ViperSoftX Malware Disguises as eBooks on Torrents to Spread Stealthy Attacks
The Hacker News
JULY 9, 2024
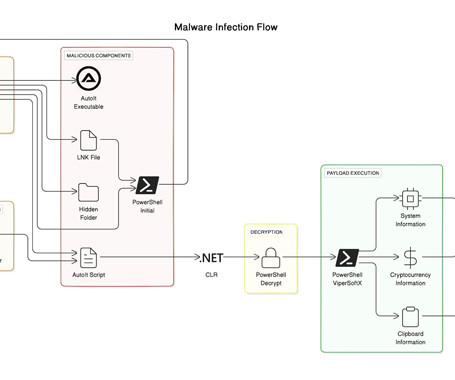
The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. "A
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
The Hacker News
JULY 9, 2024
The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. "A

Penetration Testing
JULY 11, 2024
Disguised as harmless ebooks, these malicious files are spreading through... The post Cybercriminals Exploit Ebooks to Spread AsyncRAT Malware appeared first on Cybersecurity News.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Threatpost
APRIL 19, 2021
Our new eBook goes beyond the status quo to take a look at the evolution of ransomware and what to prepare for next.

The Hacker News
JANUARY 22, 2021
Dubbed "KindleDrip," the exploit chain takes advantage of a feature called "Send to Kindle" to send a malware-laced document to a Kindle device that, when opened, could be leveraged to remotely execute arbitrary
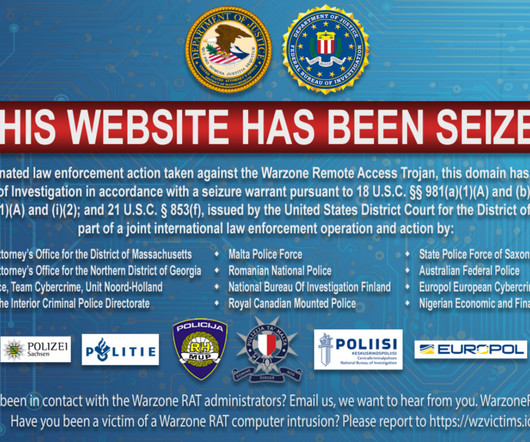
Security Affairs
FEBRUARY 12, 2024
The seizure is the result of an international law enforcement operation, federal authorities in Atlanta and Boston charged individuals in Malta and Nigeria, for their involvement in selling the malware. The two individuals are charged with selling and supporting the Warzone RAT and other malware. ” concludes DoJ.

Vipre
MAY 5, 2021
Yes, endpoint security is a vital element in your malware defense, but it cannot do the job alone. As malware threats increase in sophistication, so should the tools to combat them. For more information about how to build a comprehensive, layered security strategy check out our ebook, “ SMBs Under Attack eBook ”.

Duo's Security Blog
DECEMBER 12, 2022
The Retail & Hospitality Information Sharing and Analysis Center (RH-ISAC) just released the 2022 Holiday Season Cyber Threat Trends report that reveals the most prevalent malware tools leveraged by cyber criminals this year, with phishing and fraud dominating the list.

Tech Republic Security
DECEMBER 19, 2022
So, is it any wonder that malware is propagating in multi-cloud environments under the radar? Based on research conducted by VMware’s Threat Analysis Unit, this eBook uncovers the unique characteristics of remote access tools.

Security Affairs
OCTOBER 15, 2020
The bookseller also operated the Nook Digital, which is a spin-off division that sells eBook and e-Reader platform. Over the weekend, users have been complaining on Nook’s Facebook page and Twitter that they were not able to access their library of purchased eBooks and magazine subscriptions. SecurityAffairs – hacking, malware).

Security Affairs
MAY 6, 2023
Twitter confirmed that a security incident publicly exposed Circle tweets FBI seized other domains used by the shadow eBook library Z-Library WordPress Advanced Custom Fields plugin XSS exposes +2M sites to attacks Fortinet fixed two severe issues in FortiADC and FortiOS Pro-Russia group NoName took down multiple France sites, including the French (..)

