Weekly Update 342
Troy Hunt
APRIL 6, 2023
Off the back of the NCA's DDoS market honeypot , the BreachForums admin arrest and the takedown of RaidForums before that , if you're playing in this space you'd have to be looking over your shoulder by now.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Troy Hunt
APRIL 6, 2023
Off the back of the NCA's DDoS market honeypot , the BreachForums admin arrest and the takedown of RaidForums before that , if you're playing in this space you'd have to be looking over your shoulder by now.

Heimadal Security
NOVEMBER 7, 2023
In the wrong hands, medical data can be used for a variety of crimes, such as patient identity theft, clinician identity theft, extortion, tax fraud, insurance fraud, and more.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Security Guru
JANUARY 30, 2025
This can lead to identity theft and major financial losses. DDoS (Distributed Denial of Service) Attacks A DDoS attack happens when hackers flood a platforms servers with enough traffic to cause the platform to crash.

CSO Magazine
JANUARY 24, 2023
Industry respondents also expressed concerns over identity theft at 4%, unavailable or unaffordable cyber insurance at 4%, geopolitical risks at 3%, DDoS attacks at 2% and website defacement at 0.9%, according to CSI’s annual survey of the financial sector.

Thales Cloud Protection & Licensing
OCTOBER 16, 2024
To make matters worse, geopolitical tensions are driving a dramatic increase in Distributed Denial of Service (DDoS) attacks. In its 2024 DDoS Threat Landscape Report , Imperva revealed a 111% increase in the attacks it mitigated from H1 2023 to 2024. Individuals risk identity theft, financial loss, and privacy violations.

Security Affairs
FEBRUARY 11, 2024
Now Cybersecurity expert says the next generation of identity theft is here: ‘Identity hijacking’ Were 3 Million Toothbrushes Really Used for a DDoS Attack? Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, newsletter)

Security Affairs
DECEMBER 19, 2023
As a result, there’s an elevated risk of sensitive information being stolen and misused for activities such as identity theft, fraud, or sale on the dark web. Cybercriminals could use the API to obtain more personal information and carry out identity theft and other fraudulent acts.

Malwarebytes
JANUARY 18, 2022
Such details can also be resold for cash, used in identity theft or the making of a synthetic identity, or used to further cash out cryptocurrencies gained from other online crimes. Then in November 2021, Cannazon , the largest marketplace for buying marijuana-based products, shut after a DDoS attack.

SecureWorld News
OCTOBER 26, 2023
Viking Line: The shipping company, like many across Europe, was the target of a DDoS attack that crippled websites and has IT teams working triple-time to get systems back online. This data can be used by cybercriminals to commit fraud or identity theft. This data can be used by criminals to commit identity theft or fraud.

eSecurity Planet
SEPTEMBER 13, 2024
From personal information like Social Security numbers and addresses to sensitive financial details, banks store a treasure trove of data that, if compromised, can lead to identity theft, fraud, and significant financial loss for individuals. Cyber security plays a crucial role in safeguarding this information from unauthorized access.
Security Affairs
JUNE 15, 2022
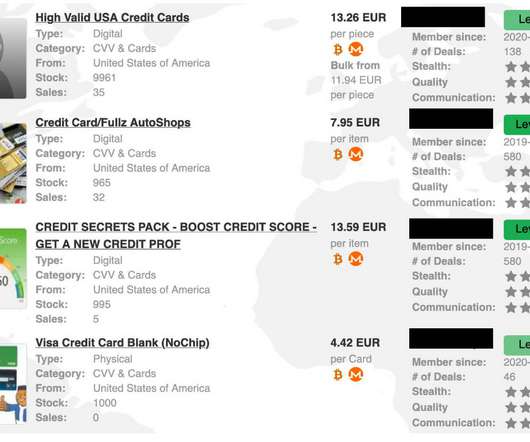
These documents could be used to conduct scams and identity theft. Dark Web Index 2022 also lists malware infections and DDoS attacks. This year’s version of the report also includes Forged Documents (Physical), below is the price list: Product Avg. Price USD (2021) Avg. Additional details are included in the report.

Security Affairs
NOVEMBER 15, 2023
Source: Cybernews The information exposed in this data leak could have been exploited for fraud, identity theft, phishing attempts, or as a source of data for meticulously targeted cyberattacks. Storing personal information in logs should be avoided, as it elevates their sensitivity level. User security log.

CyberSecurity Insiders
SEPTEMBER 13, 2021
The disruption wasn’t limited to just the banking institutions as several websites were badly hit by a DDoS attack on September 8th,2021 that includes NZ meteorological offices, NZ post offices and NZ Police. Kiwibank customers were the first to tweet their anger over the digital disruption on Wednesday last week.

