Surveillance Watch
Schneier on Security
AUGUST 22, 2024
This is a fantastic project mapping the global surveillance industry.

Schneier on Security
AUGUST 22, 2024
This is a fantastic project mapping the global surveillance industry.

Tech Republic Security
AUGUST 22, 2024
Australia is building a digital ID and information verification system called Trust Exchange, or TEx, that will see the Government verifying customer details for businesses via a smartphone app.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
AUGUST 22, 2024
Cary, NC, Aug. 22, 2024, CyberNewsWire — INE Security , a global cybersecurity training and certification provider, recently launched initiatives with several higher education institutions in an ongoing campaign to invest in the education of aspiring cybersecurity professionals. Warn “There is a critical skills gap in the industry, which has enormous implications for businesses and individuals alike,” said Dara Warn, INE Security’s CEO.

Tech Republic Security
AUGUST 22, 2024
Australia is rapidly embracing renewable energy. But for the nation to successfully leverage renewable energy, it is imperative to establish strong IT foundations.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Penetration Testing
AUGUST 22, 2024
Security researcher ‘Frost’ has released proof-of-concept exploit code for the CVE-2024-38054 vulnerability, escalating concerns over a recently patched Windows security flaw. This high-severity vulnerability in the Kernel Streaming WOW Thunk... The post Exploit for CVE-2024-38054 Released: Elevation of Privilege Flaw in Windows Kernel Streaming WOW Thunk appeared first on Cybersecurity News.

Security Boulevard
AUGUST 22, 2024
There are significant gaps in cyber resilience, despite growing confidence in organizational strategies, according to a Cohesity survey of 3,100 IT and security decision-makers across eight countries. The post Cyber Resilience Lacking, Organizations Overconfident appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Penetration Testing
AUGUST 22, 2024
SonicWall, a prominent network security provider, has released a security advisory warning users of a critical vulnerability (CVE-2024-40766) affecting their SonicOS operating system. The vulnerability, which carries a CVSS score... The post SonicWall Issues Urgent Patch for Critical Firewall Vulnerability (CVE-2024-40766) appeared first on Cybersecurity News.

Security Affairs
AUGUST 22, 2024
Semiconductor manufacturer Microchip Technology announced that its operations were disrupted by a cyberattack. U.S. chipmaker Microchip Technology suffered a cyberattack that disrupted operations at several of its manufacturing plants. The company detected potentially suspicious activity involving its IT infrastructure on August 17, 2024. The attack severely impacted the production capacity of the company that shut down or isolate some systems to contain the incident.

Pen Test Partners
AUGUST 22, 2024
TL;DR Rooting is useful for Android assessments The process is relatively simple It will wipe all user data from the device and void any warranty Introduction For mobile testing, be it for apps or hardware, having complete control over the device is essential for analysis and vulnerability assessment. Rooting an Android device allows us to gain root privileges, giving us full access to the OS, including access to the private storage of any installed app.

The Hacker News
AUGUST 22, 2024
Cybersecurity researchers have uncovered a new information stealer that's designed to target Apple macOS hosts and harvest a wide range of information, underscoring how threat actors are increasingly setting their sights on the operating system. Dubbed Cthulhu Stealer, the malware has been available under a malware-as-a-service (MaaS) model for $500 a month from late 2023.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Security Boulevard
AUGUST 22, 2024
A report published today by Critical Start, a provider of managed cybersecurity services, finds cyberattacks in the first half of 2024 continued to focus on vertical industries that are rich in critical data that can either be encrypted or stolen. For example, the manufacturing and industrial products sector remains the top targeted industry sector, with.

The Hacker News
AUGUST 22, 2024
Details have emerged about a China-nexus threat group's exploitation of a recently disclosed, now-patched security flaw in Cisco switches as a zero-day to seize control of the appliance and evade detection. The activity, attributed to Velvet Ant, was observed early this year and involved the weaponization of CVE-2024-20399 (CVSS score: 6.

