Great Firewall Ready to Unleash ‘Gigantic’ DDoS—so are Other Middleboxes
Security Boulevard
AUGUST 19, 2021
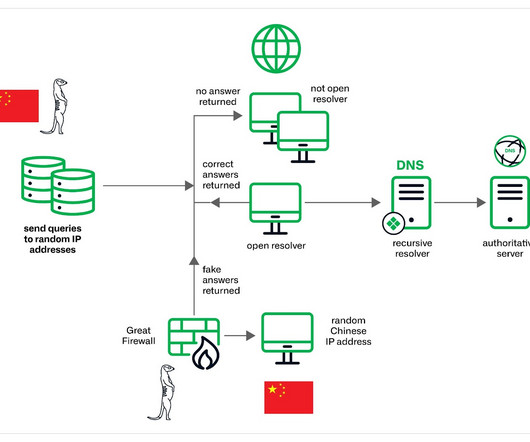
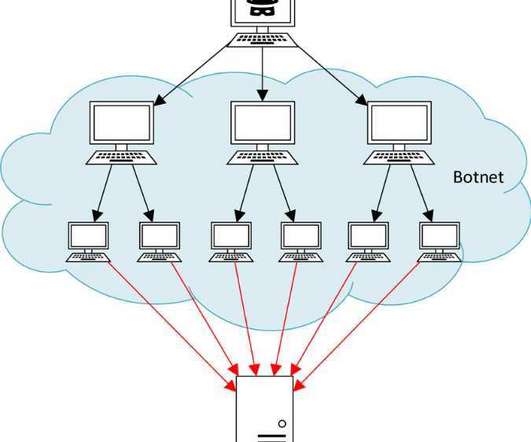
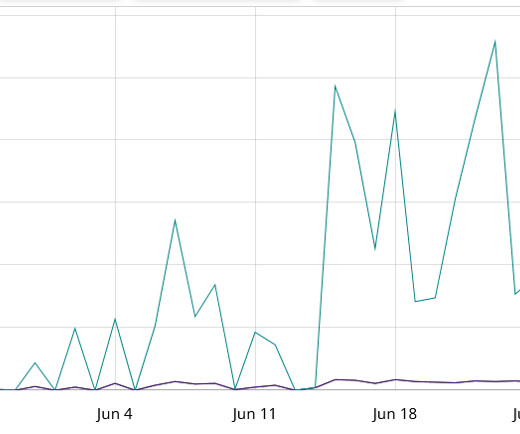
The post Great Firewall Ready to Unleash ‘Gigantic’ DDoS—so are Other Middleboxes appeared first on Security Boulevard. Researchers have disclosed a nasty new way for bad people to mess up the internet for the rest of us.








































Let's personalize your content