Yet Another IoT Cybersecurity Document
Schneier on Security
SEPTEMBER 27, 2018
This one is from NIST: " Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks." It's still in draft. Remember, there are many others.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 27, 2018
This one is from NIST: " Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks." It's still in draft. Remember, there are many others.

Troy Hunt
NOVEMBER 25, 2020
In part 1 of this series, I posited that the IoT landscape is an absolute mess but Home Assistant (HA) does an admirable job of tying it all together. As with the rest of the IoT landscape, there's a lot of scope for improvement here and also just like the other IoT posts, it gets very complex for normal people very quickly.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
JUNE 25, 2020
New research: " Best Practices for IoT Security: What Does That Even Mean? " We consider categories of best practices, and how they apply over the lifecycle of IoT devices. Back in 2017, I catalogued nineteen security and privacy guideline documents for the Internet of Things. by Christopher Bellman and Paul C.

Krebs on Security
APRIL 26, 2019
iLnkP2p is bundled with millions of Internet of Things (IoT) devices, including security cameras and Webcams, baby monitors, smart doorbells, and digital video recorders. He found that 39 percent of the vulnerable IoT things were in China; another 19 percent are located in Europe; seven percent of them are in use in the United States.

eSecurity Planet
JANUARY 22, 2021
billion Internet of Things (IoT) devices. As more information about IoT device vulnerabilities is published, the pressure on industry and government authorities to enhance security standards might be reaching a tipping point. government, standards will not apply to the IoT market at-large. Implications for IoT devices.

Adam Shostack
JANUARY 2, 2025
[no description provided] Jean Camp and Yoshi Kohno are organizing an interesting workshop upcoming at the University of Washington on " Best Practices In The IoT :" Our agenda begins with a presentation on the Federal Government initiatives in the IoT.

SecureWorld News
OCTOBER 31, 2024
Spooky fact : The infamous Mirai botnet attack in 2016 turned more than 600,000 IoT devices into cyber zombies, leading to one of the most significant DDoS attacks in history. Warding off zombies : Regularly update device firmware, patch IoT devices, and monitor for unusual traffic patterns.

Hacker's King
NOVEMBER 2, 2024
You probably know about Netcat a Swiss Army Knife for networking pen-testing tool for hackers and cybersecurity experts, but what if you get something like that for Internet Of Things (IoT) devices to test their security before an actual hacker does. Specific modules for the technology to be audited. sudo python3 homePwn.py

eSecurity Planet
AUGUST 9, 2021
A malicious advertising campaign originating out of Eastern Europe and operating since at least mid-June is targeting Internet of Things (IoT) devices connected to home networks, according to executives with GeoEdge, which offers ad security and quality solutions to online and mobile advertisers. Malvertising is Evolving.

SecureWorld News
DECEMBER 23, 2024
Manufacturing systems, especially the ones that work with SCADA technology (Supervisory Control and Data Acquisition), IoT devices, and other critical technologies, depend heavily on efficient IT support to ensure that the downtime is minimal, and the performance is optimal.

SecureList
SEPTEMBER 21, 2023
IoT devices (routers, cameras, NAS boxes, and smart home components) multiply every year. The first-ever large-scale malware attacks on IoT devices were recorded back in 2008, and their number has only been growing ever since. Telnet, the overwhelmingly popular unencrypted IoT text protocol, is the main target of brute-forcing.
Security Affairs
OCTOBER 13, 2020
The number of sensors and smart devices connected to the internet is exponentially rising, which are the 5 Major Vulnerabilities for IoT devices. If you take a look at the global market for IoT, you can easily spot the trend. IoT devices are exposed to cybersecurity vulnerabilities. IoT is a complicated concept.

Troy Hunt
JULY 13, 2021
I've spent more time IoT'ing my house over the last year than any sane person ever should. Plus, it's definitely added to our lives in terms of the things it enables us to do; see them in part 5 of my IoT unravelled blog series. You also want to be able to change the colour because hey, that's kinda cool.

Tech Republic Security
MARCH 8, 2017
The latest batch of WikiLeaks documents reveals something we've always feared: The government has the means to spy on us using our IoT devices. That means anyone else could too.

Security Affairs
MAY 5, 2019
Hacker “Subby” brute-forces the backends of 29 IoT botnets that were using weak or default credentials. A hacker that goes online with the moniker ‘Subby’ took over 29 IoT botnets in the past few week s with brute-force attacks. SecurityAffairs – IoT botnets, hacking). ” continues Subby.

