IoT Unravelled Part 2: IP Addresses, Network, Zigbee, Custom Firmware and Soldering
Troy Hunt
NOVEMBER 23, 2020
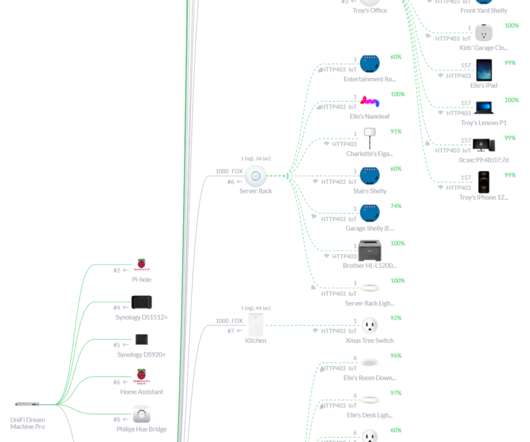
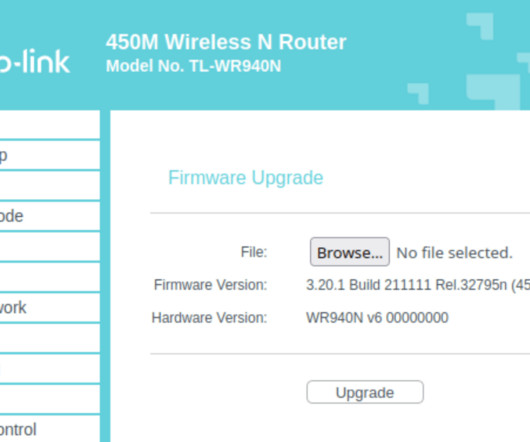
Let's drill into all that and then go deeper into custom firmware and soldering too. I can easily block a device from talking to the internet, throttle its connection, see which online services it's communicating with and access a whole host of other information about it. Why is this so hard?!











































Let's personalize your content