The Business Value of the Social-Engineer Phishing Service
Security Boulevard
JUNE 18, 2021
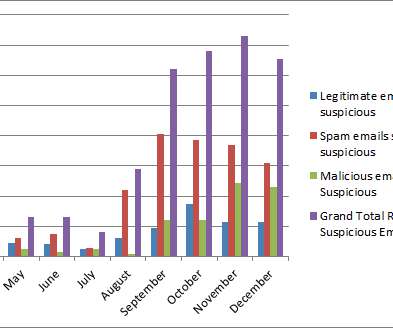
The post The Business Value of the Social-Engineer Phishing Service appeared first on Security Boulevard. Phishing attacks continue to plague organizations across the globe with great success, but why? Cybercriminals are targeting the human element of organizations. Additionally, they are developing techniques to use an.
















































Let's personalize your content