Duo's Security Blog
FEBRUARY 27, 2023
In this eBook “ Healthcare Shifts in Cybersecurity” we will look into the security challenges and trends facing healthcare and make practical recommendations for keeping your healthcare workforce secure and productive. Duo offers a trusted access solution that can help prevent healthcare industry ransomware attacks.

Graham Cluley
MAY 3, 2022
One of the largest library services in Germany, EKZ Bibliotheksservice, has been impacted by a ransomware attack that has left book lovers unable to rent and borrow eBooks, audio books, and electronic magazines. Read more in my article on the Hot for Security blog.

Duo's Security Blog
FEBRUARY 13, 2023
It just takes on lackadaisical click by an employee to install malware that results in ransomware. And for more information on protecting against ransomware, be sure to check out our ebook: Protecting Against Ransomware: Zero Trust Security for a Modern Workforce. Ransomware has gone up 150% since the pandemic , and the U.S.

Malwarebytes
JUNE 22, 2023
MRG Effitas, a world leader in independent IT research, published their anti-malware efficacy assessment results for Q1 2023. The signature and behavior-based detection techniques and proprietary anti-exploit technology of Malwarebytes EP allowed it to detect and block more malware than any other competitor on the Q1 test.

Malwarebytes
APRIL 10, 2023
Google patches three important vulnerabilities 9 vital criteria for effective endpoint security: Insights from the 'Endpoint Security Evaluation Guide' eBook Stop! fine Update Android now! fine Update Android now! Are you putting sensitive company data into ChatGPT? Do cyber regulations actually make K–12 schools safer?

Malwarebytes
JULY 14, 2022
Securing that many endpoints can get really complex, really fast, especially when you consider that the common wisdom that Macs don’t get malware simply isn’t true: in fact, the number of malware detections on Mac jumped 200% year-on-year in 2021. And it’s not just malware you have to worry about with your Mac endpoints.

Security Affairs
JULY 2, 2020
OVER 165 PAGESALWAYS FREE – LOADED WITH EXCELLENT CONTENT Learn from the experts, cybersecurity best practices Find out about upcoming information security related conferences, expos and trade shows. Always free, no strings attached.

Security Affairs
AUGUST 5, 2020
OVER 145 PAGESALWAYS FREE – LOADED WITH EXCELLENT CONTENT Learn from the experts, cybersecurity best practices Find out about upcoming information security related conferences, expos and trade shows. Always free, no strings attached.

Security Affairs
OCTOBER 22, 2020
The publication is divided into 22 different reports, which are available in both pdf form and ebook form. This year the report has a different format that could allow the readers to focus on the threat of interest. Infographic – Threat Landscape Mapping during COVID-19 ). states the report.

Malwarebytes
SEPTEMBER 14, 2023
MRG Effitas, a world leader in independent IT research, published their anti-malware efficacy assessment results for Q2 2023. Nebula view of detected ransomware activity 100% of banking malware blocked In 2021, 37% of banking malware attacks targeted corporate users. Download below!

Security Boulevard
MAY 9, 2022
Malware Traits of Blackcat Ransomware. Many of its developers have been associated with the Darkside/Blackmatter group , which also brings about the concern of dealing with experienced malware operators. This malware, after successfully gaining access to the target machine, beacons back data on the victim machine (host UUID).

Webroot
JANUARY 7, 2022
Malware made leaps and bounds in 2021. In 2022, the widespread growth of mobile access will increase the prevalence of mobile malware, given all of the behavior tracking capabilities,” says Grayson Milbourne, security intelligence director, Carbonite + Webroot, OpenText companies. In particular, six key threats made our list.

