The Prevalence of DarkComet in Dynamic DNS
Security Boulevard
AUGUST 6, 2024
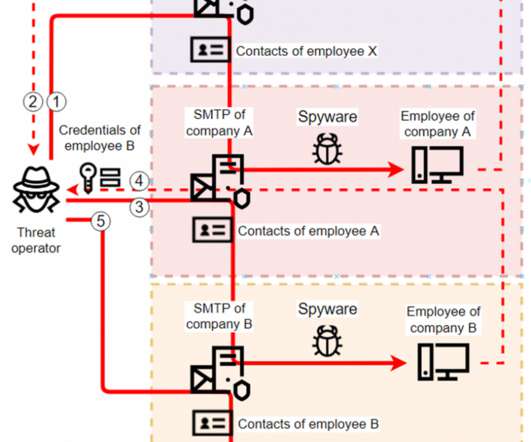
Threat Intelligence Report Date: August 6, 2024 Prepared by: David Brunsdon, Threat Intelligence - Security Engineer, HYAS Dynamic DNS (DDNS) is a service that automatically updates the Domain Name System (DNS) in real-time to reflect changes in the IP addresses of a domain.
















Let's personalize your content