New Patent Application for Car-to-Car Surveillance
Schneier on Security
AUGUST 5, 2024
Ford has a new patent application for a system where cars monitor each other’s speeds, and then report then to some central authority. Slashdot thread.

Schneier on Security
AUGUST 5, 2024
Ford has a new patent application for a system where cars monitor each other’s speeds, and then report then to some central authority. Slashdot thread.

Krebs on Security
AUGUST 5, 2024
A ransomware group called Dark Angels made headlines this past week when it was revealed the crime group recently received a record $75 million data ransom payment from a Fortune 50 company. Security experts say the Dark Angels have been around since 2021, but the group doesn’t get much press because they work alone and maintain a low profile, picking one target at a time and favoring mass data theft over disrupting the victim’s operations.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
AUGUST 5, 2024
Australia’s public sector agencies are under increasing pressure to improve their readiness for cyber attacks and data breaches, as surveys and investigations find their preparedness lackluster.
The Last Watchdog
AUGUST 5, 2024
LAS VEGAS — Humans, unsurprisingly, remain the weak link in cybersecurity. Related: Digital identity best practices We’re gullible – and we can’t get away from relying on usernames and passwords. Steady advances in software and hardware mechanisms to secure identities and privileged access have helped; yet crippling network breaches that start by fooling or spoofing a single human user continue to proliferate.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Tech Republic Security
AUGUST 5, 2024
If you’re on the hunt for Urban VPN alternatives, check out our in-depth analysis of Proton VPN, TunnelBear and other VPN providers.
The Hacker News
AUGUST 5, 2024
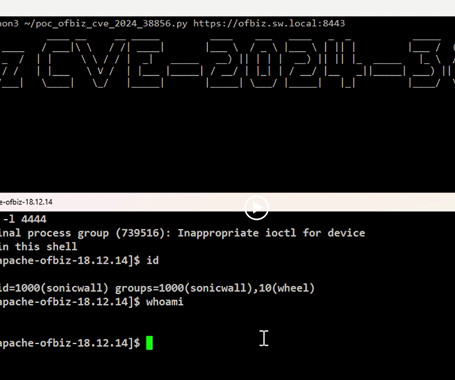
A new zero-day pre-authentication remote code execution vulnerability has been disclosed in the Apache OFBiz open-source enterprise resource planning (ERP) system that could allow threat actors to achieve remote code execution on affected instances. Tracked as CVE-2024-38856, the flaw has a CVSS score of 9.8 out of a maximum of 10.0. It affects Apache OFBiz versions prior to 18.12.15.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
AUGUST 5, 2024
Google has addressed a high-severity security flaw impacting the Android kernel that it has been actively exploited in the wild. The vulnerability, tracked as CVE-2024-36971, has been described as a case of remote code execution impacting the kernel.

Security Affairs
AUGUST 5, 2024
A security bypass bug in Rockwell Automation ControlLogix 1756 devices could allow unauthorized access to vulnerable devices. A high-severity security bypass vulnerability, tracked as CVE-2024-6242 (CVSS Base Score v4.0 of 7.3), impacts Rockwell Automation ControlLogix 1756 devices. An attacker can exploit the vulnerability to execute common industrial protocol (CIP) programming and configuration commands. “A vulnerability exists in the affected products that allows a threat actor to bypas

Security Boulevard
AUGUST 5, 2024
National Public Data, a background check company that collects sensitive personal information, is facing a class-action legal complaint for allowing the data from 2.9 billion people to be stolen in a breach and later sold on the dark web for millions of dollars. The post National Public Data Sued for Hack that Exposed Data of 2.9 Billion People appeared first on Security Boulevard.

Bleeping Computer
AUGUST 5, 2024
Android security updates this month patch 46 vulnerabilities, including a high-severity remote code execution (RCE) exploited in targeted attacks. [.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
Security Boulevard
AUGUST 5, 2024
For You Plague: U.S. Justice Dept. and Federal Trade Commission file lawsuit, alleging TikTok broke the COPPA law, plus a previous injunction. The post TikTok Abuses Kids, say DoJ and FTC appeared first on Security Boulevard.

Bleeping Computer
AUGUST 5, 2024
A design flaw in Windows Smart App Control and SmartScreen that enables attackers to launch programs without triggering security warnings has been under exploitation since at least 2018. [.

The Hacker News
AUGUST 5, 2024
The Loper Bright decision has yielded impactful results: the Supreme Court has overturned forty years of administrative law, leading to potential litigation over the interpretation of ambiguous laws previously decided by federal agencies. This article explores key questions for cybersecurity professionals and leaders as we enter a more contentious period of cybersecurity law.

Security Boulevard
AUGUST 5, 2024
LLMs are different from other tools and different approaches are required to mitigate their risks involving new security technologies. The post Strategies for Mitigating LLM Risks in Cybersecurity appeared first on Security Boulevard.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Hacker News
AUGUST 5, 2024
Organizations in Kazakhstan are the target of a threat activity cluster dubbed Bloody Wolf that delivers a commodity malware called STRRAT (aka Strigoi Master). "The program selling for as little as $80 on underground resources allows the adversaries to take control of corporate computers and hijack restricted data," cybersecurity vendor BI.ZONE said in a new analysis.

