How to Lose a Fortune with Just One Bad Click
Krebs on Security
DECEMBER 18, 2024
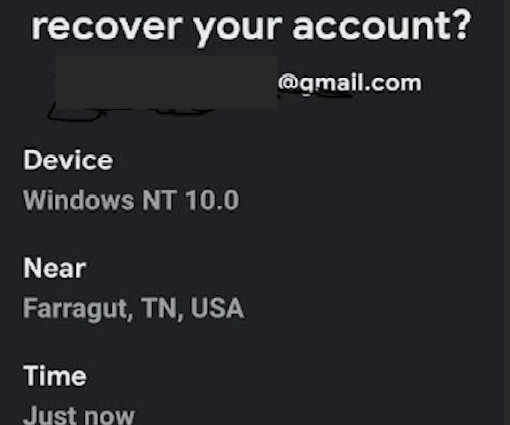
Image: Shutterstock, iHaMoo. Adam Griffin is still in disbelief over how quickly he was robbed of nearly $500,000 in cryptocurrencies. A scammer called using a real Google phone number to warn his Gmail account was being hacked, sent email security alerts directly from google.com, and ultimately seized control over the account by convincing him to click “yes” to a Google prompt on his mobile device.







































Let's personalize your content