Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware
The Hacker News
DECEMBER 22, 2023
A new phishing campaign is leveraging decoy Microsoft Word documents as bait to deliver a backdoor written in the Nim programming language.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

The Hacker News
DECEMBER 22, 2023
A new phishing campaign is leveraging decoy Microsoft Word documents as bait to deliver a backdoor written in the Nim programming language.
Security Affairs
DECEMBER 29, 2023
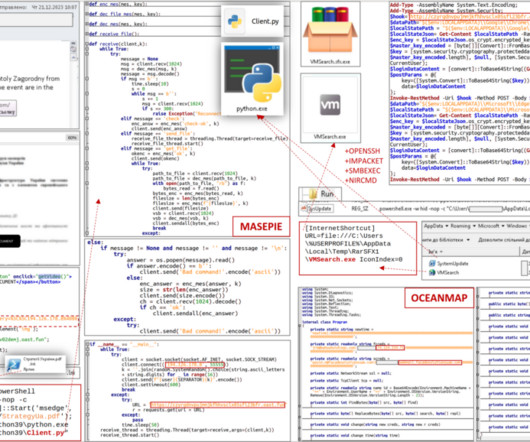
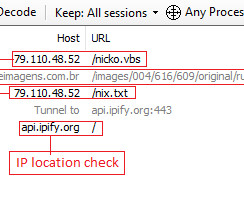
Ukraine’s CERT (CERT-UA) warned of a new phishing campaign by the APT28 group to deploy previously undocumented malware strains. The group employed previously undetected malware such as OCEANMAP, MASEPIE, and STEELHOOK to steal sensitive information from target networks. file classified as MASEPIE.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
NOVEMBER 24, 2023
North Korea-linked Konni APT group used Russian-language Microsoft Word documents to deliver malware. FortiGuard Labs researchers observed the North Korea-linked Konni APT group using a weaponized Russian-language Word document in an ongoing phishing campaign. The Word document seems to be in the Russian language.

Schneier on Security
FEBRUARY 7, 2023
Criminals using Google search ads to deliver malware isn’t new, but Ars Technica declared that the problem has become much worse recently. The surge is coming from numerous malware families, including AuroraStealer, IcedID, Meta Stealer, RedLine Stealer, Vidar, Formbook, and XLoader.

Security Affairs
NOVEMBER 7, 2024
SentinelLabs observed North Korea-linked threat actor BlueNoroff targeting businesses in the crypto industry with a new multi-stage malware. SentinelLabs researchers identified a North Korea-linked threat actor targeting crypto businesses with new macOS malware as part of a campaign tracked as “Hidden Risk.”
The Hacker News
FEBRUARY 3, 2023
In a continuing sign that threat actors are adapting well to a post-macro world, it has emerged that the use of Microsoft OneNote documents to deliver malware via phishing attacks is on the rise.

CyberSecurity Insiders
MAY 11, 2023
Intro In February 2022, Microsoft disabled VBA macros on documents due to their frequent use as a malware distribution method. This move prompted malware authors to seek out new ways to distribute their payloads, resulting in an increase in the use of other infection vectors, such as password-encrypted zip files and ISO files.
Krebs on Security
FEBRUARY 28, 2024
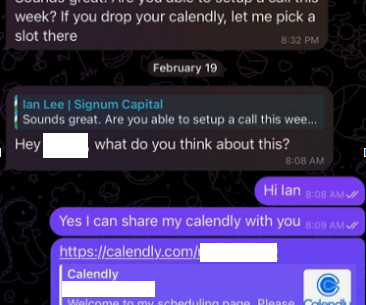
But clicking the meeting link provided by the scammers prompts the user to run a script that quietly installs malware on macOS systems. It didn’t dawn on Doug until days later that the missed meeting with Mr. Lee might have been a malware attack. ” Image: SlowMist.

Security Affairs
JULY 30, 2024
The domains and documents employed in the campaign as part of the first stage of the attack suggest threat actors are targeting of Pakistan, Egypt and Sri Lanka. In recent campaign, the threat actors used meticulously crafted documents that appear to be legitimate and familiar to the target.