SecureWorld News
NOVEMBER 12, 2020
Distributed Denial of Service (DDoS). Identity Theft. Physical Manipulation, Damage, Theft and Loss. First, however, let's look at the top 15 cyber threats organizations face right now, according to the report: Malware. Web-based Attacks. Web Application Attacks. Data Breach. Insider Threat. Information Leakage.

Security Boulevard
OCTOBER 16, 2024
To make matters worse, geopolitical tensions are driving a dramatic increase in Distributed Denial of Service (DDoS) attacks. In its 2024 DDoS Threat Landscape Report , Imperva revealed a 111% increase in the attacks it mitigated from H1 2023 to 2024. Individuals risk identity theft, financial loss, and privacy violations.

eSecurity Planet
FEBRUARY 4, 2022
Scheduled scans Encryption Identity theft protection. WAFs have to be able to quickly filter the traffic and make decisions on whether to allow each packet, especially when it comes to attackers attempting a DDoS attack. DDoS protection Challenge tests Honeypots for bad bots. Best Antivirus Protection for Consumers.

SecureWorld News
JUNE 7, 2024
DDoS attacks can overwhelm websites and disrupt services. Cybercriminals focus on financial gain through activities like ransomware and identity theft. Ransomware is a type of malware that encrypts data and demands payment for its release. It's hard to know who's behind cyberattacks, which makes the situation more complex.

SecureWorld News
SEPTEMBER 12, 2024
DDoS Attacks: Distributed Denial of Service attacks can cripple gambling sites, causing downtime and loss of revenue. The risks are also pretty obvious: Identity Theft: Personal and financial data can be compromised if a gambling site is breached. This makes them prime targets for cybercriminals.

SiteLock
AUGUST 27, 2021
With database access, thieves can use the data to commit fraud, blackmail, extortion, identity theft and to turn a quick profit by selling it to other criminals on the dark web. Distributed denial of service (DDoS) prevention: Tools that protect the site from crashing under the strain of DDoS attacks.

eSecurity Planet
JULY 28, 2021
DDoS: Overwhelming the Network. In the age-old denial of service (DDoS) attack, a fleet of attacker devices can overwhelm an organization’s web server, thus blocking access to legitimate users. Securing edge devices with identity authentication. Mitigating risk of false key propagation and identity theft.
Security Boulevard
OCTOBER 16, 2023
AI-enabled security protection layers are needed to handle the expected growth of AI-enabled email phishing attacks, DDoS attacks, and identity theft. Gone are the rooms full of human security engineers and IT ops people processing log files and security telemetry.

eSecurity Planet
FEBRUARY 13, 2023
Also read: Database Security: 7 Best Practices & Tips Use better and unique passwords to protect your data from breaches, reduce identity theft, and better protect sensitive and personal information. Threats such as SQL injection and cross-site scripting ( XSS ) attacks can be minimized with techniques such as input sanitization.

eSecurity Planet
AUGUST 13, 2021
This includes Active Directory for identity and access management, Windows Defender, Azure cloud security services such as Security Center, Key Vault, Azure DDoS Protection, Azure Information Protection and Application Gateway for protecting Web applications. Imperva (WAF, database security, threat intelligence, DDoS ).

CyberSecurity Insiders
JUNE 1, 2023
Financial institutions face a range of cybersecurity threats, including phishing attacks, malware, ransomware, and denial of service ( DDoS ) attacks. These threats can result in the theft of sensitive customer data (PII), financial fraud, and reputational damage. Sometimes theft of PII can lead to identity theft too.

The Last Watchdog
FEBRUARY 28, 2021
From mining cryptocurrency to launching DDoS attacks against networks, there are countless ways in which malware can access and utilize victim’s computers and data. They can be used to launch spam emails and distributed denial of service (DDoS) attacks, leveraging hundreds of thousands of compromised computers. Warning signs.

CyberSecurity Insiders
FEBRUARY 2, 2022
Cybercrime costs approximately $600 billion per year, accounting for over 1% of global GDP, as per The Center for Strategic and International Studies (CSIS), and 300,562,519 people were affected by publicly disclosed security breaches the previous year, as per the Identity Theft Resource Center. Exploitation. System failure.

CyberSecurity Insiders
JANUARY 31, 2021
From mining cryptocurrency to launching DDoS attacks against networks, there are countless ways in which malware can access and utilize victim’s computers and data. They can be used to launch spam emails and distributed denial of service (DDoS) attacks, leveraging hundreds of thousands of compromised computers.

Identity IQ
APRIL 29, 2021
In most cases, however, malware is about profiting from data theft by: Stealing consumer credit card information and other financial data. Tricking a target into providing sensitive information for identity theft. Gaining control of multiple computers to launch denial-of-service (DDoS) attacks against other networks.