Notice Bored
JUNE 13, 2022
To celebrate the publication of ISO/IEC 27400:2022 today, we have slashed the price for our IoT security policy templates to just $10 each through SecAware.com. IoT policy is the first of the basic security controls shown on the 'risk-control spectrum' diagram above, and is Control-01 in the new standard.
NSTIC
JULY 19, 2021
As part of our ongoing community engagement following the publication of four IoT cybersecurity draft documents in December 2020, NIST conducted a quartet of roundtable discussions in June 2021 focused on draft NISTIR 8259B, IoT Non-Technical Supporting Capability Core Baseline.
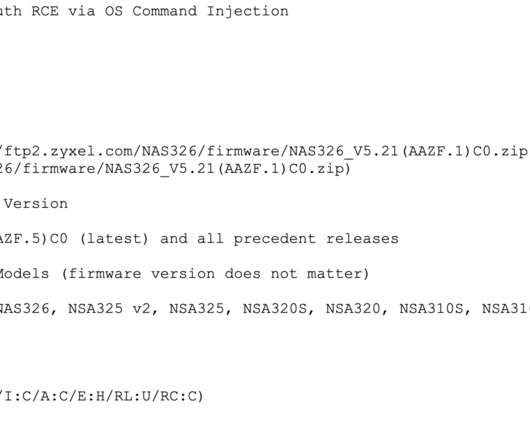
Krebs on Security
FEBRUARY 24, 2020
While in many respects the class of vulnerability addressed in this story is depressingly common among Internet of Things (IoT) devices, the flaw is notable because it has attracted the interest of groups specializing in deploying ransomware at scale. A snippet from the documentation provided by 500mhz for the Zyxel 0day.

CyberSecurity Insiders
NOVEMBER 10, 2021
Internet of Things (IoT) devices are now everywhere. Now, the National Institute of Standards and Technology (NIST) has released new draft guidance documents on securing these devices, both before release, as well as acquisition, and integration. The post The Dawn of True IoT Security appeared first on Cybersecurity Insiders.

SecureList
JULY 6, 2022
Among the various offensive security techniques, vulnerability assessment takes priority when it comes to analyzing the security of IoT/IIoT devices. The vulnerability assessment of IoT/IIoT devices is based on analyzing their firmware.

Security Affairs
SEPTEMBER 4, 2019
Kenneth Currin Schuchman (21) from Vancouver, Washington pleaded guilty to creating and operating multiple DDoS IoT botnet , including Satori. Kenneth Currin Schuchman (21) from Vancouver, Washington, aka Nexus Zeta, pleaded guilty to creating and operating multiple DDoS IoT botnets. Pierluigi Paganini.

SecureWorld News
JUNE 14, 2022
I love the possibilities that Internet of Things (IoT) products bring to our lives. But I'm also very concerned about the associated security and privacy risks that IoT products inherently bring to those using them when controls do not exist or are not used to mitigate the risks. Consider just a few recent statistics.

SecureWorld News
JANUARY 7, 2024
IoT creates a link between systems, computers, and portable devices, allowing them to automatically send information to each other. As a result, IoT must be incorporated into any GRC strategy to protect all devices and systems across the business.

NSTIC
JUNE 22, 2023
NIST’s IoT cybersecurity guidance has long recognized the importance of secure software development (SSDF) practices, highlighted by the NIST IR 8259 series—such as the recommendation for documentation in Action 3.d These development practices can also provide

Trend Micro
JUNE 30, 2021
On June 25, 2021, ETSI released its new IoT Testing Specifications completed by the organization’s committee on Methods for Testing and Specifications.

Adam Shostack
MARCH 5, 2020
Amazon has released a set of documents, “ Updates to Device Security Requirements for Alexa Built-in Products.” More precisely, since I don’t have an Amazon developer account, I’m going to look at the blog post, and infer some stuff about the underlying documentation.). ” That has 13 guidelines.

The Last Watchdog
AUGUST 26, 2024
As our world becomes increasingly interconnected, the security of Operational Technology (OT) and Internet of Things (IoT) devices is more critical than ever. The persistence of known vulnerabilities in these devices raises an important question: why are these issues still present, despite being well-documented?

The Security Ledger
OCTOBER 21, 2021
The post Spotlight: Automation Beckons as DevOps, IoT Drive PKI Explosion appeared first on The Security Ledger with Paul F. Brian Trzupek of DigiCert joins Paul to talk about the findings of a recent State of PKI Automation survey and the challenges of managing fast-growing population of tens of thousands of PKI certificates.

Security Boulevard
JULY 24, 2024
An Incident Response Plan is a document that assists IT and OT security professionals in responding effectively and timely to cyberattacks. Importance of Incident Response Plans in IT, IoT, & OT establishments Technology and automation are woven into our daily lives.

NSTIC
NOVEMBER 21, 2024
In May 2020, NIST published Foundational Cybersecurity Activities for IoT Device Manufacturers (NIST IR 8259), which describes recommended cybersecurity activities that manufacturers should consider performing before their IoT devices are sold to customers.
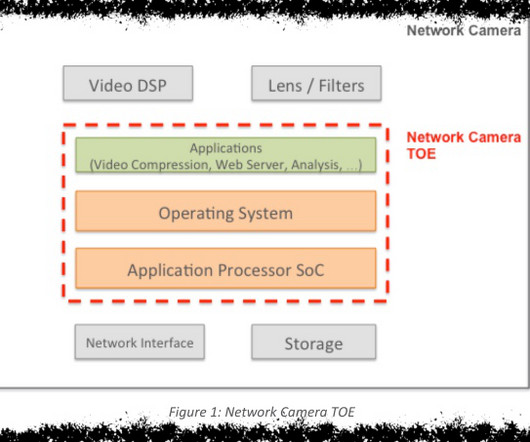
Adam Shostack
JANUARY 2, 2025
The models were created, analyzed and documented by Prove & Run , a French software firm, on contract to Arm. That fundamental nature, of being a Protection Profile, controls the form of the document, and the models within it. We might want to communicate to persuade, to discuss, or to document. Who did this? What is this?