Krebs on Security
MAY 22, 2019
Some of the most convincing email phishing and malware attacks come disguised as nastygrams from a law firm. Here’s a look at a recent spam campaign that peppered more than 100,000 business email addresses with fake legal threats harboring malware. Please download and read the attached encrypted document carefully.
Security Affairs
DECEMBER 21, 2023
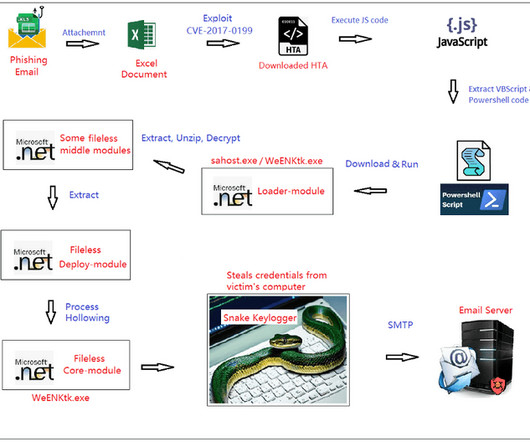
Threat actors are exploiting an old Microsoft Office vulnerability, tracked as CVE-2017-11882, to spread the Agent Tesla malware. Threat actors are exploiting an old Microsoft Office vulnerability, tracked as CVE-2017-11882 (CVSS score: 7.8), as part of phishing campaigns to spread the Agent Tesla malware.

Tech Republic Security
APRIL 29, 2020
Application Guard for Office and Safe Documents will make phishing attacks harder and the Office experience better for users, starting with Office 365 Pro Plus and E5 licences.

The Hacker News
JUNE 21, 2024
Cybersecurity researchers have shed light on a new phishing campaign that has been identified as targeting people in Pakistan using a custom backdoor. Dubbed PHANTOM#SPIKE by Securonix, the unknown threat actors behind the activity have leveraged military-related phishing documents to activate the infection sequence.
Penetration Testing
AUGUST 29, 2024
Fortinet’s FortiGuard Labs has unearthed a new variant of the notorious Snake Keylogger, delivered through a malicious Excel document in a phishing campaign. This keylogger, also known as “404 Keylogger”... The post New Snake Keylogger Variant Slithers Into Phishing Campaigns appeared first on Cybersecurity News.
Krebs on Security
AUGUST 17, 2023
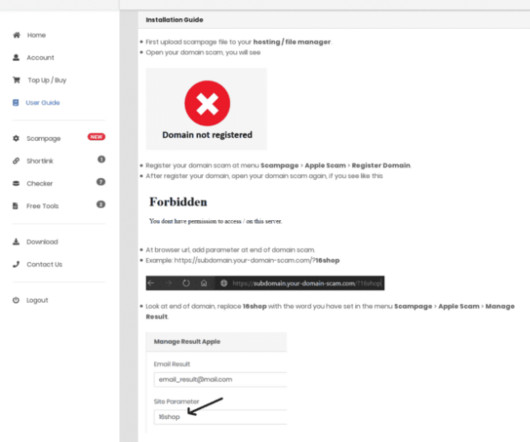
You’ve probably never heard of “ 16Shop ,” but there’s a good chance someone using it has tried to phish you. A 16Shop phishing page spoofing Apple and targeting Japanese users. 16Shop documentation instructing operators on how to deploy the kit. Image: Akamai.com. Image: Akamai. Image: ZeroFox.
Security Affairs
AUGUST 21, 2024
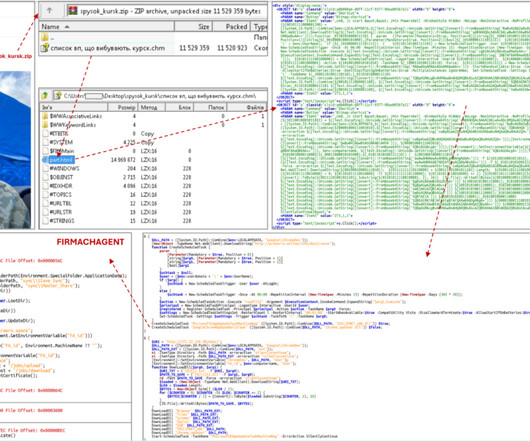
The Computer Emergency Response Team of Ukraine (CERT-UA) warned of new phishing attacks, carried out by the Vermin group, distributing a malware. The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign conducted by the Vermin group that distributed malware.

Centraleyes
NOVEMBER 7, 2024
Fake copyright infringement notices are sweeping across inboxes globally, hitting hundreds of companies with a new and devious malware campaign. But instead of legal documents, victims are met with a decoy and a hidden malware file.
Krebs on Security
FEBRUARY 8, 2021
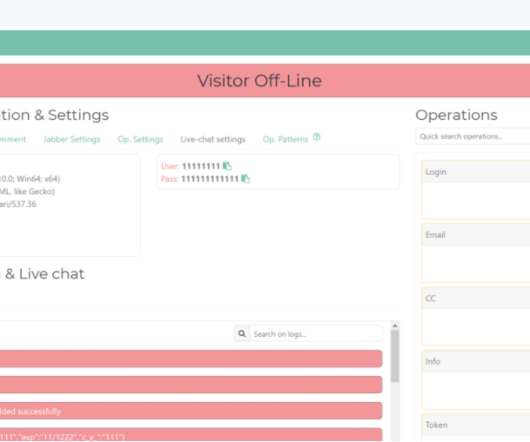
Cyber cops in Ukraine carried out an arrest and several raids last week in connection with the author of a U-Admin , a software package used to administer what’s being called “one of the world’s largest phishing services.” The U-Admin phishing panel interface. Image: fr3d.hk/blog. ” U-Admin, a.k.a.

