Largest Recorded DDoS Attack is 3.8 Tbps
Schneier on Security
OCTOBER 7, 2024
CLoudflare just blocked the current record DDoS attack: 3.8 terabits per second. (Lots of good information on the attack, and DDoS in general, at the link.) News article.

Schneier on Security
OCTOBER 7, 2024
CLoudflare just blocked the current record DDoS attack: 3.8 terabits per second. (Lots of good information on the attack, and DDoS in general, at the link.) News article.

Tech Republic Security
OCTOBER 7, 2024
These 15 cyber attacks or data breaches impacted large swaths of users across the United States and changed what was possible in cybersecurity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
We Live Security
OCTOBER 7, 2024
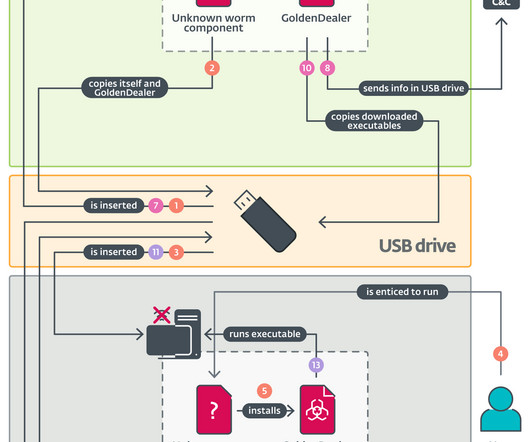
ESET Research analyzed two separate toolsets for breaching air-gapped systems, used by a cyberespionage threat actor known as GoldenJackal.

Tech Republic Security
OCTOBER 7, 2024
Gain a comprehensive understanding of cybersecurity with this 12-hour, 5-course bundle that covers everything from foundational concepts to advanced strategies.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
OCTOBER 7, 2024
Cybersecurity researchers have discovered a new botnet malware family called Gorilla (aka GorillaBot) that is a variant of the leaked Mirai botnet source code. Cybersecurity firm NSFOCUS, which identified the activity last month, said the botnet "issued over 300,000 attack commands, with a shocking attack density" between September 4 and September 27, 2024.

Tech Republic Security
OCTOBER 7, 2024
Read more about the U.S. Department of Justice and Microsoft’s efforts to interrupt the activities of Russian-based threat actor Star Blizzard, and learn how to protect from this threat.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
OCTOBER 7, 2024
Australian cyber professionals are reporting more job stress, partly due to skills gaps and other growing industry challenges.

SecureList
OCTOBER 7, 2024
Introduction In July 2021, a campaign was launched primarily targeting Russian government agencies and industrial enterprises. Shortly after the campaign started, we began tracking it, and published three reports in August and September 2024 through our threat research subscription on the threat actor we named Awaken Likho (also named by other vendors as Core Werewolf).

Tech Republic Security
OCTOBER 7, 2024
DNS and IP address management is getting harder as multi-cloud strategies take over in Australia and the APAC region.

Security Affairs
OCTOBER 7, 2024
Russian state media VGTRK faced a major cyberattack, which a Ukrainian source claimed was conducted by Kyiv’s hackers. A Ukrainian government source told Reuters that Kyiv’s hackers are behind the cyber attack that disrupted operations at the Russian state media company VGTRK on Putin’s birthday. The All-Russia State Television and Radio Broadcasting Company (VGTRK, Russian: ВГТРК) or Russian Television and Radio Broadcasting Company, also known as Russian Television and Radio,

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Hacker News
OCTOBER 7, 2024
Ukraine has claimed responsibility for a cyber attack that targeted Russia state media company VGTRK and disrupted its operations, according to reports from Bloomberg and Reuters. The incident took place on the night of October 7, VGTRK confirmed, describing it as an "unprecedented hacker attack.

Security Affairs
OCTOBER 7, 2024
Universal Music Group notified hundreds of individuals about a data breach compromising their personal information. Universal Music Group is notifying 680 individuals about a data breach that compromised their personal information, including their Social Security number. The data breach occurred on July 15, 2024, and was discovered on August 30, 2024. “In early July, we detected unauthorized activity in one of our internal applications.
The Last Watchdog
OCTOBER 7, 2024
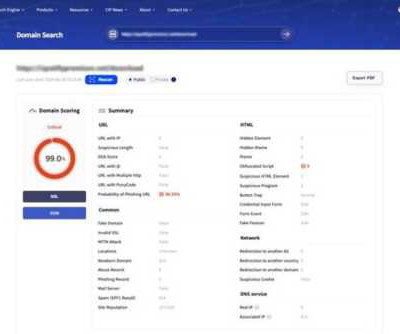
Torrance, Calif., Oct. 7, 2024, CyberNewswire — Criminal IP , a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA , has partnered with Hybrid Analysis , a platform that provides advanced malware analysis and threat intelligence, to enhance threat research. This collaboration integrates Criminal IP’s advanced domain scanning capabilities into the Hybrid Analysis platform, providing security professionals with deeper insights and more effective threat mitigation s

Security Affairs
OCTOBER 7, 2024
238,000 Comcast customers were impacted by the FBCS data breach following the February ransomware attack, Comcast reports. Telecommunications giant Comcast is notifying approximately 238,000 customers impacted by the Financial Business and Consumer Solutions (FBCS) data breach. FBCS, a third-party debt collection agency, collects personal information from its clients to facilitate debt collection activities on behalf of those clients.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
OCTOBER 7, 2024
Akamai Technologies has made available at no extra cost a connector that makes it simpler for cybersecurity teams to discover application programming interfaces (APIs) that organizations have exposed via its content delivery network (CDN). The post Akamai Embeds API Security Connector in CDN Platform appeared first on Security Boulevard.