Cytelligence
FEBRUARY 27, 2023
While the dark web has many legitimate uses, such as providing a platform for political dissidents and whistleblowers to share information safely, it is also a breeding ground for illegal activities such as drug trafficking, hacking, and identity theft. As a result, it poses a significant threat to consumers and businesses alike.

SecureWorld News
MAY 13, 2020
"Here is how we (CSN) define cybercrime: the kind of crime that is only happening because the internet exists [such as ransomware and DDoS attacks]. The other choice of crime is enhanced by the internet, like identity theft and credit card fraud," Judge said. How significant is cybercrime? What is the human side of cybercrime?

IT Security Guru
JANUARY 26, 2024
A data breach could result in the disclosure of this information to hackers who may then commit identity theft, fraud or other illicit activities. Further, knowledge of the nature of cyber threats to which the system is vulnerable, such as malware, phishing or DDoS attacks are necessary for designing appropriate countermeasures.

Graham Cluley
MAY 1, 2024
The UK Government takes aim at IoT devices shipping with weak or default passwords, an identity thief spends two years in jail after being mistaken for the person who stole his name, and are you au fait with the latest scams?

BH Consulting
JUNE 20, 2023
identity theft following the disclosure of the payslips of all employees of a company. However, as a privacy professional, how much do you know about distributed denial of service (DDOS) attacks and how to prevent them, detect them or respond to them? How much do you know about disaster recovery and business continuity?

Spinone
NOVEMBER 1, 2019
DDoS (denial-of-service attack) – a type of a cyber attack which makes the site user wants to visit unusable by flooding it with malicious traffic. Account Hijacking – a type of identity theft, when a hacker hacks and steals someone’s account to perform malicious actions.

Digital Shadows
DECEMBER 16, 2024
The actor leveraged a malicious website that impersonated CloudFlare, a widely used distributed denial of service (DDoS) protection platform, to enhance the attack’s credibility. This stolen data is often sold on underground markets, leading to identity theft, financial fraud, and initial acess into enterprise networks.

The Last Watchdog
MARCH 3, 2022
million IoT devices (predominately IP security cameras with default settings) to launch some of the largest and most disruptive distributed denial of service (DDoS) attacks of all time. According to the Identity Theft Resource Center, ransomware attacks doubled in 2020 and again in 2021. A New Wave of Attacks.
Security Affairs
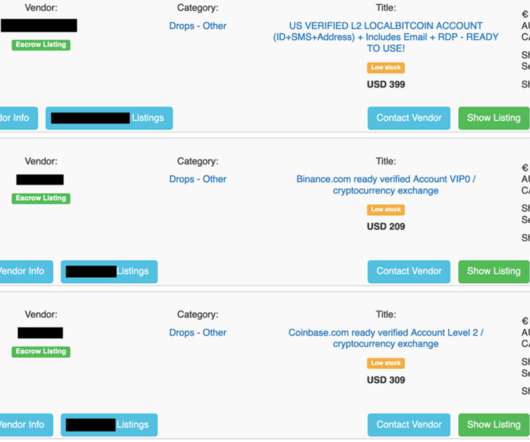
JUNE 4, 2021
And there are even more specialized products such as DDoS attacks, email databases, and malware. DDoS Attacks. Preventing Identity Theft. The New York one is four times more expensive. Passports and IDs from different American states and European countries are on offer as well. Keeping yourself safe is not rocket science.

SiteLock
AUGUST 27, 2021
And as stated by a Harris Poll conducted in 2018 , more than 60 million Americans are affected by identity theft every year. Although new threats are being created every day, most successful hacks are variations on old themes, like the DDoS attacks that are as old as the internet itself. Learn from the past.

Herjavec Group
AUGUST 26, 2021
2000 — Mafiaboy — 15-year-old Michael Calce, aka MafiaBoy, a Canadian high school student, unleashes a DDoS attack on several high-profile commercial websites including Amazon, CNN, eBay and Yahoo! The DDoS attack is part of a political activist movement against the church called “Project Chanology.” billion dollars in damages.

Security Affairs
OCTOBER 31, 2018
” The availability of such kind of data exposes voters to sophisticated identity theft. “Some of the hackers and hacking teams “offer to target government entities for the purposes of database manipulation, economic/corporate espionage, DDoS attacks, and botnet rentals.” states the report.

Adam Levin
DECEMBER 27, 2019
The hackers who brought you Hillary’s emails and who probably have President Trump’s tax returns are going to target operational systems with an array of tactics that include ransomware and more DDoS attacks that will snarl things up in ways we’ve not yet seen. The cloud will leak.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content