Bleeping Computer
AUGUST 30, 2022
Threat analysts have spotted a new malware campaign dubbed 'GO#WEBBFUSCATOR' that relies on phishing emails, malicious documents, and space images from the James Webb telescope to spread malware. [.].
Security Affairs
APRIL 17, 2020
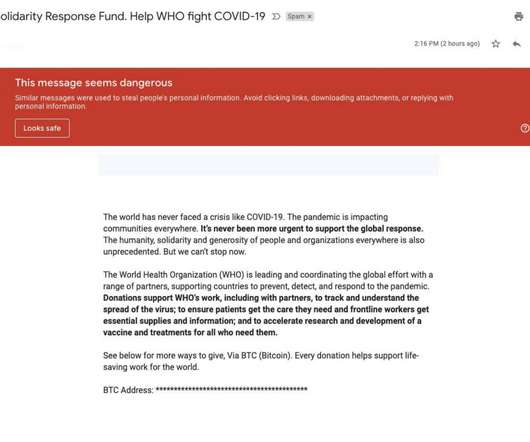
Google says that the Gmail malware scanners have blocked around 18 million phishing and malware emails using COVID-19 lures in just one week. “Every day, Gmail blocks more than 100 million phishing emails. During the last week, we saw 18 million daily malware and phishing emails related to COVID-19.

The Hacker News
JANUARY 18, 2024
The Russia-linked threat actor known as COLDRIVER has been observed evolving its tradecraft to go beyond credential harvesting to deliver its first-ever custom malware written in the Rust programming language. The lures are

Security Affairs
MAY 26, 2024
The government experts reported that the group carried out at least two massive campaigns since May 20, threat actors aimed at distributing SmokeLoader malware via email. “Starting from May 20th, hackers have launched at least two massive campaigns with emails containing the SmokeLoader malware.”

Security Affairs
SEPTEMBER 25, 2023
A phishing campaign targets Ukrainian military entities using drone manuals as lures to deliver the post-exploitation toolkit Merlin. Securonix researchers recently uncovered a phishing campaign using a Pilot-in-Command (PIC) Drone manual document as a lure to deliver a toolkit dubbed Merlin. ” concludes the report.

Bleeping Computer
AUGUST 23, 2021
A clever UPS phishing campaign utilized an XSS vulnerability in UPS.com to push fake and malicious 'Invoice' Word documents. [.].

Security Affairs
MAY 13, 2024
Experts reported that since April, the Phorpiex botnet sent millions of phishing emails to spread LockBit Black ransomware. Subject lines included “your document” and “photo of you???”. Endpoint Security : Install endpoint security solutions to fortify defenses against malware attacks. 177 and 185[.]215[.]113[.]66.
Security Affairs
NOVEMBER 18, 2020
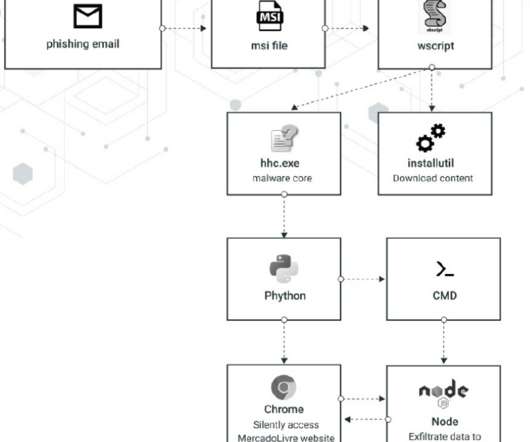
Experts from Cybereason Nocturnus uncovered an active campaign that targets users of a large e-commerce platform in Latin America with Chaes malware. Experts at Cybereason Nocturnus have uncovered an active campaign targeting the users of a large e-commerce platform in Latin America with malware tracked as Chaes.
eSecurity Planet
OCTOBER 4, 2022
Malicious programs or malware are common and dangerous threats in the digital space for both individual users and organizations alike. German IT-Security Institute AV-TEST has recorded over 1 billion malicious programs as of this writing, with over 450,000 new instances of malware being recorded every day. Malvertising.

