MasterCard DNS Error Went Unnoticed for Years
Krebs on Security
JANUARY 22, 2025
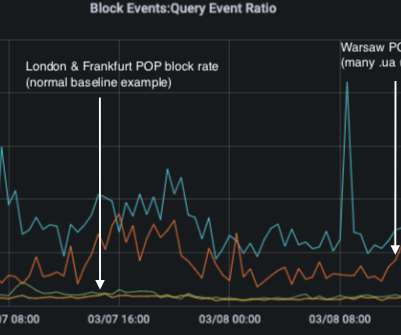
A DNS lookup on the domain az.mastercard.com on Jan. MasterCard.com relies on five shared Domain Name System (DNS) servers at the Internet infrastructure provider Akamai [DNS acts as a kind of Internet phone book, by translating website names to numeric Internet addresses that are easier for computers to manage].


















Let's personalize your content