Hardening Your VPN
Schneier on Security
SEPTEMBER 30, 2021
The NSA and CISA have released a document on how to harden your VPN.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 30, 2021
The NSA and CISA have released a document on how to harden your VPN.

Krebs on Security
MAY 6, 2024
Virtual private networking (VPN) companies market their services as a way to prevent anyone from snooping on your Internet usage. ” The feature being abused here is known as DHCP option 121 , and it allows a DHCP server to set a route on the VPN user’s system that is more specific than those used by most VPNs. .”
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
APRIL 3, 2025
That’s according to a report from the non-profit Tech Transparency Project (TTP), who investigated the top 100 mobile VPN apps downloaded from Apple’s App Store as documented by mobile intelligence company AppMagic. Mobile VPNs are apps that connect your smartphone to the internet via different computers around the world.

Security Affairs
OCTOBER 25, 2024
is a Denial of Service (DoS) issue that impacts the Remote Access VPN (RAVPN) service of ASA and FTD. An attacker could exploit this vulnerability by sending a large number of VPN authentication requests to an affected device. Services that are not related to VPN are not affected.” continues the advisory.

Schneier on Security
JULY 15, 2020
The NSA's Central Security Service -- that's the part that's supposed to work on defense -- has released two documents (a full and an abridged version) on securing virtual private networks. Maintaining a secure VPN tunnel can be complex and requires regular maintenance. patches) for VPN gateways and clients.

Krebs on Security
FEBRUARY 19, 2020
It is perhaps best known for selling virtual private networking (VPN) software that lets users remotely access networks and computers over an encrypted connection. Iranian hackers recently have been blamed for hacking VPN servers around the world in a bid to plant backdoors in large corporate networks.

Krebs on Security
AUGUST 21, 2020
The advisory came less than 24 hours after KrebsOnSecurity published an in-depth look at a crime group offering a service that people can hire to steal VPN credentials and other sensitive data from employees working remotely during the Coronavirus pandemic. authenticate the phone call before sensitive information can be discussed.

Security Affairs
SEPTEMBER 29, 2021
CISA and the NSA agencies have published guidance for securely using virtual private network (VPN) solutions. Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) have released guidance for increasing the security of virtual private network (VPN) solutions.
Security Affairs
JUNE 15, 2020
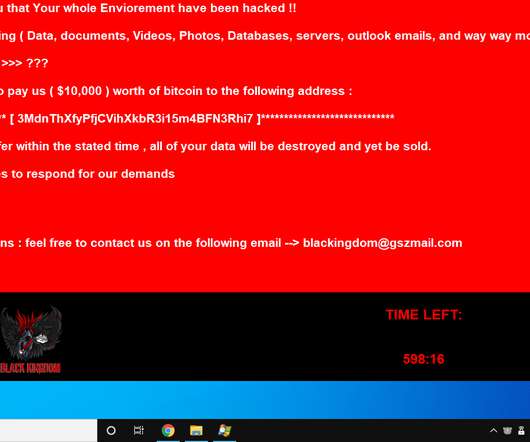
Black Kingdom ransomware operators are targeting organizations using unpatched Pulse Secure VPN software to deploy their malware. the malicious code encrypts files and appends the.DEMON extension to filenames of the encrypted documents. Black Kingdom ransomware was first spotted in late February by security researcher GrujaRS.

Security Affairs
JUNE 17, 2021
Iran-linked Ferocious Kitten APT group used instant messaging apps and VPN software like Telegram and Psiphon to deliver Windows RAT and spy on targets’ devices. ” Kaspersky spotted the activity of the group by investigating two weaponized documents that were uploaded to VirusTotal in July 2020 and March 2021. .

Krebs on Security
NOVEMBER 21, 2020
In due course, the malicious actor was able to partially compromise our infrastructure, and gain access to document storage.” The phishers often will explain that they’re calling from the employer’s IT department to help troubleshoot issues with the company’s email or virtual private networking (VPN) technology.

