Online Businesses Often Steal And Exploit Customer Data Collected During Cancelled Transactions
Joseph Steinberg
JANUARY 18, 2024
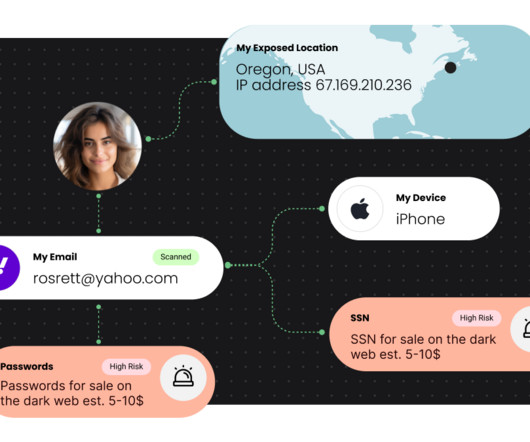
Over the past year I have experimented to see how various retailers handle personal information that they collect from customers, especially when such information is collected as part of a purchase made by the customer in what appears, at first glance, to be some “amazing deal.”










































Let's personalize your content