Malwarebytes
OCTOBER 7, 2024
Apple has issued security updates for iOS 18.0.1 and iPadOS 18.0.1 which includes a fix for a bug that could allow a user’s saved passwords to be read aloud by its VoiceOver feature. VoiceOver allows users to use their iPhone or iPad even if they can’t see the screen. It gives audible descriptions of what’s on your screen—for example, the battery level, who’s calling you, or what item your finger is on.

Security Affairs
OCTOBER 7, 2024
A critical vulnerability in the Apache Avro Java Software Development Kit (SDK) could be exploited to execute arbitrary code on vulnerable instances. A critical vulnerability, tracked as CVE-2024-47561, in the Apache Avro Java Software Development Kit (SDK) could allow the execution of arbitrary code on vulnerable instances. The flaw, tracked as CVE-2024-47561, impacts all versions of the software prior to 1.11.4.

Security Boulevard
OCTOBER 7, 2024
The zero-trust model demands robust identity security, which needs continuous verification of individuals and systems. The post How to Prepare Identity Stack to Adopt the Zero-Trust Model appeared first on Security Boulevard.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

The Hacker News
OCTOBER 7, 2024
Organizations are losing between $94 - $186 billion annually to vulnerable or insecure APIs (Application Programming Interfaces) and automated abuse by bots. That’s according to The Economic Impact of API and Bot Attacks report from Imperva, a Thales company. The report highlights that these security threats account for up to 11.

Security Boulevard
OCTOBER 7, 2024
The DOJ wants to seize $2.67 million from the $69 million in crypto the North Korean-backed Lazarus Group stole in from the options exchange Deribit in 2022 and online gambling platform Stake.com last year. The post DOJ Wants to Claw Back $2.67 Million Stolen by Lazarus Group appeared first on Security Boulevard.

Graham Cluley
OCTOBER 7, 2024
When Sean Kelly bought a top-of-the-line vacuum cleaner, he imagined he was making a safe purchase. Little did he know that the cleaning machine scuttling about his family's feet contained a security flaw that could let anyone see and hear their every move. Read more in my article on the Hot for Security blog.

Security Boulevard
OCTOBER 7, 2024
There is a growing disconnect between the increasing sophistication of cybersecurity threats and the preparedness of IT teams to combat them, according to an O’Reilly study of more than 1300 IT professionals. The post Critical Skills Gap in AI, Cloud Security appeared first on Security Boulevard.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

The Hacker News
OCTOBER 7, 2024
A critical security flaw has been disclosed in the Apache Avro Java Software Development Kit (SDK) that, if successfully exploited, could allow the execution of arbitrary code on susceptible instances. The flaw, tracked as CVE-2024-47561, impacts all versions of the software prior to 1.11.4. "Schema parsing in the Java SDK of Apache Avro 1.11.

Security Boulevard
OCTOBER 7, 2024
Understanding reachability is increasingly important for enterprises, as it can significantly influence their risk management strategies. The post Reachability and Risk: Prioritizing Protection in a Complex Security Landscape appeared first on Security Boulevard.

The Hacker News
OCTOBER 7, 2024
Google has announced that it's piloting a new security initiative that automatically blocks sideloading of potentially unsafe Android apps in India, after similar tests in Singapore, Thailand, and Brazil.

Penetration Testing
OCTOBER 7, 2024
A new study has revealed the extent to which smart TVs use Automatic Content Recognition (ACR) technology to track users’ viewing habits. The research, conducted by a team of scientists... The post Your Smart TV is Watching You: New Research Reveals the Extent of ACR Tracking appeared first on Cybersecurity News.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

The Hacker News
OCTOBER 7, 2024
Ever heard of a "pig butchering" scam? Or a DDoS attack so big it could melt your brain? This week's cybersecurity recap has it all – government showdowns, sneaky malware, and even a dash of app store shenanigans. Get the scoop before it's too late!
Malwarebytes
OCTOBER 7, 2024
After what seemed like a long hiatus, we’ve observed threat actors returning to malvertising to drop malware disguised as software downloads. The campaign we identified is high-impact, going after utility software such as Slack, Notion, Calendly, Odoo, Basecamp, and others. For this blog, we decided to focus on the Mac version of communication tool Slack.

Approachable Cyber Threats
OCTOBER 7, 2024
Category Awareness, Compliance, Cybersecurity Fundamentals, FedRAMP, CMMC Risk Level NIST recently updated its decades-old password security guidance after years of scrutiny, skepticism, and flat-out ineffectiveness finally forced the agency to address practical security considerations and realistic threats while abandoning what many considered to be ineffective security theater.

Malwarebytes
OCTOBER 7, 2024
A data breach at Financial Business and Consumer Solutions (FBCS), a US debt collection agency, has led to the loss of data of some Comcast Cable Communications and Truist Bank customers. FBCS is in the business of collecting unpaid debts on behalf of its customers. The data breach occurred in February 2024 and the cybercriminals responsible for the incident gained access to: Full names Social Security Numbers (SSNs) Date of birth Account information and other provider information ID card and/or

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content