Private AI For All: Our End-To-End Approach to AI Privacy on Android
Google Security
AUGUST 13, 2024
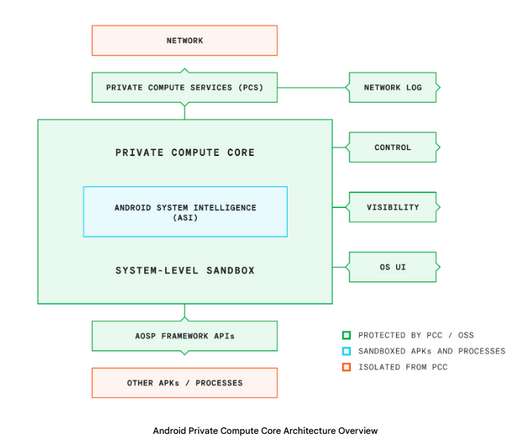
As a pioneer in responsible AI and cutting-edge privacy technologies like Private Compute Core and federated learning , we made sure our approach to the assistant experience with Gemini on Android is aligned with our existing Secure AI framework , AI Principles and Privacy Principles. Pioneering new privacy technologies.












Let's personalize your content