Malwarebytes
AUGUST 22, 2024
Whenever you shop online and enter your payment details, you could be at risk of being a victim of fraud. Digital skimmers are snippets of code that have been injected into online stores and they can steal your credit card number, expiration date and CVV/CVC as you type it in. We recently detected a new malware campaign targeting a number of online stores running Magento, a popular e-commerce platform.
The Hacker News
AUGUST 22, 2024
Cybersecurity researchers have uncovered a hardware backdoor within a particular model of MIFARE Classic contactless cards that could allow authentication with an unknown key and open hotel rooms and office doors. The attacks have been demonstrated against FM11RF08S, a new variant of MIFARE Classic that was released by Shanghai Fudan Microelectronics in 2020.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Security Affairs
AUGUST 22, 2024
US oil giant Halliburton announced that it was hit by a cyberattack that is affecting operations at its Houston, Texas offices. Halliburton, a major U.S. oil company, announced that a cyberattack hit its IT infrastructure, particularly impacting operations at its Houston offices. Halliburton Company is an American multinational corporation and the world’s second largest oil service company which is responsible for most of the world’s largest fracking operations.

Tech Republic Security
AUGUST 22, 2024
Explore how low media literacy can have lingering repercussions for the tech industry in Australia.

Penetration Testing
AUGUST 22, 2024
In a surprising turn of events, McDonald’s, the global fast-food giant, fell victim to a cyberattack that leveraged the brand’s Instagram account to promote a meme coin called “Grimace.” On... The post McDonald’s Falls Victim to Cyberattack: Instagram Hijacked to Promote Grimace Cryptocurrency appeared first on Cybersecurity News.

Security Affairs
AUGUST 22, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Dahua IP Camera, Linux Kernel and Microsoft Exchange Server bugs to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the following vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog : CVE-2021-33044 Dahua IP Camera Authentication Bypass Vulnerability CVE-2021-33045 Dahua IP Camera Authentication Bypass Vulnerability CVE-2022-0185 Linux Kernel

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!

Graham Cluley
AUGUST 22, 2024
A production partner of Netflix has suffered a serious security breach which has resulted in yet-to-be-released episodes of popular shows to be leaked online. Read more in my article on the Hot for Security blog.

Security Affairs
AUGUST 22, 2024
SolarWinds fixed a hardcoded credential flaw in its Web Help Desk (WHD) software that could allow attackers to gain unauthorized access to vulnerable instances. SolarWinds has addressed a new security flaw, tracked as CVE-2024-28987 (CVSS score of 9.1) in its Web Help Desk (WHD) software that could allow remote unauthenticated attackers to gain unauthorized access to vulnerable instances.

The Hacker News
AUGUST 22, 2024
A 33-year-old Latvian national living in Moscow, Russia, has been charged in the U.S. for allegedly stealing data, extorting victims, and laundering ransom payments since August 2021. Deniss Zolotarjovs (aka Sforza_cesarini) has been charged with conspiring to commit money laundering, wire fraud and Hobbs Act extortion.

Security Affairs
AUGUST 22, 2024
GitHub addressed three vulnerabilities in its GitHub Enterprise Server product, including a critical authentication flaw. GitHub addressed three security vulnerabilities impacting the GitHub Enterprise Server (GHES), including a critical flaw tracked as CVE-2024-6800 (CVSS score of 9.5). An attacker can trigger the vulnerability to gain site administrator privileges.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

The Hacker News
AUGUST 22, 2024
SolarWinds has issued patches to address a new security flaw in its Web Help Desk (WHD) software that could allow remote unauthenticated users to gain unauthorized access to susceptible instances.
Security Boulevard
AUGUST 22, 2024
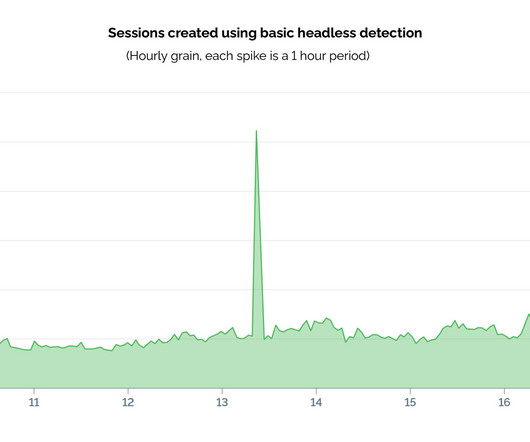
In the escalating battle against malicious headless bots, basic detection methods are no longer sufficient. As cybercriminals refine their techniques and leverage headless browsers to automate attacks with increasing sophistication, the need for advanced detection strategies has never been more critical. This blog post dives into the world of headless browsers, exploring how they are […] The post The Growing Challenge of Headless Browser Attacks: How to Defend Your Digital Assets appeared first
The Hacker News
AUGUST 22, 2024
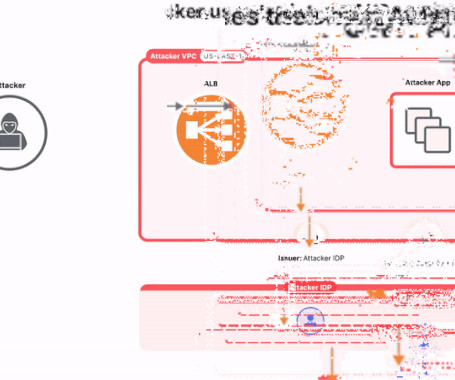
As many as 15,000 applications using Amazon Web Services' (AWS) Application Load Balancer (ALB) for authentication are potentially susceptible to a configuration-based issue that could expose them to sidestep access controls and compromise applications. That's according to findings from Israeli cybersecurity company Miggo, which dubbed the problem ALBeast.