Bleeping Computer
DECEMBER 13, 2021
A new variant of the Agent Tesla malware has been spotted in an ongoing phishing campaign that relies on Microsoft PowerPoint documents laced with malicious macro code. [.].
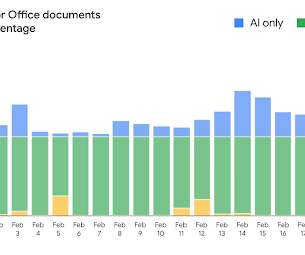
Security Affairs
FEBRUARY 27, 2020
Google announced that the new scanning capabilities implemented in Gmail have increased the detection rate of malicious documents. The figures revealed by Google are awesome, the company declared that its malware scanner processes more than 300 billion attachments each week. SecurityAffairs – Gmail, malware).
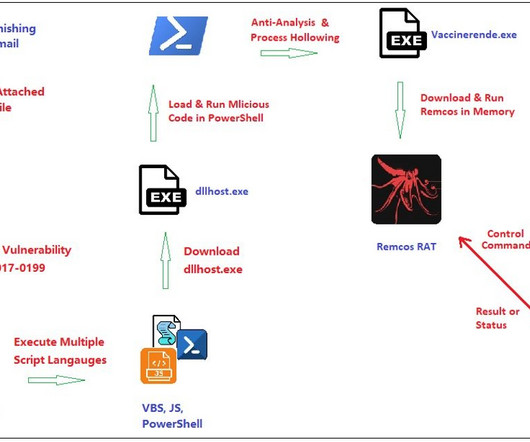
Security Affairs
NOVEMBER 11, 2024
Fortinet researchers discovered a new phishing campaign spreading a variant of the commercial malware Remcos RAT. Fortinet’s FortiGuard Labs recently uncovered a phishing campaign spreading a new variant of the Remcos RAT. Upon opening the file, the RCE vulnerability CVE-2017-0199 is exploited.

Heimadal Security
JULY 15, 2022
Researchers have uncovered a new phishing kit that, under the guise of security controls, injects malware into legitimate WordPress sites and uses a fake PayPal-branded social engineering scam to trick targets into handing over their most sensitive data. This data includes government documents, photos, and even financial information.

Adam Levin
JUNE 12, 2020
and global protests of the killing of George Floyd are being used to spread malware according to the cybersecurity non-profit organization abuse.ch. . The Zurich-based group identified a phishing campaign that capitalizes on the Black Lives Matter movement to distribute malware. The documented by Abuse.ch

Security Boulevard
DECEMBER 4, 2023
In the ever-evolving landscape of cybersecurity, a recent discovery sheds light on a new phishing attack being dubbed the Konni malware. Identifying The Konni […] The post Konni Malware Alert: Uncovering The Russian-Language Threat appeared first on TuxCare.

Malwarebytes
MARCH 22, 2023
Opening the attachment up reveals a Word document called W-9 form.doc This file’s size is 548,164 KB (548 MB), which is very suspicious. You won’t find many genuine Word documents weighing in at 500MB or more. Opening the document quickly becomes a game of Macro-related risk. This is no exception. File early.
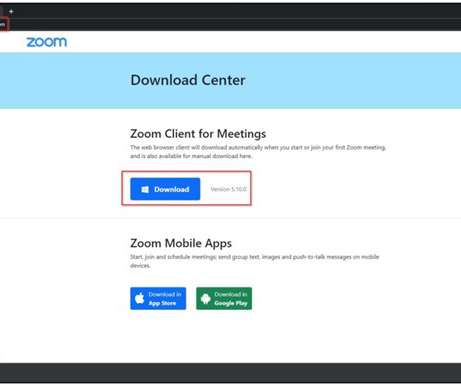
Security Affairs
JANUARY 7, 2023
Cyber researchers warn of a modified Zoom app that was used by threat actors in a phishing campaign to deliver the IcedID Malware. Cyble researchers recently uncovered a phishing campaign targeting users of the popular video conferencing and online meeting platform Zoom to deliver the IcedID malware. Pierluigi Paganini.

The Hacker News
DECEMBER 20, 2023
Attackers are weaponizing an old Microsoft Office vulnerability as part of phishing campaigns to distribute a strain of malware called Agent Tesla.

