Matthew Green on Telegram’s Encryption
Schneier on Security
AUGUST 28, 2024
Matthew Green wrote a really good blog post on what Telegram’s encryption is and is not.

Schneier on Security
AUGUST 28, 2024
Matthew Green wrote a really good blog post on what Telegram’s encryption is and is not.

Penetration Testing
AUGUST 28, 2024
A critical vulnerability (CVE-2024-43425) has been identified in Moodle, a widely-used Learning Management System. This flaw could enable attackers to execute malicious code on affected servers, potentially compromising sensitive student... The post CVE-2024-43425: Moodle Remote Code Execution Vulnerability, PoC Published appeared first on Cybersecurity News.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

We Live Security
AUGUST 28, 2024
ESET research uncovers a vulnerability in WPS Office for Windows (CVE-2024-7262), as it was being exploited by South Korea-aligned cyberespionage group APT-C-60 to target East Asian countries. Analysis of the vendor’s silently released patch led to the discovery of another vulnerability CVE-2024-7263).

The Hacker News
AUGUST 28, 2024
The threat actors behind the BlackByte ransomware group have been observed likely exploiting a recently patched security flaw impacting VMware ESXi hypervisors, while also leveraging various vulnerable drivers to disarm security protections.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Boulevard
AUGUST 28, 2024
Security specialist Fortinet announced the debut of Sovereign SASE and the integration of Generative AI (GenAI) technology into its Unified SASE offering. The post Fortinet Debuts Sovereign SASE, Updates Unified SASE With FortiAI appeared first on Security Boulevard.

The Hacker News
AUGUST 28, 2024
French prosecutors on Wednesday formally charged CEO Pavel Durov with facilitating a litany of criminal activity on the popular messaging platform and placed him under formal investigation following his arrest Saturday.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
AUGUST 28, 2024
Fortra has addressed a critical security flaw impacting FileCatalyst Workflow that could be abused by a remote attacker to gain administrative access. The vulnerability, tracked as CVE-2024-6633, carries a CVSS score of 9.8, and stems from the use of a static password to connect to a HSQL database.

Joseph Steinberg
AUGUST 28, 2024
(The following op-ed, written by cybersecurity expert, Joseph Steinberg, appeared in Conservative Home, Britain’s leading independent conservative news and analysis site.) With the Labour Government committing in the Kings Speech to strengthen the Online Safety Act, new ministers will soon rule on Ofcom’s final guidance on age assurance for Internet access to adult content.
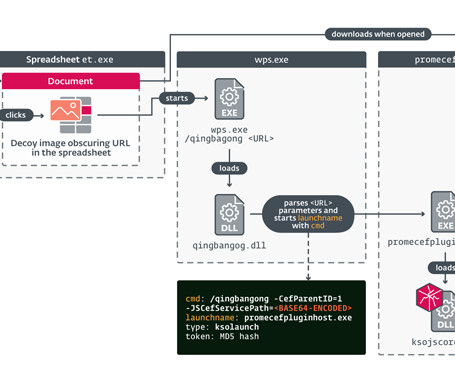
The Hacker News
AUGUST 28, 2024
A South Korea-aligned cyber espionage has been linked to the zero-day exploitation of a now-patched critical remote code execution flaw in Kingsoft WPS Office to deploy a bespoke backdoor dubbed SpyGlace. The activity has been attributed to a threat actor dubbed APT-C-60, according to cybersecurity firms ESET and DBAPPSecurity.

Security Affairs
AUGUST 28, 2024
Iran-linked group APT33 used new Tickler malware in attacks against organizations in the government, defense, satellite, oil and gas sectors. Microsoft researchers reported that the Iran-linked cyberespionage group APT33 (aka Peach Sandstorm , Holmium , Elfin , Refined Kitten , and Magic Hound ) used new custom multi-stage backdoor called Tickler to compromise organizations in sectors such as government, defense, satellite, oil, and gas in the U.S. and UAE.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Boulevard
AUGUST 28, 2024
Xi whiz: Versa Networks criticized for swerving the blame. The post China Cyberwar Coming? Versa’s Vice: Volt Typhoon’s Target appeared first on Security Boulevard.

Security Affairs
AUGUST 28, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Google Chromium V8 bug to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Google Chromium V8 Inappropriate Implementation Vulnerability CVE-2024-38856 (CVSS score of 8.8) to its Known Exploited Vulnerabilities (KEV) catalog.
Security Boulevard
AUGUST 28, 2024
Broadcom today at the VMware Explore 2024 conference extended its VMware vDefend portfolio to include generative artificial intelligence (AI) capabilities in addition to extending its software-defined edge computing portfolio to provide deeper integrations with networking and security platforms that its VMware business unit provides. The post Broadcom Extends VMware Cybersecurity Portfolio appeared first on Security Boulevard.

Security Affairs
AUGUST 28, 2024
BlackByte ransomware operators are exploiting a recently patched VMware ESXi hypervisors vulnerability in recent attacks. Cisco Talos observed the BlackByte ransomware group exploiting the recently patched security flaw CVE-2024-37085 in VMware ESXi hypervisors in recent attacks. The flaw CVE-2024-37085 (CVSS score of 6.8) is an authentication bypass vulnerability in VMware ESXi.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Trend Micro
AUGUST 28, 2024
Threat actors are targeting users in the Middle East by distributing sophisticated malware disguised as the Palo Alto GlobalProtect tool.

Security Affairs
AUGUST 28, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Apache OFBiz bug to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Apache OFBiz Incorrect Authorization Vulnerability CVE-2024-38856 (CVSS score of 9.8) to its Known Exploited Vulnerabilities (KEV) catalog. The vulnerability is an incorrect authorization issue in Apache OFBiz that impacts versions through 18.12.14, version 18.12.15 addressed the flaw.