Duo's Security Blog
JUNE 27, 2023
is the latest iteration of this type of malware, and it differs from its predecessors in several ways, first and foremost in scale. According to the 2022 Verizon Data Breach Investigations Report, ransomware has increased by 13% over the previous year — a jump greater than the last five years combined. Ransomware 3.0

Security Boulevard
JULY 7, 2022
This lack of visibility and oversight can leave your organization exposed to attacks by cybercriminals, who take advantage of the vulnerabilities of this valuable trust mechanism to slip their malware into software that appears to be legitimate. Read our free eBook! "> Off. Related Posts. Cybercriminals are more creative than ever.

Webroot
FEBRUARY 10, 2022
Install reputable cybersecurity software – What used to be the main method of defense against malware is now only a single method of defense, but it’s still a critical one. Download our eBook on the Hidden Cost of Ransomware. Interested in learning more about ransomware and its effects on businesses?

Webroot
FEBRUARY 11, 2021
These documents will ask users to enable an embedded macro that then delivers malware, usually in the form of ransomware. Over 90% of malware campaigns used the pandemic in their initial phishing email this past year.

Security Boulevard
JUNE 21, 2022
If your pipeline doesn’t require digital signatures of all artifacts used to build your products, anyone could slip in a malicious change and the automation will incorporate that change and produce a malware-infected executable that you deliver to your customers. Distributing malware in your company’s name. UTM Medium. UTM Source.

Security Boulevard
SEPTEMBER 2, 2022
TLS/SSL bridging adds another layer of security by performing extra checks for malware. Download our Machine Identity Management for dummies eBook to learn more about securing your applications and preventing certificate-related outages. TLS/SSL offloading can also be used to introduce additional security checks for malware.

SiteLock
AUGUST 27, 2021
Creating an eBook is one of the quickest ways to make a digital product. eBook tips: Keep it simple. Use tools like Word, PowerPoint and others to create your eBook PDF. Use tools like Word, PowerPoint and others to create your eBook PDF. Audiobooks: Read a blog post or eBook you’ve written previously. Audio files.

Malwarebytes
AUGUST 9, 2022
Has machine learning (ML) to recognize ‘goodware’ instead of malware. Many EDR vendors will offer EP as a separate offering—usually, these are just file-based scanners looking for possible clues to malware in binary files. Has machine learning (ML) to recognize ‘goodware’ instead of malware.

Security Boulevard
JULY 9, 2024
This makes malware command-and-control, phishing attacks, DNS tunneling and a number of other attacks significantly less effective. These instructions determine how the malware, ransomware or botnets will “act” within and cause damage to an organization.

Security Boulevard
MAY 24, 2022
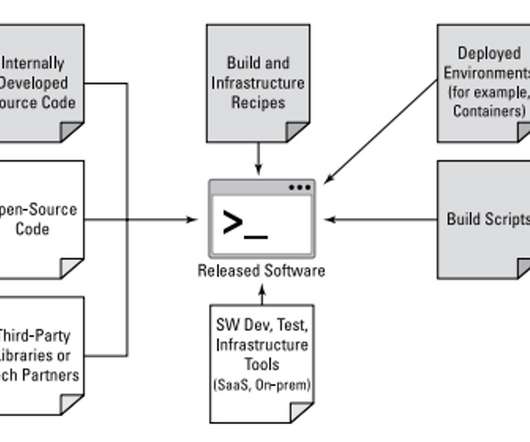
SolarWinds was followed by a similar build-time code-manipulation attack, in which attackers penetrated Codecov product’s software supply chain , manipulating the build process to inject malicious code into its software and using the software update mechanism to distribute the malware to Codecov customers. Related Posts.

