7 Types of Penetration Testing: Guide to Pentest Methods & Types
eSecurity Planet
JUNE 28, 2023
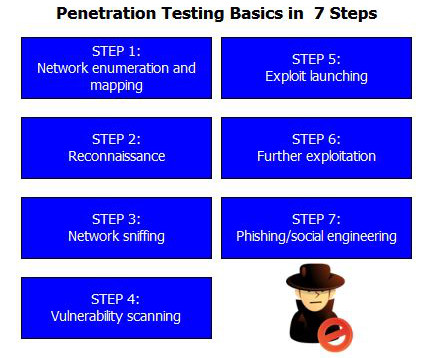
Penetration testers will try to bypass firewalls , test routers, evade intrusion detection and prevention systems ( IPS/IDS ), scan for ports and proxy services, and look for all types of network vulnerabilities. Most cyberattacks today start with social engineering, phishing , or smishing.










Let's personalize your content