Heimadal Security
SEPTEMBER 29, 2021
Cybersecurity and Infrastructure Security Agency (CISA) have issued guidance for strengthening the security of virtual private network (VPN) services. The post NSA and CISA Release Security Tips Regarding VPN Security appeared first on Heimdal Security Blog.
Krebs on Security
MAY 28, 2024
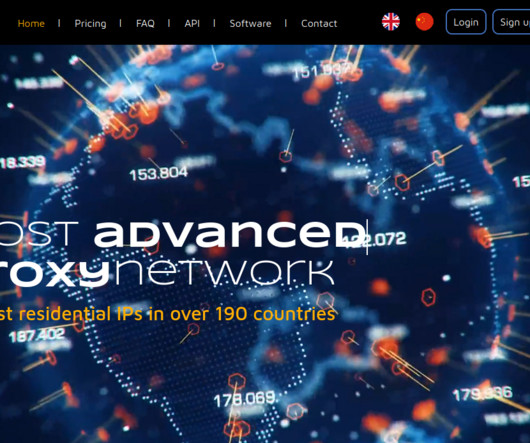
911 built its proxy network mainly by offering “free” virtual private networking (VPN) services. 911’s VPN performed largely as advertised for the user — allowing them to surf the web anonymously — but it also quietly turned the user’s computer into a traffic relay for paying 911 S5 customers.
Security Affairs
JANUARY 16, 2024
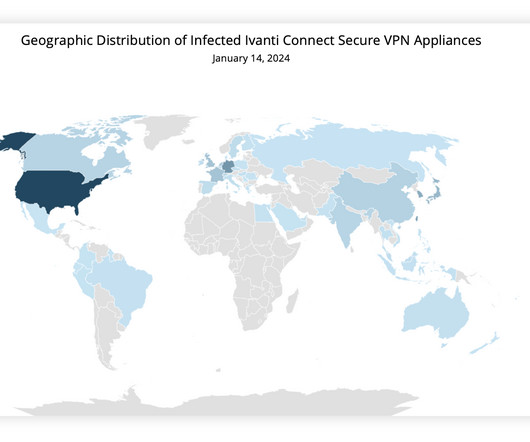
Experts warn that recently disclosed Ivanti Connect Secure VPN and Policy Secure vulnerabilities are massively exploited in the wild. Through forensic analysis of the memory sample, Volexity was able to recreate two proof-of-concept exploits that allowed full unauthenticated command execution on the ICS VPN appliance.

CyberSecurity Insiders
JUNE 6, 2023
The nation is known to plant its employees in other countries by fabricating false documents, allowing them to initiate and profit from their malicious digital campaigns. In a separate news development, cybersecurity researcher Jeremiah Fowler recently discovered a significant data breach related to the database of a Free VPN service.
Krebs on Security
JUNE 7, 2021
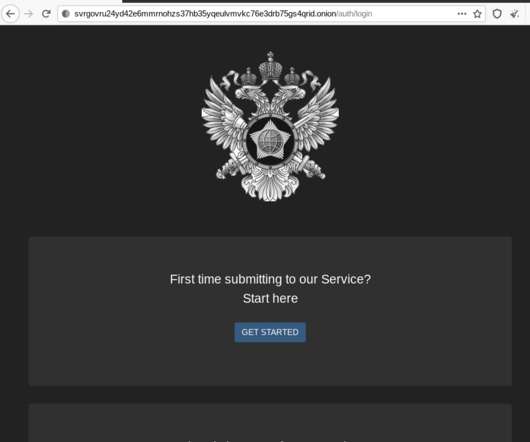
In the process of doing so, I encountered a small snag: The FSB’s website said in order to communicate with them securely, I needed to download and install an encryption and virtual private networking (VPN) appliance that is flagged by at least 20 antivirus products as malware. The FSB headquarters at Lubyanka Square, Moscow.

Schneier on Security
SEPTEMBER 17, 2018
A 2006 document from the Snowden archives outlines successful NSA operations against "a number of "high potential" virtual private networks, including those of media organization Al Jazeera, the Iraqi military and internet service organizations, and a number of airline reservation systems.".

Krebs on Security
NOVEMBER 17, 2021
But shortly after Spamhaus began blocking Micfo’s IP address ranges, Micfo shifted gears and began reselling IP addresses mainly to companies marketing “virtual private networking” or VPN services that help customers hide their real IP addresses online.

Krebs on Security
SEPTEMBER 17, 2020
Charging documents say the seven men are part of a hacking group known variously as “ APT41 ,” “ Barium ,” “ Winnti ,” “ Wicked Panda ,” and “ Wicked Spider.” One of the alleged hackers was first profiled here in 2012 as the owner of a Chinese antivirus firm. Image: FBI.

eSecurity Planet
MARCH 12, 2025
IPVanish and NordVPN are VPN solutions that offer customers multiple pricing options, a mobile VPN, and various privacy features. IPVanish is an affordable VPN with multiple support channels, including phone. Ive compared both VPNs, including their plans and features, to help you decide which is better for you.

Krebs on Security
OCTOBER 8, 2020
If the attachment is opened, the malicious document proceeds to quietly download additional malware and hacking tools to the victim machine ( here’s one video example of a malicious Microsoft Office attachment from the malware sandbox service any.run ). .” ” WHO IS DR. SAMUIL?

