.

Zero Day
SEPTEMBER 10, 2024
The move really limits the options of anyone who wants a new Pro model directly from Apple.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content