ClickFix: How to Infect Your PC in Three Easy Steps
Krebs on Security
MARCH 14, 2025
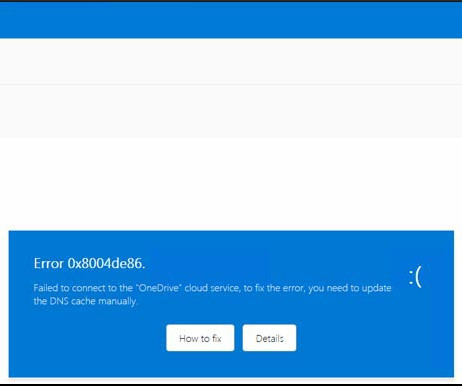
In this scam, dubbed “ ClickFix ,” the visitor to a hacked or malicious website is asked to distinguish themselves from bots by pressing a combination of keyboard keys that causes Microsoft Windows to download password-stealing malware. Executing this series of keypresses prompts Windows to download password-stealing malware.








Let's personalize your content