Malwarebytes
AUGUST 18, 2021
Phishing scammers love well known brand names, because people trust them, and their email designs are easy to rip off. DocuSign is a service that allows people to sign documents in the Cloud. DocuSign is a service that allows people to sign documents in the Cloud. Signing documents electronically saves a lot of paper and time.
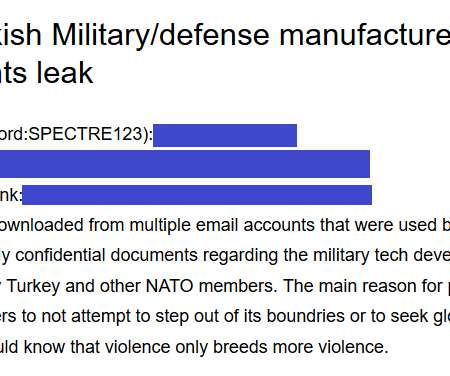
Security Affairs
OCTOBER 12, 2020
Security experts from Cyble found alleged sensitive documents of NATO and Turkey, is it a case of cyber hacktivism or cyber espionage? The post Researchers found alleged sensitive documents of NATO and Turkey appeared first on Security Affairs. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.
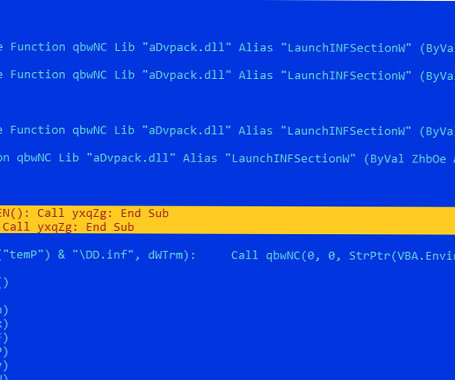
The Hacker News
JULY 17, 2023
Microsoft Word documents exploiting known remote code execution flaws are being used as phishing lures to drop malware called LokiBot on compromised systems. LokiBot, also known as Loki PWS, has been a well-known information-stealing Trojan active since 2015," Fortinet FortiGuard Labs researcher Cara Lin said. "It

SecureList
JUNE 28, 2023
Introduction Andariel, a part of the notorious Lazarus group, is known for its use of the DTrack malware and Maui ransomware in mid-2022. Their campaign introduced several new malware families, such as YamaBot and MagicRat, but also updated versions of NukeSped and, of course, DTrack.
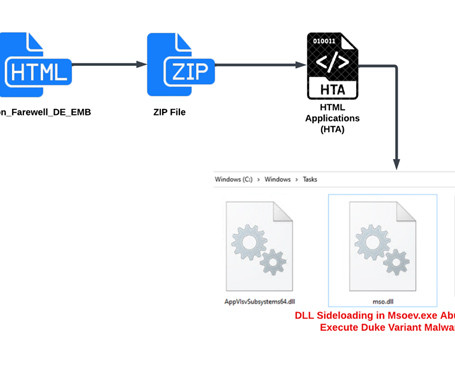
The Hacker News
AUGUST 17, 2023
The phishing attacks feature PDF documents with diplomatic lures, some of which are disguised as coming from Germany, to deliver a variant of a malware called Duke, which has been attributed to APT29 (aka BlueBravo, Cloaked Ursa, Cozy Bear, Iron Hemlock,
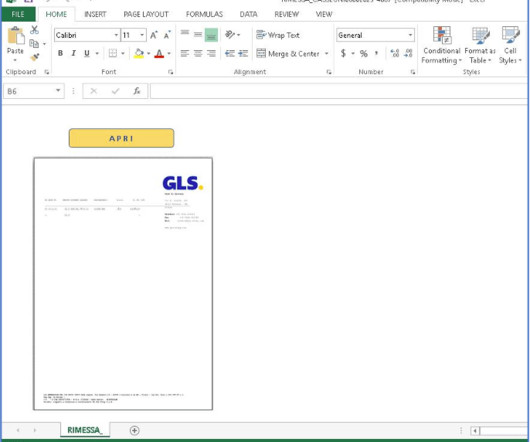
Security Affairs
AUGUST 1, 2023
Threat actors are targeting Italian organizations with a phishing campaign aimed at delivering a new malware called WikiLoader. WikiLoader is a new piece of malware that is employed in a phishing campaign that is targeting Italian organizations. ” reads the post published by Proofpoint. ” continues the report.

Malwarebytes
JULY 19, 2022
This data includes identification documents, spreadsheets related to Roblox creators, and various email addresses. At time of writing, there’s no specifics with regard to the “identification documents” This could mean driving licence, passport, employee ID scan…we simply don’t know at the moment.

Bleeping Computer
JUNE 7, 2022
A previously unknown malware loader named SVCReady has been discovered in phishing attacks, featuring an unusual way of loading the malware from Word documents onto compromised machines. [.].
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content