Vipre
OCTOBER 25, 2021
Email is the #1 attack vector for SMBs, and serves as a primary starting point for malware, phishing, and other types of attacks. . Potential attackers can exploit endpoints using various forms of malware. For our full step-by-step guide to improving your SMB’s security, download our free ebook here. Endpoints .
Security Boulevard
JUNE 2, 2022
If legitimate software provided by your organization is tampered with—such as malware being added—and then signed with your organization’s legitimate code signing keys, your organization may experience a liability situation from your customers who are the ones who will suffer from that malware attack. Download the eBook to learn more.

Security Boulevard
OCTOBER 2, 2023
For example, attackers may use domain spoofing techniques to create websites that look like legitimate websites, or they may use malware to inject malicious code into legitimate websites. Malware payloads - Malicious attachments or links that install info-stealing malware, ransomware, or remote access Trojans via phishing messages.
Security Boulevard
JULY 25, 2022
If you found malware on the internet signed by your company’s code signing certificate, where would you start looking for the source of the breach? Read our free eBook! "> Off. The more certificates in use, the more organizations find it difficult to obtain the complete visibility needed to track and manage them. UTM Medium.

Cisco Security
AUGUST 10, 2023
We understand that while commodity malware provides significant value from a recovery model focused on the endpoint, targeted attacks require more prescriptive and preventative capabilities. A critical part of our project was learning from real-world ransomware attack cases.

Malwarebytes
OCTOBER 24, 2022
Threat hunting is all about nipping stealthy attackers (and malware) in the bud. That includes SOC work, forensics, malware analysis, and more, each of which Hiep feels has over the years given him a leg-up in the world of threat hunting. Get the eBook : Is MDR right for my business? More MDR resources.
Security Boulevard
AUGUST 16, 2022
An organization with EDR or NDR in place may be protected against up to 90% of classic threats, such as commodity malware. eBook: Five Easy Steps to Replace Your SIEM. Endpoint malware reveals outdated EDR alerting the endpoint security team. Whitepaper: Power to the People - Democratizing Automation & AI-Driven Security.

Duo's Security Blog
MAY 10, 2023
Umbrella also includes threat intelligence, remote browser isolation (RBI) , data loss prevention (DLP) , and cloud malware detection, all while acting as a secure onramp to the internet to provide protection against threats for users anywhere they connect. Trying to understand how to roll out a layered approach to cybersecurity?
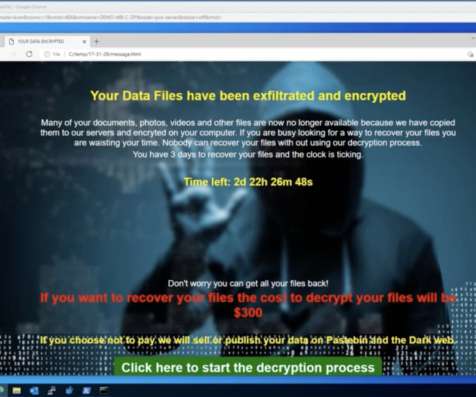
Malwarebytes
JULY 26, 2022
Below, you’ll see the dashboard for Malwarebytes Nebula , our cloud-hosted security operations platform that allows you to manage control of any malware or ransomware incident. Read our eBook on ransomware best practices to detect and block ransomware attacks before they happen. Now, let’s switch to our Nebula console.

Cisco Security
MARCH 4, 2021
Under her guidance, I’ve written about a broad range of cybersecurity topics – from malware to indicators of compromise, from incident response to information security policy, and everything in between. Read Cisco’s eBook, Lifting Each Other Up: A Celebration of Women in Cybersecurity and Their Advocates.

Security Boulevard
MAY 10, 2022
Vulnerabilities, commodity malware, and advanced persistent threats involving machine identities all experienced triple-digit growth during that period, as well. TLS Machine Identity Management for Dummies - the FREE eBook! Broaden the view out to 2015-2020, and that figure rises to 700%. UTM Medium. UTM Source. UTM Campaign.

Threatpost
JUNE 16, 2021
Meanwhile, in a separate survey, 80 percent of organizations that paid the ransom said they were hit by a second attack.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content