Adam Shostack
JANUARY 2, 2025
Exploring supply chain threat modeling with Alexa Amazon has released a set of documents, " Updates to Device Security Requirements for Alexa Built-in Products." More precisely, since I don't have an Amazon developer account, I'm going to look at the blog post, and infer some stuff about the underlying documentation.)

The Last Watchdog
APRIL 13, 2021
But what about the numerous machines on a company’s network, like mobile devices, servers, applications, and IoT devices? Enterprises should implement email and document signing with certificates to accomplish this. This also reduces the wet-ink hassle of printing and scanning documents while working remotely.

NSTIC
DECEMBER 15, 2020
IoT devices are becoming integral elements of federal information systems, which is why NIST has released for public review draft guidance on defining federal IoT cybersecurity requirements, including supporting non-technical requirements. This figure illustrates the relationships among the documents.

Security Boulevard
JUNE 28, 2022
IoT and Machine Identity Management in Financial Services. How is IoT changing the financial sector? IoT has already positively impacted the financial sector and will only continue to in the future. The most notable and well-documented example of investment in the IoT infrastructure has been by retail banks.

Security Affairs
JANUARY 28, 2025
. “ The cyber-attacks granted attackers unauthorized access to classified information and sensitive data stored within several government ministries, including Economic Affairs and Communications, Social Affairs, and Foreign Affairs leading to the theft of thousands of confidential documents.”
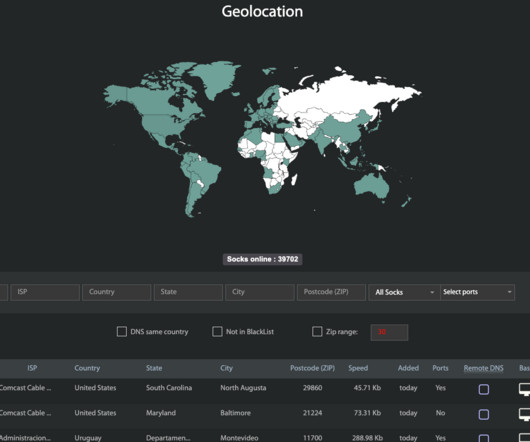
Krebs on Security
APRIL 18, 2023
Kilmer said when Spur first started looking into Faceless, they noticed almost every Internet address that Faceless advertised for rent also showed up in the IoT search engine Shodan.io Those with IoT zero-days could expect payment if their exploit involved at least 5,000 systems that could be identified through Shodan.

eSecurity Planet
FEBRUARY 2, 2024
Within the last couple of months, smart device vulnerabilities have been piling up, prompting businesses to protect their Internet of Things (IoT) environments. While Teslas aren’t the typical business IoT device, their connection to the internet makes them a cyber threat as much as your business’s other IoT technology.

NSTIC
FEBRUARY 4, 2020
Your comments helped strengthen and improve this foundational document for Internet of Things (IoT) device manufacturers, and we’re pleased to announce that the second draft of NISTIR 8259, Recommendations for IoT Device Manufacturers: Foundational Activities and Core Device Cybersecurity Capability Baseline, is now available for public comment.
Security Affairs
FEBRUARY 26, 2024
On February 16th, an account linked to that email uploaded a batch of files including marketing documents, images, screenshots, and a substantial collection of WeChat messages exchanged between I-SOON employees and clients. The alleged data breach revealed the capabilities of the China-linked hacking contractor.

Krebs on Security
JANUARY 14, 2019
Kaye launched the attack using a botnet powered by Mirai , a malware strain that enslaves hacked Internet of Things (IoT) devices like poorly-secured Internet routers and Web-based cameras for use in large-scale cyberattacks. Daniel Kaye , an Israel-U.K. to face charges there.

The Last Watchdog
DECEMBER 13, 2023
Related: Why IoT standards matter Digital Trust refers to the level of confidence both businesses and consumers hold in digital products and services – not just that they are suitably reliable, but also that they are as private and secure as they need to be. Notable progress was made in 2023 in the quest to elevate Digital Trust.

Security Affairs
JUNE 26, 2020
“According to court documents, the botnets were initially based largely on the source code previously developed by other individuals to create the Mirai botnet;” In September 2019, Schuchman pleaded guilty to creating and operating multiple DDoS IoT botnets. .” reads the DoJ.

Centraleyes
DECEMBER 11, 2024
Recent amendments have focused on addressing vulnerabilities linked to digital transformation in aviation, such as the use of cloud technologies and IoT devices. Evolution and Updates: The IATA has regularly updated its guidance to reflect emerging threats, including ransomware, supply chain vulnerabilities, and advanced persistent threats.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content