Adam Levin
JUNE 24, 2020
Among the hundreds of thousands of documents are police and FBI reports, bulletins, guides and more,” DDoSecrets announced on its Twitter feed (Twitter has since banned the DDoSecrets account). Included in the data set are emails, audio, video, scanned documents, bulletins, guide, and police and FBI reports.
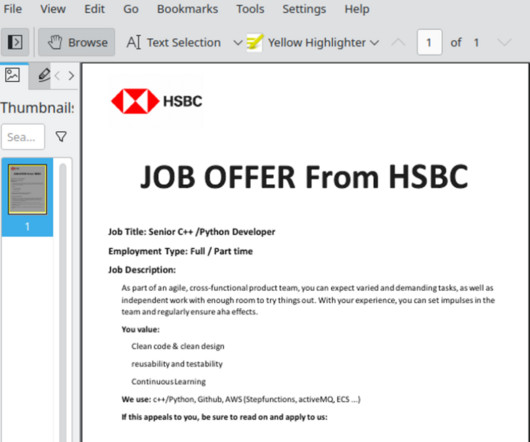
Krebs on Security
APRIL 20, 2023
Mandiant found the earliest evidence of compromise uncovered within 3CX’s network was through the VPN using the employee’s corporate credentials, two days after the employee’s personal computer was compromised. The malware was found inside of a document that offered an employment contract at the multinational bank HSBC.

Security Affairs
NOVEMBER 2, 2024
The first documented attack against a Sophos facility is the one that targeted Cyberoam in 2018. Attackers maintained persistence through VPN credentials, Active Directory DCSYNC access, and firmware-hooking methods to survive updates.

eSecurity Planet
OCTOBER 1, 2021
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have released guidance and best practices for securing virtual private network (VPN) solutions. What might be most striking about the document is how many security steps and solutions it takes to properly secure VPN connections.

Malwarebytes
NOVEMBER 6, 2024
Very important files and documents can be encrypted or stored in password protected folders to keep them safe from prying eyes. Use a firewall and VPN A firewall protects an entry point to a network while a VPN creates an encrypted tunnel between two networks.

Security Affairs
MARCH 29, 2024
Cisco warns customers of password-spraying attacks that have been targeting Remote Access VPN (RAVPN) services of Cisco Secure Firewall devices. Cisco is warning customers of password-spraying attacks that have been targeting Remote Access VPN (RAVPN) services configured on Cisco Secure Firewall devices. ” reads the report.
Security Boulevard
MARCH 31, 2025
Privacy Without Compromise: Proton VPN is Now Built Into Vivaldi Vivaldi Vivaldi integrates ProtonVPN natively into its desktop version of its browser. Proton Drive and Docs now support collaboration with users without Proton accounts Proton Proton users can now collaborate on documents with anyone -- including those without Proton accounts.
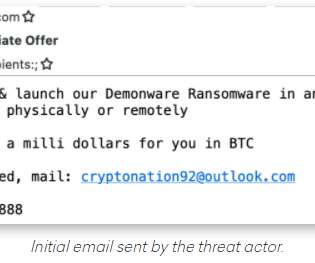
Krebs on Security
AUGUST 19, 2021
Abnormal Security documented how it tied the email back to a young man in Nigeria who acknowledged he was trying to save up money to help fund a new social network he is building called Sociogram. “You can provide us accounting data for the access to any company, for example, login and password to RDP, VPN, corporate email, etc.

The Hacker News
JULY 29, 2022
These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others. All these apps in question have been

Malwarebytes
JANUARY 7, 2022
In order to distribute the RAT onto victims, Patchwork lures them with documents impersonating Pakistani authorities. For example, a document called EOIForm.rtf was uploaded by the threat actor onto their own server at karachidha[.]org/docs/. Figure 4: Malicious document triggers exploit. Figure 10: Threat actor uses VPN-S.
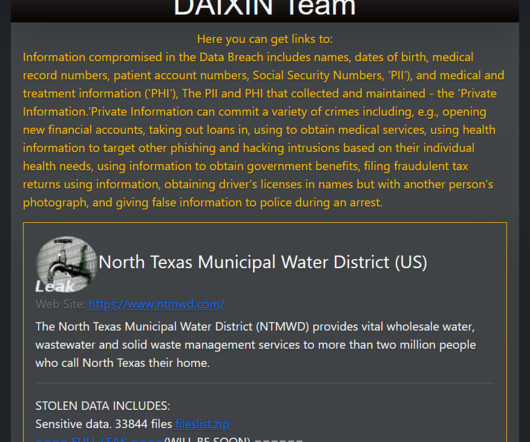
Security Affairs
NOVEMBER 28, 2023
The ransomware gang claims the theft of board meeting minutes, internal project documentation, personnel details, audit reports, and more. The Daixin Team group gains initial access to victims through virtual private network (VPN) servers. The threat actors obtained the VPN credentials through phishing attacks.