Security Boulevard
AUGUST 28, 2024
The recent National Public Data (NPD) breach stands as one of the largest social security number (SSN) exposures in history. With reports suggesting potential compromises affecting up to 3 billion SSNs, it is crucial to understand the scope of the breach and take immediate steps to protect yourself from identity theft. This guide provides an … The post National Public Data (NPD) Breach: Essential Guide to Protecting Your Identity appeared first on Security Boulevard.
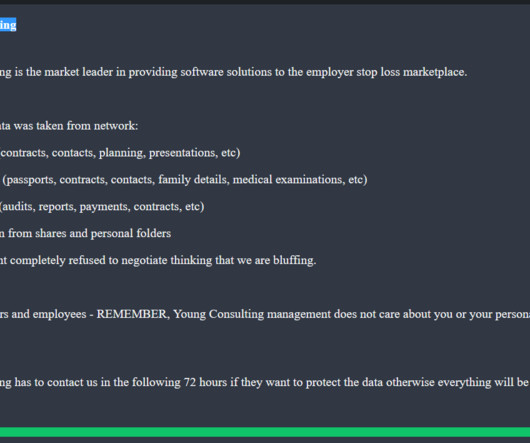
Security Affairs
AUGUST 28, 2024
A ransomware attack by the BlackSuit group on Young Consulting compromised the personal information of over 950,000 individuals. Software solutions provider Young Consulting disclosed a data breach impacting 950,000 individuals following a BlackSuit ransomware attack. On April 13 the company “became aware of technical difficulties” that impacted its infrastructure.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

SecureWorld News
AUGUST 28, 2024
In a concerning development for cybersecurity professionals worldwide, the Chinese state-backed hacking group known as Volt Typhoon has been linked to a series of sophisticated attacks exploiting a Zero-Day vulnerability in Versa Director, a critical management platform used by Internet Service Providers (ISPs) and Managed Service Providers (MSPs). The vulnerability, CVE-2024-39717 , affects Versa Director versions 21.2.3, 22.1.2, and 22.1.3.

Malwarebytes
AUGUST 28, 2024
The Qilin ransomware group listed CODAC Behavioral Healthcare, a nonprofit health care treatment organization, as one of their latest victims. Qilin seems to have a preference for healthcare and support organizations. One of their most well-known victims was the pathology lab services provider Synnovis in June 2024, causing chaos across the NHS in London.

Cisco Security
AUGUST 28, 2024
Cisco Umbrella for Government up-levels government cybersecurity with protection against phishing, malware, ransomware and data loss from cyberattacks. Cisco Umbrella for Government up-levels government cybersecurity with protection against phishing, malware, ransomware and data loss from cyberattacks.

Penetration Testing
AUGUST 28, 2024
In a recent security advisory, Dell disclosed a high-severity vulnerability, identified as CVE-2024-39584, affecting the BIOS of several popular Dell client platforms. This vulnerability, carrying a CVSS score of 8.2,... The post CVE-2024-39584: Dell BIOS Flaw Exposes Systems to Secure Boot Bypass and Arbitrary Code Execution appeared first on Cybersecurity News.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Graham Cluley
AUGUST 28, 2024
A phishing exercise conducted by the IT department of the University of California Santa Cruz (UCSC) has backfired, after causing unnecessary panic amongst students and staff. Read more in my article on the Hot for Security blog.

Penetration Testing
AUGUST 28, 2024
In a significant security advisory, the Perl community has been alerted to a critical vulnerability, CVE-2024-45321, affecting the widely-used App::cpanminus (cpanm) tool. Rated with a CVSS score of 9.8, this... The post Critical CVE-2024-45321 Flaw in Popular Perl Module Installer cpanminus, No Patch Available appeared first on Cybersecurity News.

Zero Day
AUGUST 28, 2024
Ahead of Labor Day weekend, we tested the best phones you can buy. These are the top picks for power users, content creators, budget shoppers, and more.

Penetration Testing
AUGUST 28, 2024
A cybersecurity researcher has uncovered a critical vulnerability in the AI-powered assistant Copilot, integrated into Microsoft 365, which enables malicious actors to exfiltrate sensitive data. The exploit, previously submitted to... The post New Attack on Microsoft 365 Copilot Steals Personal Data appeared first on Cybersecurity News.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Zero Day
AUGUST 28, 2024
Costco is cracking down on membership sharing. Don't miss this deal to buy your own with a free gift card, effectively cutting the price to $40. (I bought one and highly recommend it.

Penetration Testing
AUGUST 28, 2024
Hitachi Energy has issued a cybersecurity advisory addressing multiple critical vulnerabilities discovered in their MicroSCADA X SYS600 product, widely used for monitoring and controlling power systems. The vulnerabilities, identified as... The post Critical Vulnerabilities Expose Hitachi Energy MicroSCADA X SYS600 to Cyberattacks appeared first on Cybersecurity News.

Security Boulevard
AUGUST 28, 2024
The Oregon Zoo's recent data breach serves as a stark reminder of the urgent need for robust cybersecurity measures in today's digital landscape. With over 117,000 payment card details potentially compromised, this incident underscores the vulnerabilities that organizations face when it comes to eSkimming (client-side) attacks and PCI DSS compliance.
Penetration Testing
AUGUST 28, 2024
An open-source project on GitHub called Docker-OSX allows users to effortlessly run Apple’s OSX and macOS systems through containers, a method akin to virtual machines but significantly more convenient than... The post Docker-OSX Shut Down: Apple’s Copyright Claim Impacts macOS Containers appeared first on Cybersecurity News.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content