IT Security Guru
AUGUST 22, 2024
We’ve all encountered websites that are legitimate, but feel clunky, slow, and frustrating to navigate. A website’s first impression directly impacts how users perceive a business’s quality and trustworthiness, making it crucial to get it right. However, creating an effective online presence can be a daunting task. Even seasoned professionals stumble upon common pitfalls that can impact user experience and, consequently, a site’s success.

Advertisement
IT leaders are experiencing rapid evolution in AI amid sustained investment uncertainty. As AI evolves, enhanced cybersecurity and hiring challenges grow. This whitepaper offers real strategies to manage risks and position your organization for success.
Penetration Testing
AUGUST 22, 2024
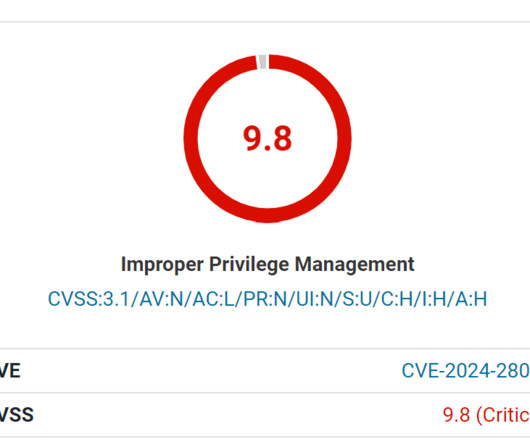
A critical security vulnerability in the widely used LiteSpeed Cache plugin for WordPress has come under active exploitation, with over 30,000 attack attempts blocked in just the past 24 hours,... The post CVE-2024-28000 in LiteSpeed Cache Plugin Actively Exploited: Over 30,000 Attacks Blocked in 24 Hours appeared first on Cybersecurity News.

The Hacker News
AUGUST 22, 2024
What is Continuous Attack Surface Penetration Testing or CASPT? Continuous Penetration Testing or Continuous Attack Surface Penetration Testing (CASPT) is an advanced security practice that involves the continuous, automated, and ongoing penetration testing services of an organization's digital assets to identify and mitigate security vulnerabilities.

Security Boulevard
AUGUST 22, 2024
A data breach at National Public Data, a relatively obscure but widely connected company, has exposed 272 million Social Security numbers. This breach, reminiscent of the 2017 Equifax breach but on an even larger scale, has sent shockwaves through the security sector. Hackers infiltrated National Public Data’s systems, accessing a vast database containing highly sensitive […] The post Massive Data Breach Exposes Personal Information of Billions appeared first on Centraleyes.

Penetration Testing
AUGUST 22, 2024
Researchers at ANY.RUN have identified a new campaign using Tycoon 2FA phish-kit. This time, attackers are targeting US government organizations with fake Microsoft pages. Tycoon 2FA and Its Latest Activity... The post New Phishing Campaign Targets US Government Organizations appeared first on Cybersecurity News.

Advertisement
Leverage the Cloud Development Environment Maturity Model to elevate your software development practices with scalable, secure cloud-based workspaces. This model offers a structured approach to modernizing development, aligning technology, developer experience, security, and workflows. By implementing Cloud Development Environments (CDEs), teams can boost efficiency, improve security, and streamline operations through centralized governance.
Let's personalize your content