Security Affairs
APRIL 2, 2020
Microsoft is sending notifications to dozens of hospitals about vulnerable VPN devices and gateways exposed online in their network. Microsoft is warning dozens of hospitals of the risks of ransomware attacks due to insecure VPN devices and gateways exposed online. ” reads the post published by Microsoft.
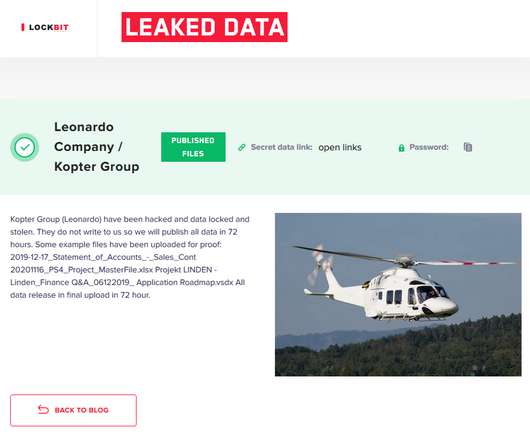
Security Affairs
DECEMBER 6, 2020
The files published by the ransomware gang on the leak site include internal projects, business documents, and various aerospace and defense industry standards. LockBit ransomware operators told ZDNet that they have accessed the network of the helicopter maker via a VPN appliance that was poorly protected. Source ZDNet.

eSecurity Planet
NOVEMBER 12, 2024
Aside from antivirus, Norton offers ransomware and hacking protection, privacy monitoring, and a VPN. Even McAfee’s most basic plan includes a VPN, identity monitoring, and text scam detection. McAfee Essential offers web browsing protection, VPN, and identity monitoring. 5 Pricing: 3.7/5 5 Core features: 3.5/5 5 Pricing: 4.7/5

Webroot
MARCH 3, 2025
Document disposal Shred sensitive documents. Practice personal Information management Data minimization strategies Provide the least number of private details necessary when filling out forms or answering questionnaires. Social media privacy Avoid sharing personal information on social media.

eSecurity Planet
SEPTEMBER 26, 2024
Surfshark and ExpressVPN are both popular VPNs for individuals and home office setups. Surfshark is a highly affordable solution with many useful features for basic and advanced VPN needs. 5 SurfShark is a VPN solution offering multiple privacy and security features besides private networking. month • SurfShark One: $3.39/month

Security Affairs
FEBRUARY 16, 2024
The government experts conducted an incident response assessment of the state government organization after its documents were posted on the dark web. CISA and MS-ISAC assessed that the threat actor connected to the VM through the victim’s VPN with the intent to blend in with legitimate traffic to evade detection.”

Security Affairs
JUNE 19, 2021
North Korea-linked APT group Kimsuky allegedly breached South Korea’s atomic research agency KAERI by exploiting a VPN vulnerability. A KAERI spokesperson revealed that threat actors exploited a vulnerability in a virtual private network (VPN) server to gain access to the network of the institute. ” reported The Record.

Joseph Steinberg
JULY 17, 2023
Among the leaked data were briefings on domestic US terrorism marked “For Official Use Only,” a global counter-terrorism assessment document with the words “Not Releasable to the Public or Foreign Governments” on its cover, crew lists for ships, and maps and photos of military bases. ML,” the domain for Mali, instead of the U.S.

SecureWorld News
NOVEMBER 27, 2024
Back up files If you haven't backed up the data on your devices, like photos, documents or other files, do so before heading on vacation. Instead, use a virtual private network (VPN) or your phone as a personal hotspot to surf more securely. Updates often include tweaks that protect you against the latest cybersecurity concerns.

eSecurity Planet
SEPTEMBER 5, 2024
A VPN (Virtual Private Network) routes your internet traffic through an encrypted tunnel, shielding your data from hackers and ensuring your online activities remain private and secure. A VPN can provide the solution if you want to safeguard your personal information, bypass geo-restrictions, or maintain anonymity online.

eSecurity Planet
FEBRUARY 17, 2025
Visit Microsoft Defender Pros & Cons Pros Cons Free Limited advanced features Integration with windows No VPN feature Automatic updates Only supports Windows Key Features Real-time threat protection: Microsoft Defender actively monitors your system for viruses, malware, and other threats. It supports Windows OS only. 5 Pricing: 4.7/5

Webroot
OCTOBER 22, 2021
The user can access their company’s files and documents as if they were physically present at their office. The most popular options include virtual private network (VPN) or remote desktop protocol (RDP). VPN works by initiating a secure connection over the internet through data encryption. Document your procedures.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content