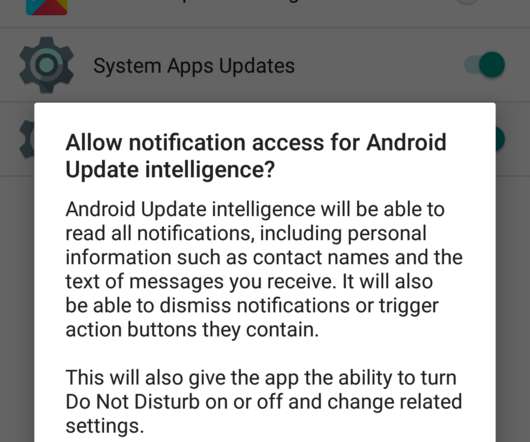
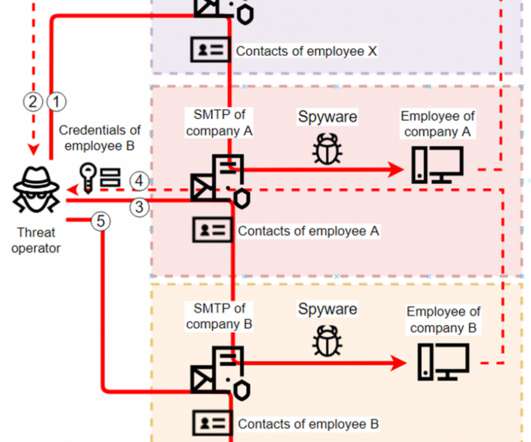
Spyware disguises itself as Zoom downloads
Malwarebytes
SEPTEMBER 29, 2022
It's no surprise then to see criminals continuing to abuse Zoom's popularity, in the hope of netting interested parties and, potentially, luring current users into downloading and installing malware. Malware @Zoom downloads ? Findings reveal six fake Zoom download sites, but they are no longer accessible.












































Let's personalize your content