Security Boulevard
AUGUST 5, 2024
As AI adoption grows, so does organizations’ appetite for the vast data from disparate sources needed to train AI models. Because of this, companies are grappling with how to safeguard a surging amount of fragmented data wherever it lives. The post DSPM: A Cybersecurity Approach Tailor-Made for This AI Era appeared first on Security Boulevard.

Bleeping Computer
AUGUST 5, 2024
The Hunters International ransomware group is targeting IT workers with a new C# remote access trojan (RAT) called SharpRhino to breach corporate networks. [.
Security Boulevard
AUGUST 5, 2024
n the battle against cyber threats, should we trust human experts or AI agents to protect our valuable data? Explore how AI's tireless vigilance, pattern recognition, and rapid adaptation are reshaping cybersecurity. The post Human vs AI Agents in Cybersecurity: Who Should Guard Your Data? appeared first on Security Boulevard.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
AUGUST 5, 2024
South Korea's National Cyber Security Center (NCSC) warns that state-backed DPRK hackers hijacked flaws in a VPN's software update to deploy malware and breach networks. [.

Security Boulevard
AUGUST 5, 2024
The Payment Card Industry Data Security Standard (PCI DSS) aims to improve credit, debit and cash card transaction security and protect cardholders from breaches of their personal information. The post Effective Third-Party Risk Management Under PCI DSS 4.0 appeared first on Security Boulevard.

Penetration Testing
AUGUST 5, 2024
The U.S. Department of Justice, in conjunction with the Federal Trade Commission (FTC), has initiated a civil lawsuit against the popular app TikTok and its Chinese parent company ByteDance. Authorities accuse the developers of... The post TikTok Faces Civil Lawsuit for COPPA Violations, Millions of Children Affected appeared first on Cybersecurity News.

The Hacker News
AUGUST 5, 2024
Incident response is a structured approach to managing and addressing security breaches or cyber-attacks. Security teams must overcome challenges such as timely detection, comprehensive data collection, and coordinated actions to enhance readiness. Improving these areas ensures a swift and effective response, minimizing damage and restoring normal operations quickly.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Tech Republic Security
AUGUST 5, 2024
Company devices which are hooked to the internet can involve both internal and external connections. These internet resources can be web servers, email servers, proxy servers, routers, FTP servers or any other public-facing device which performs a service or function.
Security Boulevard
AUGUST 5, 2024
A novel Linux kernel exploit technique called SLUBStick has proven to be 99% successful running the kind of attacks that in the past had a success rate of about 40% and allows bad actors to take total control of a system. The post Novel SLUBStick Linux Exploit Gives Attackers Full System Control appeared first on Security Boulevard.

SecureWorld News
AUGUST 5, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has taken a pioneering step in the realm of artificial intelligence and cybersecurity by appointing its first Chief Artificial Intelligence Officer, Lisa Einstein. This move, announced on August 1, 2024, underscores the growing importance of AI in national security and sets a precedent that other organizations may soon follow.
Malwarebytes
AUGUST 5, 2024
Last week on Malwarebytes Labs: Threat actor impersonates Google via fake ad for Authenticator Scammers are impersonating cryptocurrency exchanges, FBI warns Meta to pay $1.4 billion over unauthorized facial recognition image capture Apple fixes Siri vulnerabilities that could have allowed sensitive data theft from locked device. Update now! SIEM is not storage, with Jess Dodson (Lock and Code S05E16) US senators ask FTC to investigate car makers’ privacy practices Last week on ThreatDown: Azure

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

SecureBlitz
AUGUST 5, 2024
In this post, learn why identity theft protection is crucial in today's digital world. Protecting personal information has never been more critical in our increasingly digital world. Identity theft is a growing concern that can have devastating consequences for its victims. This blog post will explore why identity theft protection is crucial, the risks of […] The post Why Is Identity Theft Protection Crucial in Today’s Digital World?

Bleeping Computer
AUGUST 5, 2024
A previously undocumented Android malware named 'LightSpy' has been discovered targeting Russian users, posing on phones as an Alipay app or a system service to evade detection. [.

Security Boulevard
AUGUST 5, 2024
Salt Security is making available a free scanning tool that it has been using to assess the level of potential risk organizations face from cross-site scripting (XSS) attacks in the wake of discovering similar flaws in multiple websites, including the Hotjar service that millions of users rely on to analyze web traffic. The post Salt Security Provides Free Scans for XXS Vulnerabilities Involving OAuth Protocol appeared first on Security Boulevard.
Cisco Security
AUGUST 5, 2024
Cisco XDR turns one year old. Here is the backstory of how we developed relationships and alliances with “competitors” to have the open ecosystem of today. Cisco XDR turns one year old. Here is the backstory of how we developed relationships and alliances with “competitors” to have the open ecosystem of today.

Advertisement
Tech leaders today are facing shrinking budgets and investment concerns. This whitepaper provides insights from over 1,000 tech leaders on how to stay secure and attract top cybersecurity talent, all while doing more with less. Download today to learn more!
Let's personalize your content