Weekly Update 405
Troy Hunt
JUNE 23, 2024
Ah, sunshine! As much as I love being back in Norway, the word "summer" is used very loosely there. Not as much in Greece, however, which is just spectacular: Finally escaped the bitterly cold Norwegian summer for something… warmer 🇬🇷 pic.twitter.com/jk9knZvJar — Troy Hunt (@troyhunt) June 17, 2024 3 nights in Mykonos, 2 in Santorini and I'm pushing this post out just before our second night in Athens before embarking on the long journey home.







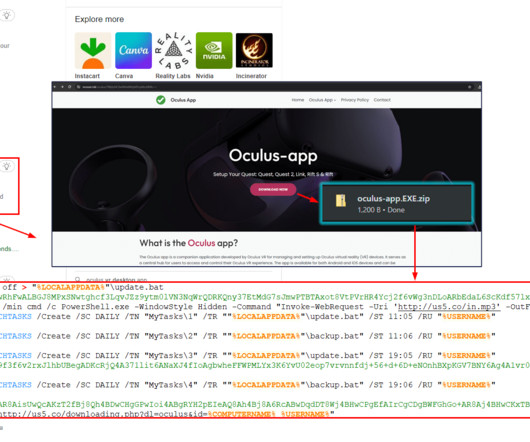























Let's personalize your content